Walter Lucia
Trojan Attacks on Neural Network Controllers for Robotic Systems
Feb 04, 2026Abstract:Neural network controllers are increasingly deployed in robotic systems for tasks such as trajectory tracking and pose stabilization. However, their reliance on potentially untrusted training pipelines or supply chains introduces significant security vulnerabilities. This paper investigates backdoor (Trojan) attacks against neural controllers, using a differential-drive mobile robot platform as a case study. In particular, assuming that the robot's tracking controller is implemented as a neural network, we design a lightweight, parallel Trojan network that can be embedded within the controller. This malicious module remains dormant during normal operation but, upon detecting a highly specific trigger condition defined by the robot's pose and goal parameters, compromises the primary controller's wheel velocity commands, resulting in undesired and potentially unsafe robot behaviours. We provide a proof-of-concept implementation of the proposed Trojan network, which is validated through simulation under two different attack scenarios. The results confirm the effectiveness of the proposed attack and demonstrate that neural network-based robotic control systems are subject to potentially critical security threats.
Collision-Free Platooning of Mobile Robots through a Set-Theoretic Predictive Control Approach
Mar 13, 2024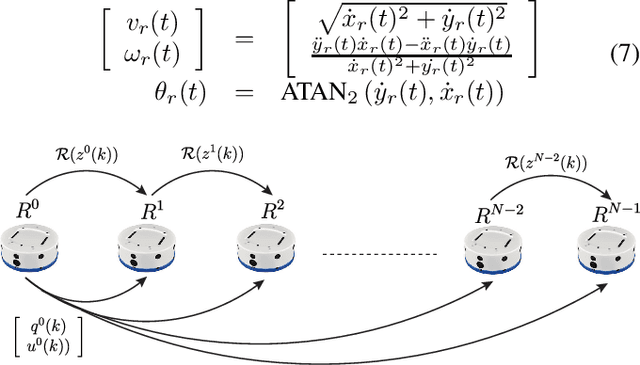
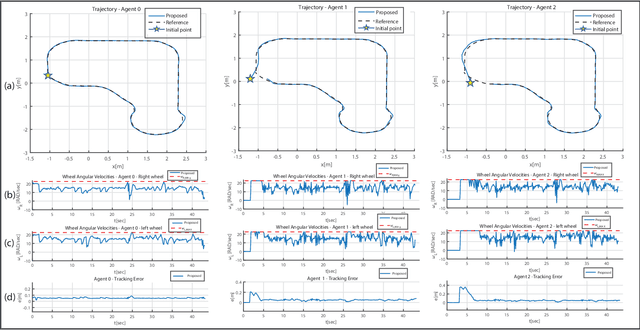
Abstract:This paper proposes a control solution to achieve collision-free platooning control of input-constrained mobile robots. The platooning policy is based on a leader-follower approach where the leader tracks a reference trajectory while followers track the leader's pose with an inter-agent delay. First, the leader and the follower kinematic models are feedback linearized and the platoon's error dynamics and input constraints characterized. Then, a set-theoretic model predictive control strategy is proposed to address the platooning trajectory tracking control problem. An ad-hoc collision avoidance policy is also proposed to guarantee collision avoidance amongst the agents. Finally, the effectiveness of the proposed control architecture is validated through experiments performed on a formation of Khepera IV differential drive robots
An Observer-Based Key Agreement Scheme for Remotely Controlled Mobile Robots
Mar 08, 2023Abstract:Remotely controlled mobile robots are important examples of Cyber-Physical Systems (CPSs). Recently, these robots are being deployed in many safety critical applications. Therefore, ensuring their cyber-security is of paramount importance. Different control schemes that have been proposed to secure such systems against sophisticated cyber-attacks require the exchange of secret messages between their smart actuators and the remote controller. Thus, these schemes require pre-shared secret keys, or an established Public Key Infrastructure (PKI) that allows for key agreement. Such cryptographic approaches might not always be suitable for the deployment environments of such remotely mobile robots. To address this problem, in this paper, we consider a control theoretic approach for establishing a secret key between the remotely controlled robot and the networked controller without resorting to traditional cryptographic techniques. Our key agreement scheme leverages a nonlinear unknown input observer and an error correction code mechanism to allow the robot to securely agree on a secret key with its remote controller. To validate the proposed scheme, we implement it using a Khepera-IV differential drive robot and evaluate its efficiency and the additional control cost acquired by it. Our experimental results confirm the effectiveness of the proposed key establishment scheme.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge