Tong-Xing Zheng
STAR-RIS Assisted Covert Communications in NOMA Systems
Jun 12, 2023Abstract:Covert communications assisted by simultaneously transmitting and reflecting reconfigurable intelligent surface (STAR-RIS) in non-orthogonal multiple access (NOMA) systems have been explored in this paper. In particular, the access point (AP) transmitter adopts NOMA to serve a downlink covert user and a public user. The minimum detection error probability (DEP) at the warden is derived considering the uncertainty of its background noise, which is used as a covertness constraint. We aim at maximizing the covert rate of the system by jointly optimizing APs transmit power and passive beamforming of STAR-RIS, under the covertness and quality of service (QoS) constraints. An iterative algorithm is proposed to effectively solve the non-convex optimization problem. Simulation results show that the proposed scheme significantly outperforms the conventional RIS-based scheme in ensuring system covert performance.
STAR-RIS Aided Covert Communication
May 11, 2023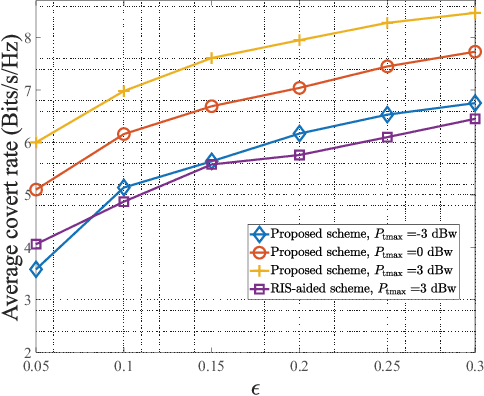
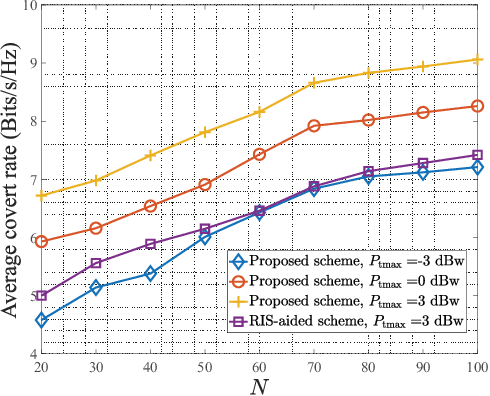
Abstract:This paper investigates the multi-antenna covert communications assisted by a simultaneously transmitting and reflecting reconfigurable intelligent surface (STAR-RIS). In particular, to shelter the existence of communications between transmitter and receiver from a warden, a friendly full-duplex receiver with two antennas is leveraged to make contributions to confuse the warden. Considering the worst case, the closed-form expression of the minimum detection error probability (DEP) at the warden is derived and utilized as a covert constraint. Then, we formulate an optimization problem maximizing the covert rate of the system under the covertness constraint and quality of service (QoS) constraint with communication outage analysis. To jointly design the active and passive beamforming of the transmitter and STAR-RIS, an iterative algorithm based on globally convergent version of method of moving asymptotes (GCMMA) is proposed to effectively solve the non-convex optimization problem. Simulation results show that the proposed STAR-RIS-assisted scheme highly outperforms the case with conventional RIS.
Physical layer security in large-scale random multiple access wireless sensor networks: a stochastic geometry approach
Apr 13, 2022



Abstract:This paper investigates physical layer security for a large-scale WSN with random multiple access, where each fusion center in the network randomly schedules a number of sensors to upload their sensed data subject to the overhearing of randomly distributed eavesdroppers. We propose an uncoordinated random jamming scheme in which those unscheduled sensors send jamming signals with a certain probability to defeat the eavesdroppers. With the aid of stochastic geometry theory and order statistics, we derive analytical expressions for the connection outage probability and secrecy outage probability to characterize transmission reliability and secrecy, respectively. Based on the obtained analytical results, we formulate an optimization problem for maximizing the sum secrecy throughput subject to both reliability and secrecy constraints, considering a joint design of the wiretap code rates for each scheduled sensor and the jamming probability for the unscheduled sensors. We provide both optimal and low-complexity sub-optimal algorithms to tackle the above problem, and further reveal various properties on the optimal parameters which are useful to guide practical designs. In particular, we demonstrate that the proposed random jamming scheme is beneficial for improving the sum secrecy throughput, and the optimal jamming probability is the result of trade-off between secrecy and throughput. We also show that the throughput performance of the sub-optimal scheme approaches that of the optimal one when facing a stringent reliability constraint or a loose secrecy constraint.
Physical Layer Security for NOMA-Enabled Multi-Access Edge Computing Wireless Networks
Jul 03, 2021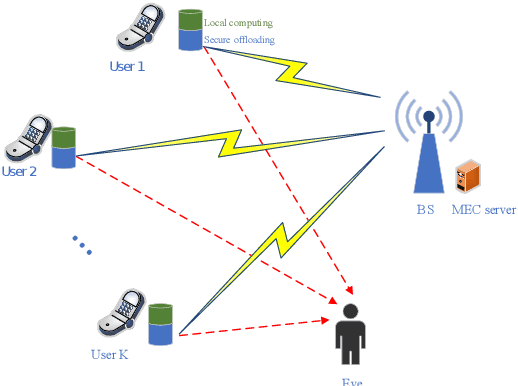
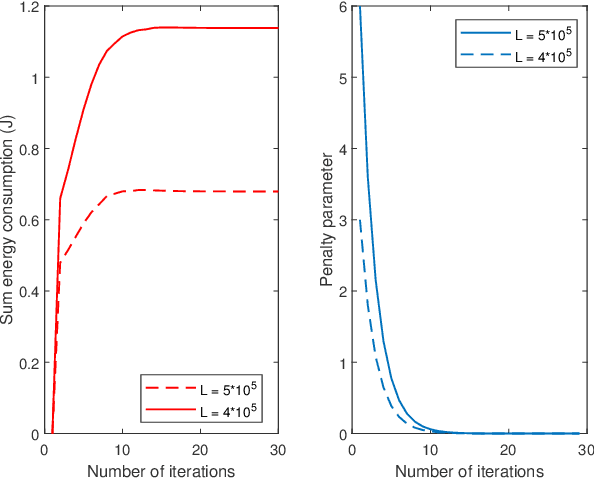
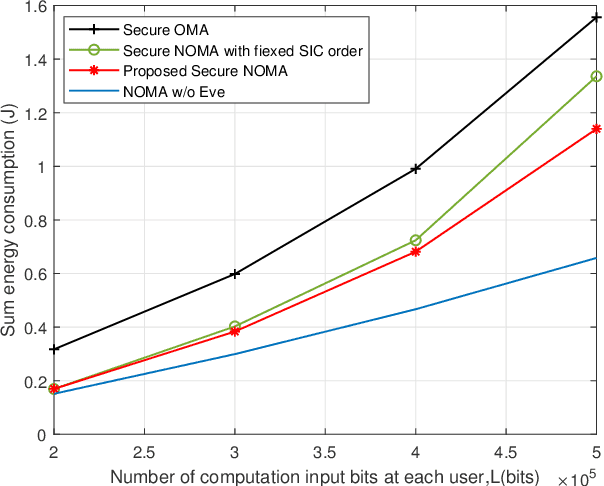
Abstract:Multi-access edge computing (MEC) has been regarded as a promising technique for enhancing computation capabilities for wireless networks. In this paper, we study physical layer security in an MEC system where multiple users offload partial of their computation tasks to a base station simultaneously based on non-orthogonal multiple access (NOMA), in the presence of a malicious eavesdropper. Secrecy outage probability is adopted to measure the security performance of the computation offloading against eavesdropping attacks. We aim to minimize the sum energy consumption of all the users, subject to constraints in terms of the secrecy offloading rate, the secrecy outage probability, and the decoding order of NOMA. Although the original optimization problem is non-convex and challenging to solve, we put forward an efficient algorithm based on sequential convex approximation and penalty dual decomposition. Numerical results are eventually provided to validate the convergence of the proposed algorithm and its superior energy efficiency with secrecy requirements.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge