Saud Khan
Access-based Lightweight Physical Layer Authentication for the Internet of Things Devices
Mar 01, 2023



Abstract:Physical-layer authentication is a popular alternative to the conventional key-based authentication for internet of things (IoT) devices due to their limited computational capacity and battery power. However, this approach has limitations due to poor robustness under channel fluctuations, reconciliation overhead, and no clear safeguard distance to ensure the secrecy of the generated authentication keys. In this regard, we propose a novel, secure, and lightweight continuous authentication scheme for IoT device authentication. Our scheme utilizes the inherent properties of the IoT devices transmission model as its source for seed generation and device authentication. Specifically, our proposed scheme provides continuous authentication by checking the access time slots and spreading sequences of the IoT devices instead of repeatedly generating and verifying shared keys. Due to this, access to a coherent key is not required in our proposed scheme, resulting in the concealment of the seed information from attackers. Our proposed authentication scheme for IoT devices demonstrates improved performance compared to the benchmark schemes relying on physical-channel. Our empirical results find a near threefold decrease in misdetection rate of illegitimate devices and close to zero false alarm rate in various system settings with varied numbers of active devices up to 200 and signal-to-noise ratio from 0 dB to 30 dB. Our proposed authentication scheme also has a lower computational complexity of at least half the computational cost of the benchmark schemes based on support vector machine and binary hypothesis testing in our studies. This further corroborates the practicality of our scheme for IoT deployments.
Joint User and Data Detection in Grant-Free NOMA with Attention-based BiLSTM Network
Sep 14, 2022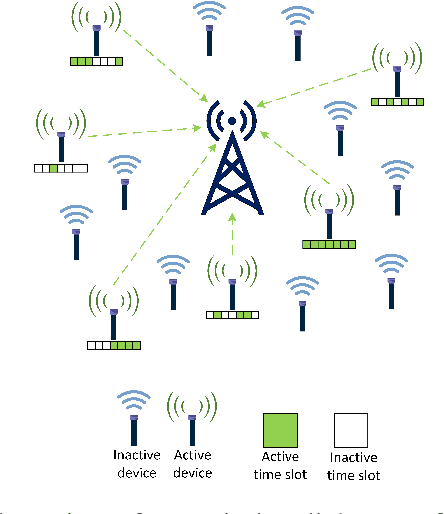
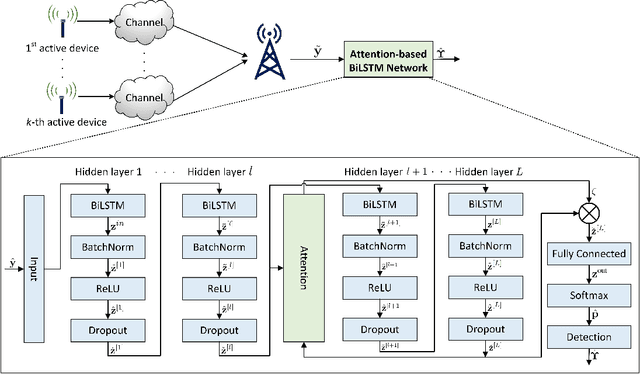
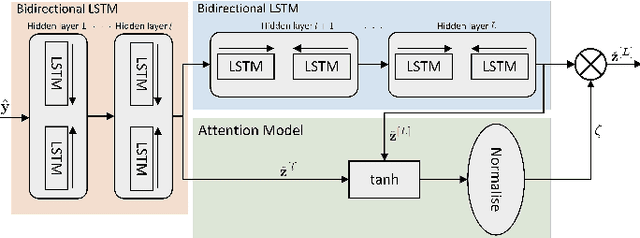

Abstract:We consider the multi-user detection (MUD) problem in uplink grant-free non-orthogonal multiple access (NOMA), where the access point has to identify the total number and correct identity of the active Internet of Things (IoT) devices and decode their transmitted data. We assume that IoT devices use complex spreading sequences and transmit information in a random-access manner following the burst-sparsity model, where some IoT devices transmit their data in multiple adjacent time slots with a high probability, while others transmit only once during a frame. Exploiting the temporal correlation, we propose an attention-based bidirectional long short-term memory (BiLSTM) network to solve the MUD problem. The BiLSTM network creates a pattern of the device activation history using forward and reverse pass LSTMs, whereas the attention mechanism provides essential context to the device activation points. By doing so, a hierarchical pathway is followed for detecting active devices in a grant-free scenario. Then, by utilising the complex spreading sequences, blind data detection for the estimated active devices is performed. The proposed framework does not require prior knowledge of device sparsity levels and channels for performing MUD. The results show that the proposed network achieves better performance compared to existing benchmark schemes.
Intelligent Reflective Surface Deployment in 6G: A Comprehensive Survey
Apr 03, 2022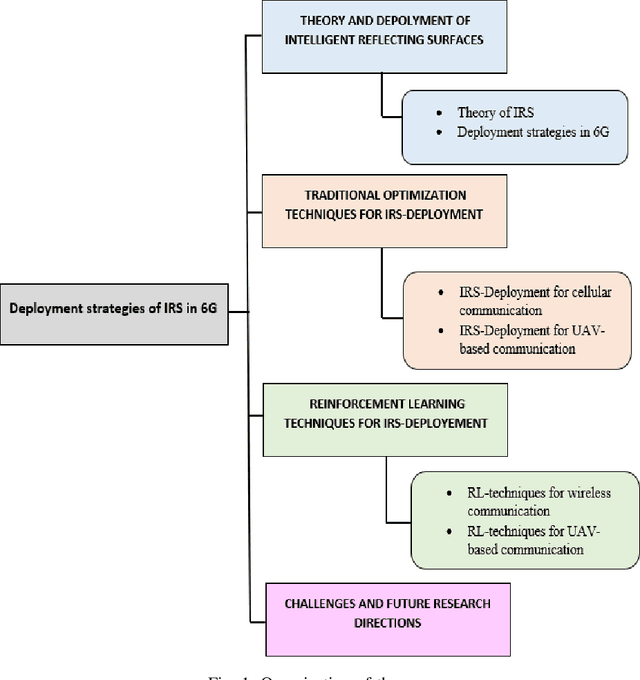

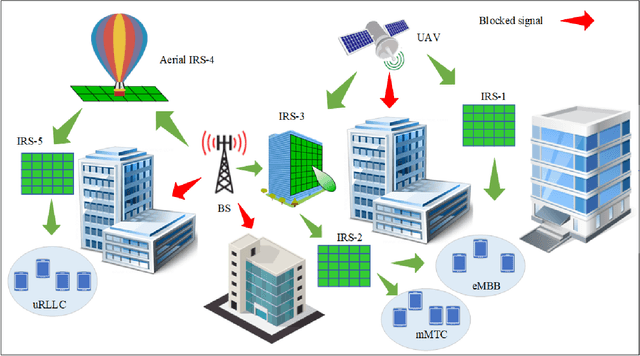
Abstract:Intelligent reflecting surfaces (IRSs) are considered a promising technology that can smartly reconfigure the wireless environment to enhance the performance of future wireless networks. However, the deployment of IRSs still faces challenges due to highly dynamic and mobile unmanned aerial vehicle (UAV) enabled wireless environments to achieve higher capacity. This paper sheds light on the different deployment strategies for IRSs in future terrestrial and non-terrestrial networks. Specifically, in this paper, we introduce key theoretical concepts underlying the IRS paradigm and discuss the design aspects related to the deployment of IRSs in 6G networks. We also explore optimization-based IRS deployment techniques to improve system performance in terrestrial and aerial IRSs. Furthermore, we survey model-free reinforcement learning (RL) techniques from the deployment aspect to address the challenges of achieving higher capacity in complex and mobile IRS-assisted UAV wireless systems. Finally, we highlight challenges and future research directions from the deployment aspect of IRSs for improving system performance for the future 6G network.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge