Khac-Hoang Ngo
MATTER: Multiscale Attention for Registration Error Regression
Sep 16, 2025

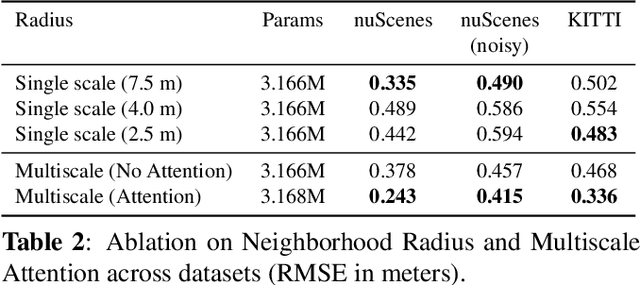

Abstract:Point cloud registration (PCR) is crucial for many downstream tasks, such as simultaneous localization and mapping (SLAM) and object tracking. This makes detecting and quantifying registration misalignment, i.e.,~{\it PCR quality validation}, an important task. All existing methods treat validation as a classification task, aiming to assign the PCR quality to a few classes. In this work, we instead use regression for PCR validation, allowing for a more fine-grained quantification of the registration quality. We also extend previously used misalignment-related features by using multiscale extraction and attention-based aggregation. This leads to accurate and robust registration error estimation on diverse datasets, especially for point clouds with heterogeneous spatial densities. Furthermore, when used to guide a mapping downstream task, our method significantly improves the mapping quality for a given amount of re-registered frames, compared to the state-of-the-art classification-based method.
Practical Bayes-Optimal Membership Inference Attacks
May 30, 2025Abstract:We develop practical and theoretically grounded membership inference attacks (MIAs) against both independent and identically distributed (i.i.d.) data and graph-structured data. Building on the Bayesian decision-theoretic framework of Sablayrolles et al., we derive the Bayes-optimal membership inference rule for node-level MIAs against graph neural networks, addressing key open questions about optimal query strategies in the graph setting. We introduce BASE and G-BASE, computationally efficient approximations of the Bayes-optimal attack. G-BASE achieves superior performance compared to previously proposed classifier-based node-level MIA attacks. BASE, which is also applicable to non-graph data, matches or exceeds the performance of prior state-of-the-art MIAs, such as LiRA and RMIA, at a significantly lower computational cost. Finally, we show that BASE and RMIA are equivalent under a specific hyperparameter setting, providing a principled, Bayes-optimal justification for the RMIA attack.
Breaking the TDD Flow for Over-the-Air Phase Synchronization in Distributed Antenna Systems
Apr 15, 2025Abstract:Phase synchronization between distributed antenna arrays requires measurements that break the standard time-division duplex (TDD) operation. We present a feasibility study on implementing such synchronization and analyze its impact on the quality of service. Considering two antenna arrays with independent local oscillators (LOs), we propose a modified TDD flow to accommodate the transmission of phase synchronization signals, formulate the phase estimation and compensation problem, and derive the achievable downlink spectral efficiency (SE). Numerical results show that frequent re-estimation of the interarray phase disparity is essential for maximizing SE in systems with low-quality LOs. Furthermore, applying a Kalman filter for phase tracking substantially improves the SE, especially if phase estimation errors are large compared to LOs phase drifts.
Sparse Orthogonal Matching Pursuit-based Parameter Estimation for Integrated Sensing and Communications
Mar 04, 2025



Abstract:Accurate parameter estimation such as angle of arrival (AOA) is essential to enhance the performance of integrated sensing and communication (ISAC) in mmWave multiple-input multiple-output (MIMO) systems. This work presents a sensing-aided communication channel estimation mechanism, where the sensing channel shares the same AOA with the uplink communication channel. First, we propose a novel orthogonal matching pursuit (OMP)-based method for coarsely estimating the AOA in a sensing channel, offering improved accuracy compared to conventional methods that rely on rotational invariance techniques. Next, we refine the coarse estimates obtained in the first step by modifying the Space-Alternating Generalized Expectation Maximization algorithm for fine parameter estimation. Through simulations and mathematical analysis, we demonstrate that scenarios with shared AOA achieve a better Cramer-Rao lower bound (CRLB) than those without sharing. This finding highlights the potential of leveraging joint sensing and communication channels to enhance parameter estimation accuracy, particularly in channel or location estimation applications.
Timely Status Updates in Slotted ALOHA Network With Energy Harvesting
Apr 29, 2024Abstract:We investigate the age of information (AoI) in a scenario where energy-harvesting devices send status updates to a gateway following the slotted ALOHA protocol and receive no feedback. We let the devices adjust the transmission probabilities based on their current battery level. Using a Markovian analysis, we derive analytically the average AoI. We further provide an approximate analysis for accurate and easy-to-compute approximations of both the average AoI and the age-violation probability (AVP), i.e., the probability that the AoI exceeds a given threshold. We also analyze the average throughput. Via numerical results, we investigate two baseline strategies: transmit a new update whenever possible to exploit every opportunity to reduce the AoI, and transmit only when sufficient energy is available to increase the chance of successful decoding. The two strategies are beneficial for low and high update-generation rates, respectively. We show that an optimized policy that balances the two strategies outperforms them significantly in terms of both AoI metrics and throughput. Finally, we show the benefit of decoding multiple packets in a slot using successive interference cancellation and adapting the transmission probability based on both the current battery level and the time elapsed since the last transmission.
Secure Aggregation is Not Private Against Membership Inference Attacks
Mar 26, 2024Abstract:Secure aggregation (SecAgg) is a commonly-used privacy-enhancing mechanism in federated learning, affording the server access only to the aggregate of model updates while safeguarding the confidentiality of individual updates. Despite widespread claims regarding SecAgg's privacy-preserving capabilities, a formal analysis of its privacy is lacking, making such presumptions unjustified. In this paper, we delve into the privacy implications of SecAgg by treating it as a local differential privacy (LDP) mechanism for each local update. We design a simple attack wherein an adversarial server seeks to discern which update vector a client submitted, out of two possible ones, in a single training round of federated learning under SecAgg. By conducting privacy auditing, we assess the success probability of this attack and quantify the LDP guarantees provided by SecAgg. Our numerical results unveil that, contrary to prevailing claims, SecAgg offers weak privacy against membership inference attacks even in a single training round. Indeed, it is difficult to hide a local update by adding other independent local updates when the updates are of high dimension. Our findings underscore the imperative for additional privacy-enhancing mechanisms, such as noise injection, in federated learning.
Joint Communications and Sensing Design for Multi-Carrier MIMO Systems
Jun 24, 2023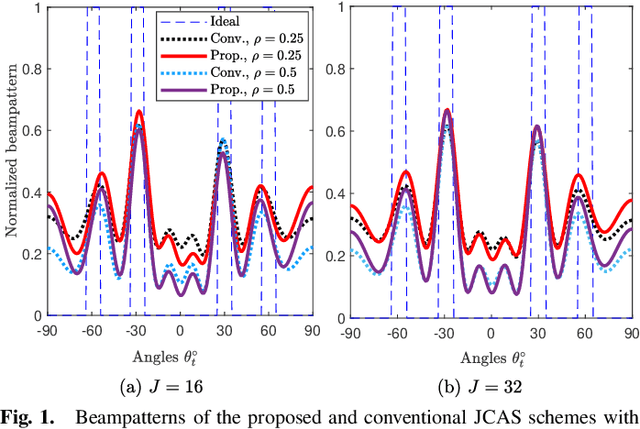
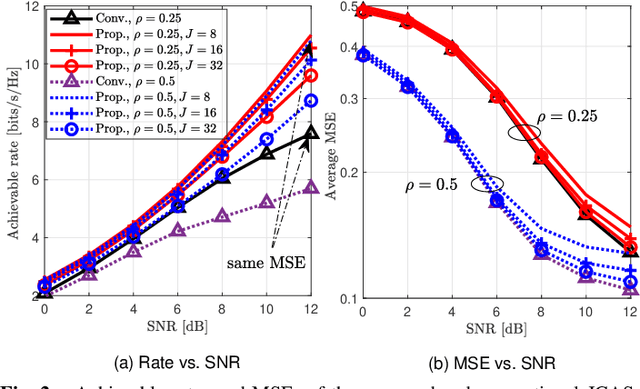
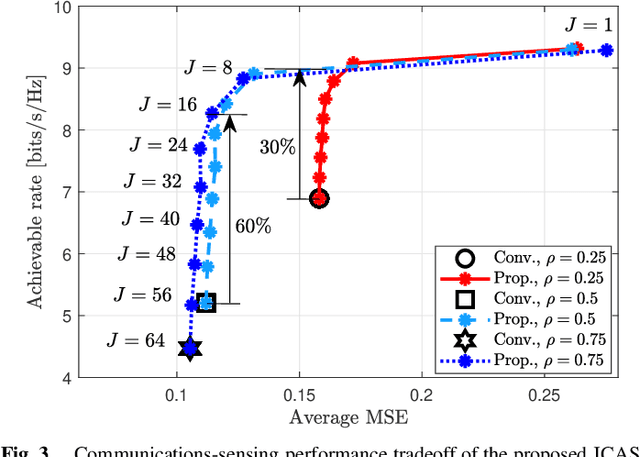
Abstract:In conventional joint communications and sensing (JCAS) designs for multi-carrier multiple-input multiple-output (MIMO) systems, the dual-functional waveforms are often optimized for the whole frequency band, resulting in limited communications--sensing performance tradeoff. To overcome the limitation, we propose employing a subset of subcarriers for JCAS, while the communications function is performed over all the subcarriers. This offers more degrees of freedom to enhance the communications performance under a given sensing accuracy. We first formulate the rate maximization under the sensing accuracy constraint to optimize the beamformers and JCAS subcarriers. The problem is solved via Riemannian manifold optimization and closed-form solutions. Numerical results for an 8x4 MIMO system with 64 subcarriers show that compared to the conventional subcarrier sharing scheme, the proposed scheme employing 16 JCAS subcarriers offers 60% improvement in the achievable communications rate at the signal-to-noise ratio of 10 dB. Meanwhile, this scheme generates the sensing beampattern with the same quality as the conventional JCAS design.
Low-Latency and Secure Computation Offloading Assisted by Hybrid Relay-Reflecting Intelligent Surface
Sep 03, 2021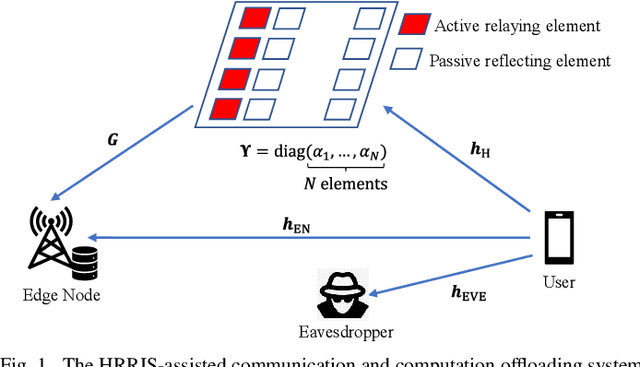
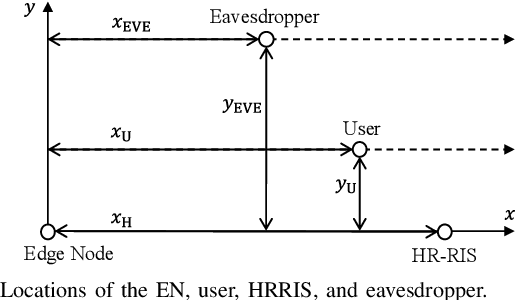
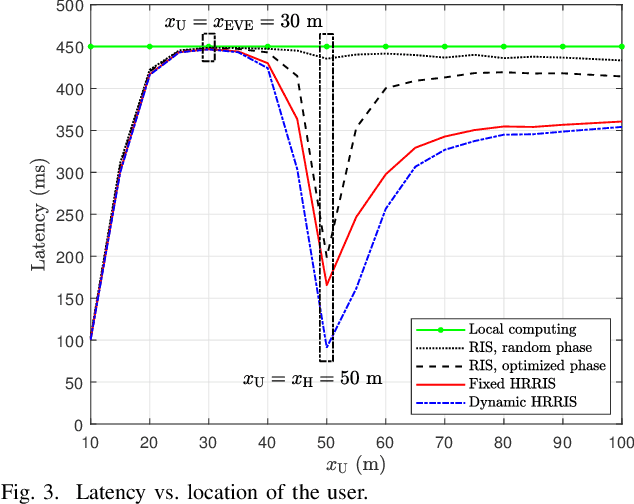
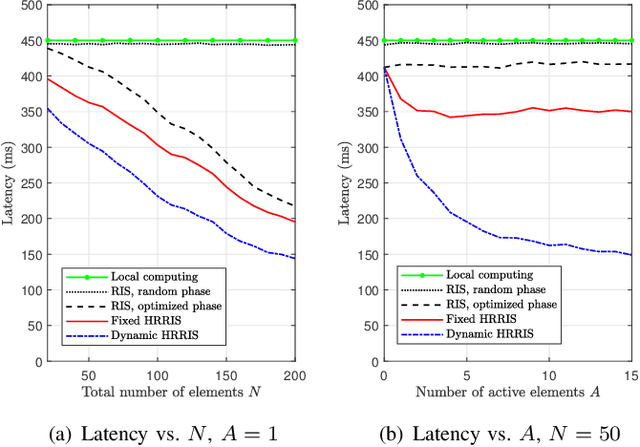
Abstract:Recently, the hybrid relay-reflecting intelligent surface (HRRIS) has been introduced as a spectral- and energy-efficient architecture to assist wireless communication systems. In the HRRIS, a single or few active relay elements are deployed along with a large number of passive reflecting elements, allowing it to not only reflect but also amplify the incident signals. In this work, we investigate the potential of the HRRIS in aiding the computation offloading in a single-user mobile edge computing system. The objective is to minimize the offloading latency while ensuring the secrecy of user data against a malicious eavesdropper. We develop efficient solutions to this latency minimization problem based on alternating optimization. Through numerical results, we show that the deployment of the HRRIS can result in a considerable reduction in latency. Furthermore, the latency reduction gain offered by the HRRIS is much more significant than that of the conventional reconfigurable intelligent surface (RIS).
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge