Pengcheng Mu
STAR-RIS Enhanced UAV-Enabled MEC Networks with Bi-Directional Task Offloading
Jan 11, 2024



Abstract:A simultaneously transmitting and reflecting reconfigurable intelligent surface (STAR-RIS) enhanced unnamed aerial vehicle (UAV)-enabled multi-user mobile edge computing (MEC) scheme is proposed in this paper. Different from the existing MEC works, the proposed scheme allows bi-directional offloading where users can simultaneously offload their computing tasks to the MEC servers situated at the ground base station (BS) and aerial UAV with the assistance of the STARRIS. Specifically, we formulate an optimization problem aiming at maximizing the energy efficiency of the system while ensuring the quality of service (QoS) constraint by jointly optimizing the resource allocation, user scheduling, passive beamforming of the STAR-RIS, and the UAV trajectory. An iterative algorithm designed with the Dinkelbach's algorithm and the successive convex approximation (SCA) is proposed to effectively handle the formulated non-convex optimization problem. Simulation results indicate that the proposed STAR-RIS enhanced UAV-enabled MEC scheme possesses significant advantages in enhancing the system energy efficiency over other baseline schemes including the conventional RIS-aided scheme.
On the Generalization and Advancement of Half-Sine-Based Pulse Shaping Filters for Constant Envelope OQPSK Modulation
Jun 14, 2023Abstract:The offset quadrature phase-shift keying (OQPSK) modulation is a key factor for the technique of ZigBee, which has been adopted in IEEE 802.15.4 for wireless communications of Internet of Things (IoT) and Internet of Vehicles (IoV), etc. In this paper, we propose the general conditions of pulse shaping filters (PSFs) with constant envelope (CE) property for OQPSK modulation, which can be easily leveraged to design the PSFs with CE property. Based on these conditions, we further design an advanced PSF called $\alpha$-half-sine PSF. It is verified that the newly designed $\alpha$-half-sine PSF can not only keep the CE property for OQPSK but also achieve better performance than the traditional PSFs in certain scenarios. Moreover, the $\alpha$-half-sine PSF can be simply adjusted to achieve a flexible performance tradeoff between the transition roll-off speed and out-of-band leakage.
STAR-RIS Aided Covert Communication
May 11, 2023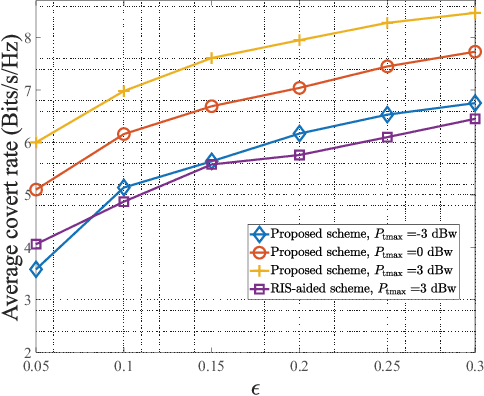
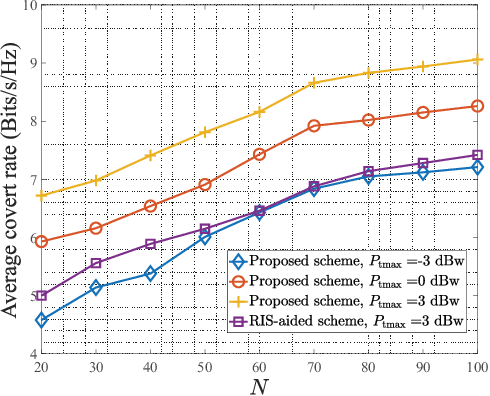
Abstract:This paper investigates the multi-antenna covert communications assisted by a simultaneously transmitting and reflecting reconfigurable intelligent surface (STAR-RIS). In particular, to shelter the existence of communications between transmitter and receiver from a warden, a friendly full-duplex receiver with two antennas is leveraged to make contributions to confuse the warden. Considering the worst case, the closed-form expression of the minimum detection error probability (DEP) at the warden is derived and utilized as a covert constraint. Then, we formulate an optimization problem maximizing the covert rate of the system under the covertness constraint and quality of service (QoS) constraint with communication outage analysis. To jointly design the active and passive beamforming of the transmitter and STAR-RIS, an iterative algorithm based on globally convergent version of method of moving asymptotes (GCMMA) is proposed to effectively solve the non-convex optimization problem. Simulation results show that the proposed STAR-RIS-assisted scheme highly outperforms the case with conventional RIS.
Physical Layer Security for NOMA-Enabled Multi-Access Edge Computing Wireless Networks
Jul 03, 2021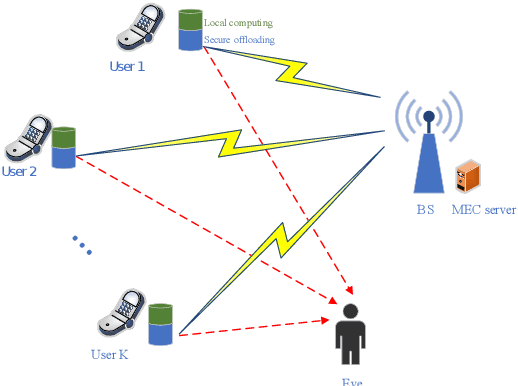
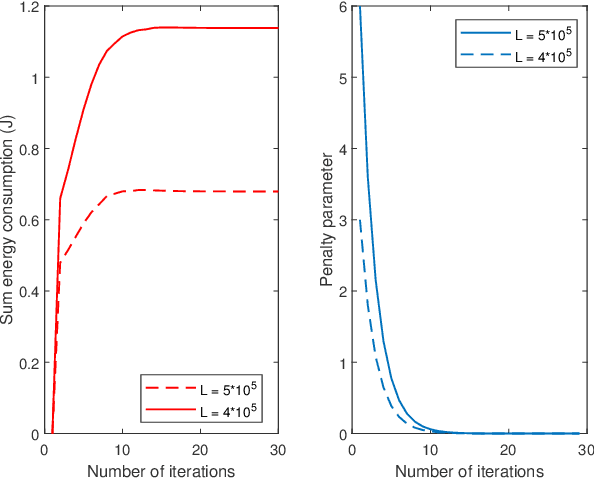
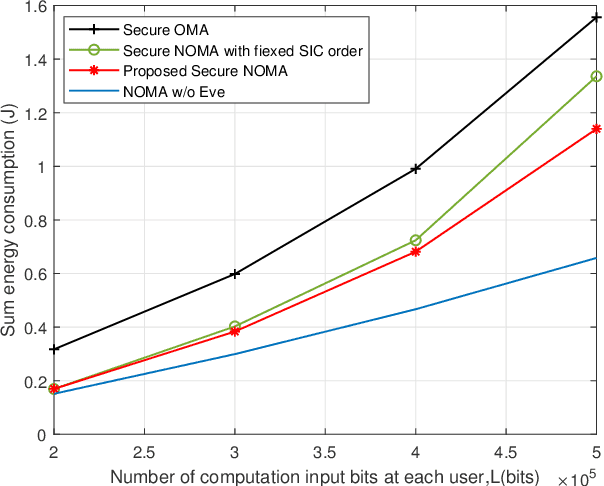
Abstract:Multi-access edge computing (MEC) has been regarded as a promising technique for enhancing computation capabilities for wireless networks. In this paper, we study physical layer security in an MEC system where multiple users offload partial of their computation tasks to a base station simultaneously based on non-orthogonal multiple access (NOMA), in the presence of a malicious eavesdropper. Secrecy outage probability is adopted to measure the security performance of the computation offloading against eavesdropping attacks. We aim to minimize the sum energy consumption of all the users, subject to constraints in terms of the secrecy offloading rate, the secrecy outage probability, and the decoding order of NOMA. Although the original optimization problem is non-convex and challenging to solve, we put forward an efficient algorithm based on sequential convex approximation and penalty dual decomposition. Numerical results are eventually provided to validate the convergence of the proposed algorithm and its superior energy efficiency with secrecy requirements.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge