Shalini Tripathi
Joint Transmit and Jamming Power Optimization for Secrecy in Energy Harvesting Networks: A Reinforcement Learning Approach
Jul 24, 2024



Abstract:In this paper, we address the problem of joint allocation of transmit and jamming power at the source and destination, respectively, to enhance the long-term cumulative secrecy performance of an energy-harvesting wireless communication system until it stops functioning in the presence of an eavesdropper. The source and destination have energy-harvesting devices with limited battery capacities. The destination also has a full-duplex transceiver to transmit jamming signals for secrecy. We frame the problem as an infinite-horizon Markov decision process (MDP) problem and propose a reinforcement learning-based optimal joint power allocation (OJPA) algorithm that employs a policy iteration (PI) algorithm. Since the optimal algorithm is computationally expensive, we develop a low-complexity sub-optimal joint power allocation (SJPA) algorithm, namely, reduced state joint power allocation (RSJPA). Two other SJPA algorithms, the greedy algorithm (GA) and the naive algorithm (NA), are implemented as benchmarks. In addition, the OJPA algorithm outperforms the individual power allocation (IPA) algorithms termed individual transmit power allocation (ITPA) and individual jamming power allocation (IJPA), where the transmit and jamming powers, respectively, are optimized individually. The results show that the OJPA algorithm is also more energy efficient. Simulation results show that the OJPA algorithm significantly improves the secrecy performance compared to all SJPA algorithms. The proposed RSJPA algorithm achieves nearly optimal performance with significantly less computational complexity marking it the balanced choice between the complexity and the performance. We find that the computational time for the RSJPA algorithm is around 75 percent less than the OJPA algorithm.
Recurrent Neural Network Assisted Transmitter Selection for Secrecy in Cognitive Radio Network
Feb 16, 2021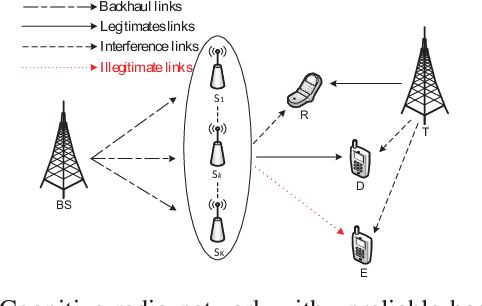

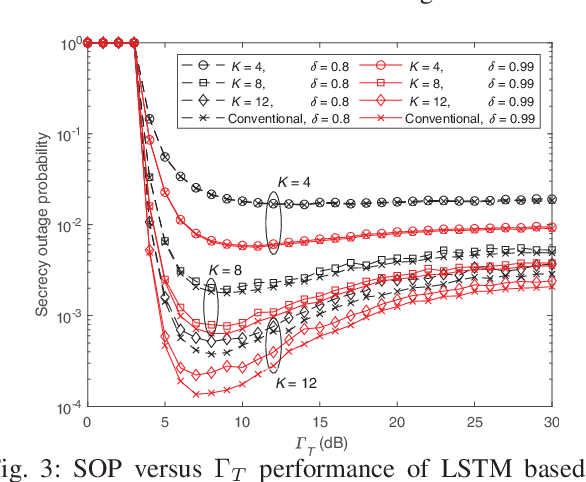
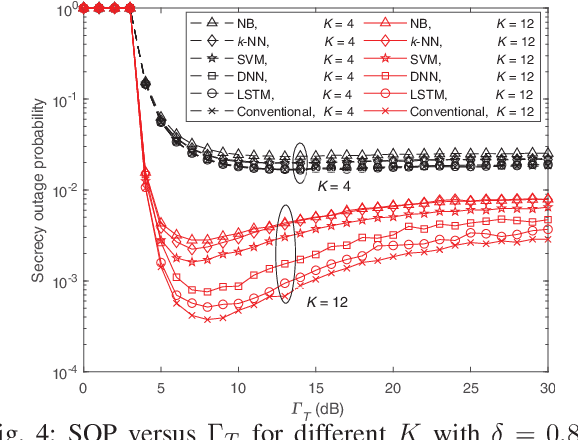
Abstract:In this paper, we apply the long short-term memory (LSTM), an advanced recurrent neural network based machine learning (ML) technique, to the problem of transmitter selection (TS) for secrecy in an underlay small-cell cognitive radio network with unreliable backhaul connections. The cognitive communication scenario under consideration has a secondary small-cell network that shares the same spectrum of the primary network with an agreement to always maintain a desired outage probability constraint in the primary network. Due to the interference from the secondary transmitter common to all primary transmissions, the secrecy rates for the different transmitters are correlated. LSTM exploits this correlation and matches the performance of the conventional technique when the number of transmitters is small. As the number grows, the performance degrades in the same manner as other ML techniques such as support vector machine, $k$-nearest neighbors, naive Bayes, and deep neural network. However, LSTM still significantly outperforms these techniques in misclassification ratio and secrecy outage probability. It also reduces the feedback overhead against conventional TS.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge