Vahid Shah-Mansouri
Diffusion-RL for Scalable Resource Allocation for 6G Networks
Jun 09, 2025Abstract:This paper presents a novel approach to resource allocation in Open Radio Access Networks (O-RAN), leveraging a Generative AI technique with network slicing to address the diverse demands of 5G and 6G service types such as Enhanced Mobile Broadband (eMBB), Ultra-Reliable Low-Latency Communications (URLLC), and Massive Machine-Type Communications (mMTC). Additionally, we provide a comprehensive analysis and comparison of machine learning (ML) techniques for resource allocation within O-RAN, evaluating their effectiveness in optimizing network performance. We introduce a diffusion-based reinforcement learning (Diffusion-RL) algorithm designed to optimize the allocation of physical resource blocks (PRBs) and power consumption, thereby maximizing weighted throughput and minimizing the delay for user equipment (UE). The Diffusion-RL model incorporates controlled noise and perturbations to explore optimal resource distribution while meeting each service type's Quality of Service (QoS) requirements. We evaluate the performance of our proposed method against several benchmarks, including an exhaustive search algorithm, deep Q-networks (DQN), and the Semi-Supervised Variational Autoencoder (SS-VAE). Comprehensive metrics, such as throughput and latency, are presented for each service type. Experimental results demonstrate that the Diffusion-based RL approach outperforms existing methods in efficiency, scalability, and robustness, offering a promising solution for resource allocation in dynamic and heterogeneous O-RAN environments with significant implications for future 6G networks.
Towards Secure Intelligent O-RAN Architecture: Vulnerabilities, Threats and Promising Technical Solutions using LLMs
Nov 13, 2024Abstract:The evolution of wireless communication systems will be fundamentally impacted by an open radio access network (O-RAN), a new concept defining an intelligent architecture with enhanced flexibility, openness, and the ability to slice services more efficiently. For all its promises, and like any technological advancement, O-RAN is not without risks that need to be carefully assessed and properly addressed to accelerate its wide adoption in future mobile networks. In this paper, we present an in-depth security analysis of the O-RAN architecture, discussing the potential threats that may arise in the different O-RAN architecture layers and their impact on the Confidentiality, Integrity, and Availability (CIA) triad. We also promote the potential of zero trust, Moving Target Defense (MTD), blockchain, and large language models(LLM) technologies in fortifying O-RAN's security posture. Furthermore, we numerically demonstrate the effectiveness of MTD in empowering robust deep reinforcement learning methods for dynamic network slice admission control in the O-RAN architecture. Moreover, we examine the effect of explainable AI (XAI) based on LLMs in securing the system.
Semi-Supervised Learning Approach for Efficient Resource Allocation with Network Slicing in O-RAN
Jan 16, 2024Abstract:The Open Radio Access Network (O-RAN) technology has emerged as a promising solution for network operators, providing them with an open and favorable environment. Ensuring effective coordination of x-applications (xAPPs) is crucial to enhance flexibility and optimize network performance within the O-RAN. In this paper, we introduce an innovative approach to the resource allocation problem, aiming to coordinate multiple independent xAPPs for network slicing and resource allocation in O-RAN. Our proposed method focuses on maximizing the weighted throughput among user equipments (UE), as well as allocating physical resource blocks (PRBs). We prioritize two service types, namely enhanced Mobile Broadband and Ultra Reliable Low Latency Communication. To achieve this, we have designed two xAPPs: a power control xAPP for each UE and a PRB allocation xAPP. The proposed method consists of a two-part training phase, where the first part uses supervised learning with a Variational Autoencoder trained to regress the power transmission as well as the user association and PRB allocation decisions, and the second part uses unsupervised learning with a contrastive loss approach to improve the generalization and robustness of the model. We evaluate the performance of our proposed method by comparing its results to those obtained from an exhaustive search algorithm, deep Q-network algorithm, and by reporting performance metrics for the regression task. We also evaluate the proposed model's performance in different scenarios among the service types. The results show that the proposed method is a more efficient and effective solution for network slicing problems compared to state-of-the-art methods.
Generative Adversarial Networks (GANs) in Networking: A Comprehensive Survey & Evaluation
May 10, 2021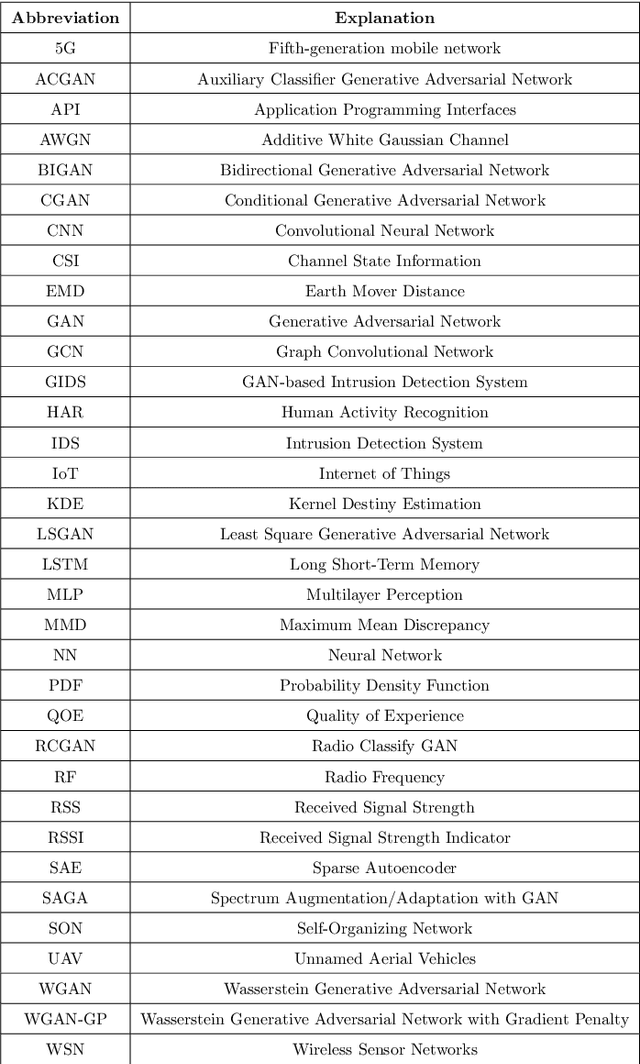
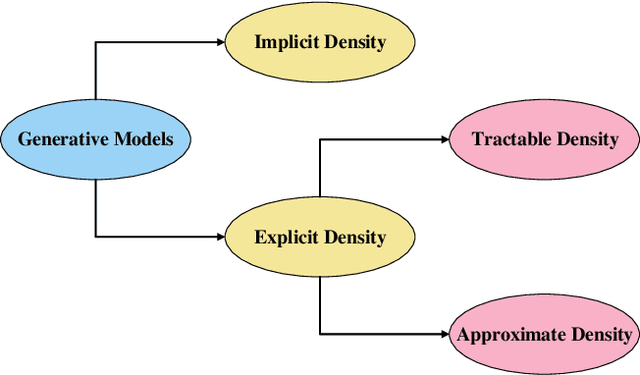
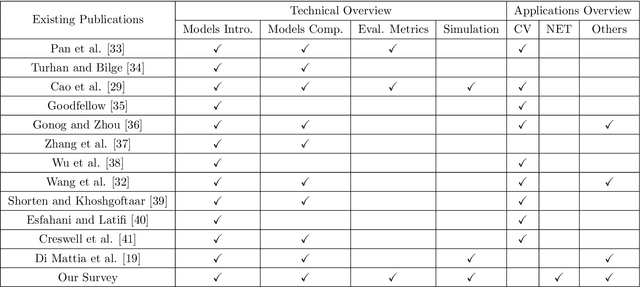
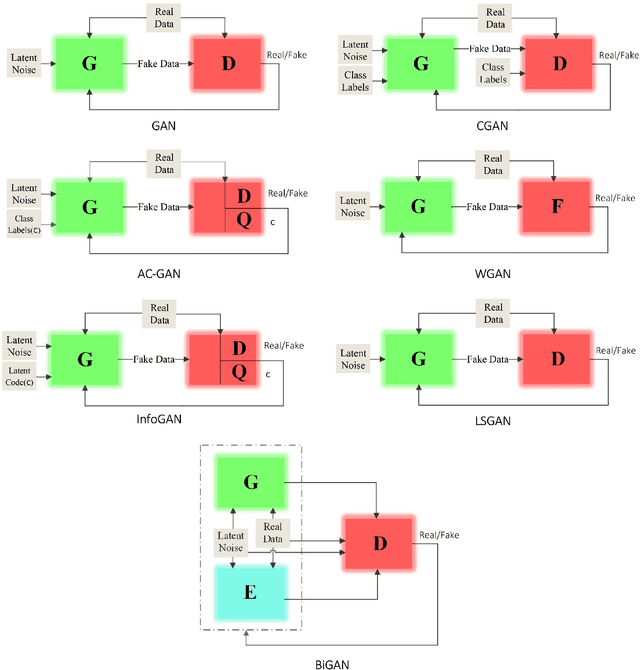
Abstract:Despite the recency of their conception, Generative Adversarial Networks (GANs) constitute an extensively researched machine learning sub-field for the creation of synthetic data through deep generative modeling. GANs have consequently been applied in a number of domains, most notably computer vision, in which they are typically used to generate or transform synthetic images. Given their relative ease of use, it is therefore natural that researchers in the field of networking (which has seen extensive application of deep learning methods) should take an interest in GAN-based approaches. The need for a comprehensive survey of such activity is therefore urgent. In this paper, we demonstrate how this branch of machine learning can benefit multiple aspects of computer and communication networks, including mobile networks, network analysis, internet of things, physical layer, and cybersecurity. In doing so, we shall provide a novel evaluation framework for comparing the performance of different models in non-image applications, applying this to a number of reference network datasets.
Classification of Traffic Using Neural Networks by Rejecting: a Novel Approach in Classifying VPN Traffic
Jan 10, 2020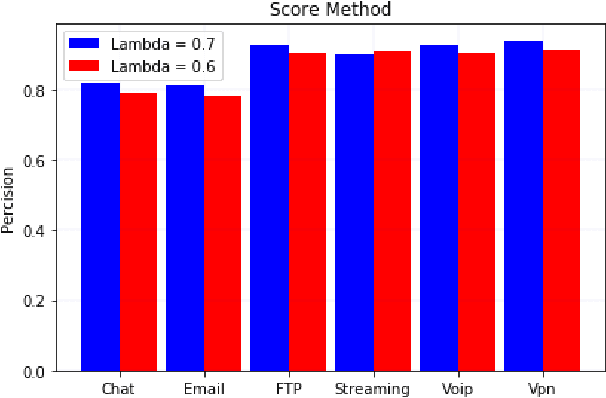
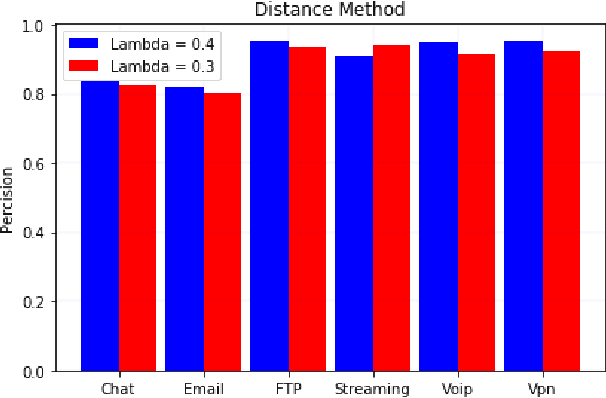
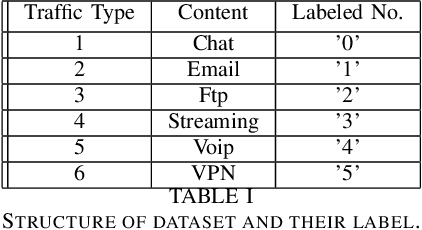
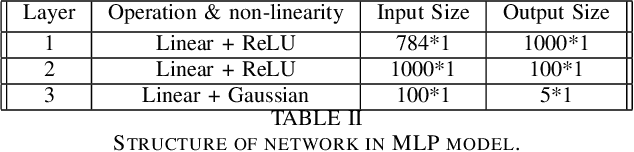
Abstract:Traffic flows are set of packets transferring between a client and a server with the same set of source and destination IP and port numbers. Traffic classification is referred to as the task of categorizing traffic flows into application-aware classes such as chats, streaming, VoIP, etc. Classification can be used for several purposes including policy enforcement and control or QoS management. In this paper, we introduce a novel end-to-end traffic classification method to distinguish between traffic classes including VPN traffic. Classification of VPN traffic is not trivial using traditional classification approaches due to its encrypted nature. We utilize two well-known neural networks, namely multi-layer perceptron and recurrent neural network focused on two metrics: class scores and distance from the center of the classes. Such approaches combined extraction, selection, and classification functionality into a single end-to-end system to systematically learn the non-linear relationship between input and predicted performance. Therefore, we could distinguish VPN traffics from Non-VPN traffics by rejecting the unrelated features of the VPN class. Moreover, obtain the application of Non-VPN traffics at the same time. The approach is evaluated using the general traffic dataset ISCX VPN-nonVPN and the acquired real dataset. The results of the analysis demonstrate that our proposed model fulfills the realistic project's criterion for precision.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge