Zhengping Luo
Adversarial Machine Learning based Partial-model Attack in IoT
Jul 10, 2020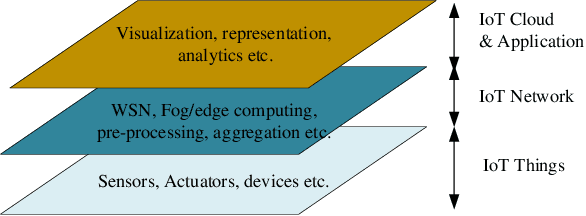
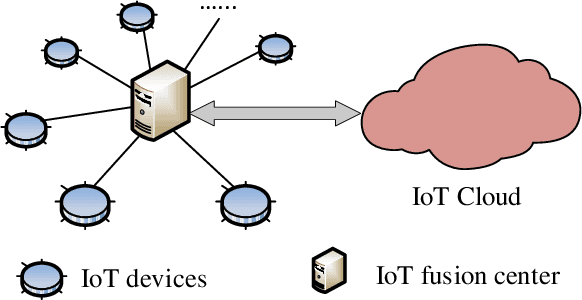
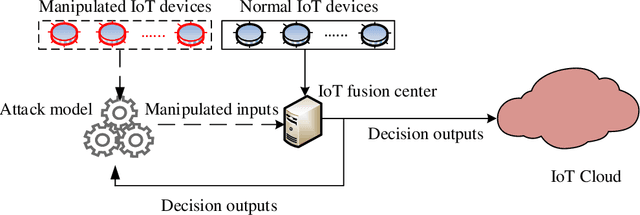
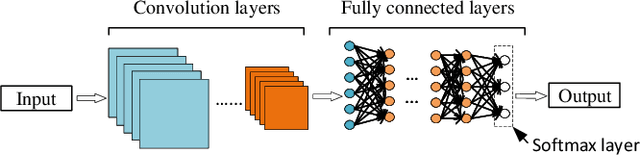
Abstract:As Internet of Things (IoT) has emerged as the next logical stage of the Internet, it has become imperative to understand the vulnerabilities of the IoT systems when supporting diverse applications. Because machine learning has been applied in many IoT systems, the security implications of machine learning need to be studied following an adversarial machine learning approach. In this paper, we propose an adversarial machine learning based partial-model attack in the data fusion/aggregation process of IoT by only controlling a small part of the sensing devices. Our numerical results demonstrate the feasibility of this attack to disrupt the decision making in data fusion with limited control of IoT devices, e.g., the attack success rate reaches 83\% when the adversary tampers with only 8 out of 20 IoT devices. These results show that the machine learning engine of IoT system is highly vulnerable to attacks even when the adversary manipulates a small portion of IoT devices, and the outcome of these attacks severely disrupts IoT system operations.
When Attackers Meet AI: Learning-empowered Attacks in Cooperative Spectrum Sensing
May 04, 2019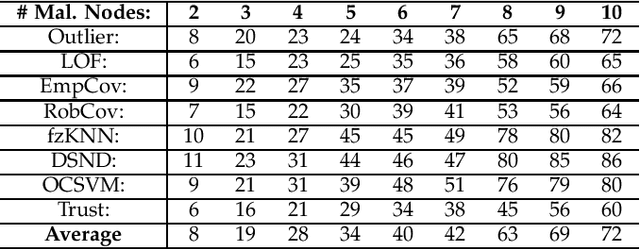
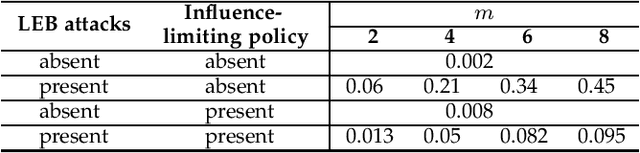
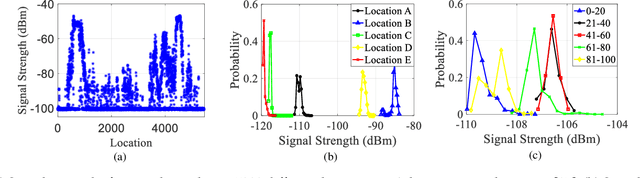
Abstract:Defense strategies have been well studied to combat Byzantine attacks that aim to disrupt cooperative spectrum sensing by sending falsified sensing data. However, existing studies usually make network or attack assumptions biased towards the defense (e.g., assuming the prior knowledge of attacks is known). In practice, attackers can adopt any arbitrary behavior and avoid any pre-assumed pattern or assumption used by defense strategies. In this paper, we revisit this traditional security problem and propose a novel learning-empowered framework named Learn-Evaluate-Beat (LEB) to mislead the fusion center. Based on the black-box nature of the fusion center in cooperative spectrum sensing process, our new perspective is to make the adversarial use of machine learning to construct a surrogate model of the fusion center's decision model. Then, we propose a generic algorithm to create malicious sensing data. Our real-world experiments show that the LEB attack is very effective to beat a wide range of existing defense strategies with an up to 82% of success ratio. Given the gap between the new LEB attack and existing defenses, we introduce a non-invasive and parallel method named as influence-limiting policy sided with existing defenses to defend against the LEB-based or other similar attacks, which demonstrates a strong performance in terms of overall disruption ratio reduction by up to 80% of the LEB attacks.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge