Pavel Filonov
Anomaly Detection for Water Treatment System based on Neural Network with Automatic Architecture Optimization
Jul 19, 2018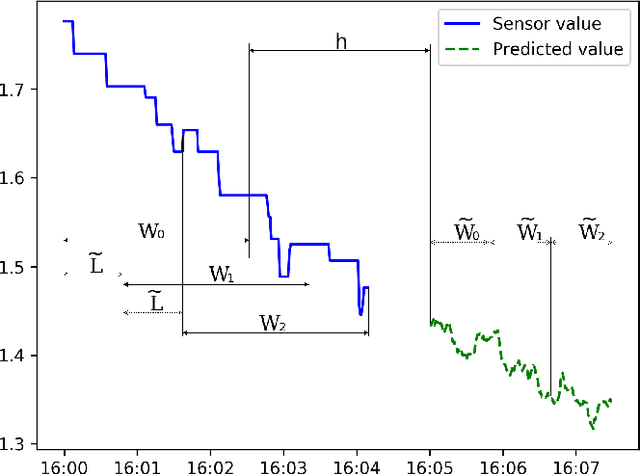
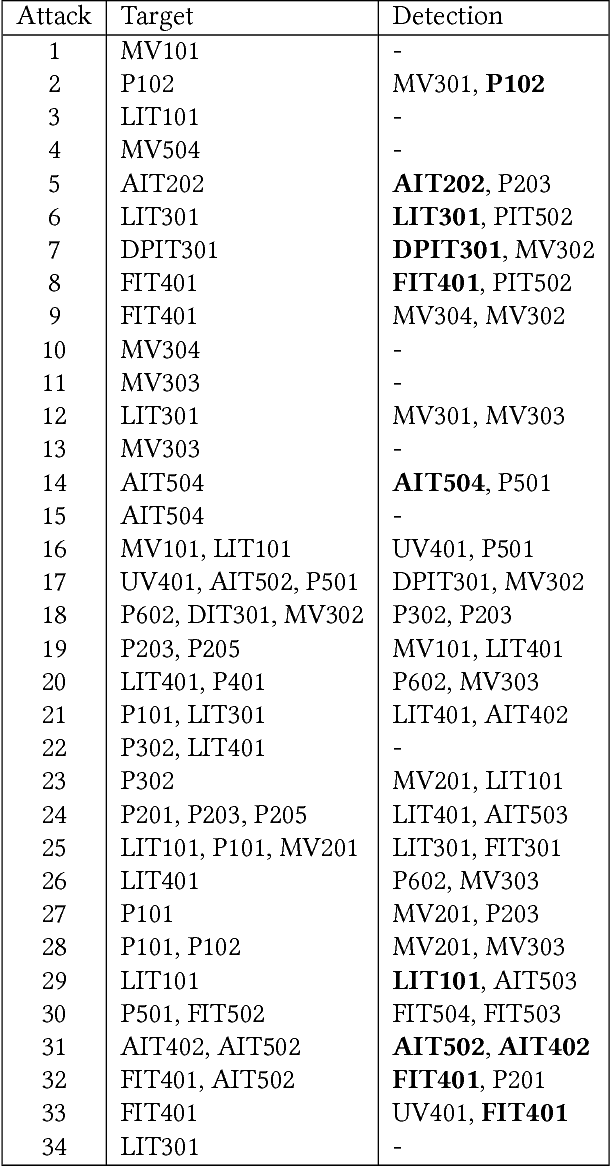
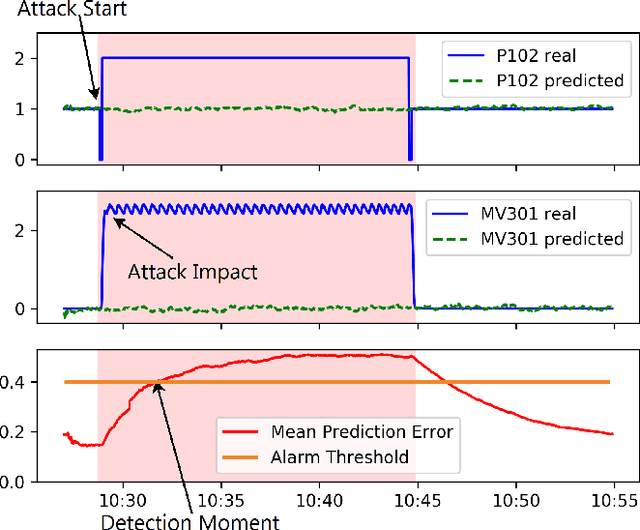
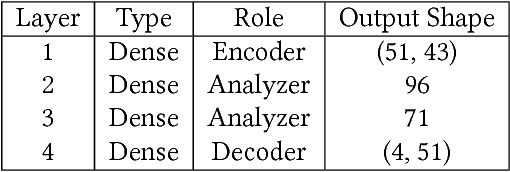
Abstract:We continue to develop our neural network (NN) based forecasting approach to anomaly detection (AD) using the Secure Water Treatment (SWaT) industrial control system (ICS) testbed dataset. We propose genetic algorithms (GA) to find the best NN architecture for a given dataset, using the NAB metric to assess the quality of different architectures. The drawbacks of the F1-metric are analyzed. Several techniques are proposed to improve the quality of AD: exponentially weighted smoothing, mean p-powered error measure, individual error weight for each variable, disjoint prediction windows. Based on the techniques used, an approach to anomaly interpretation is introduced.
RNN-based Early Cyber-Attack Detection for the Tennessee Eastman Process
Sep 07, 2017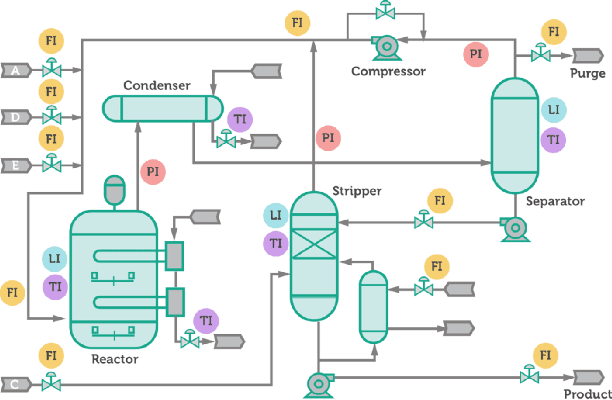
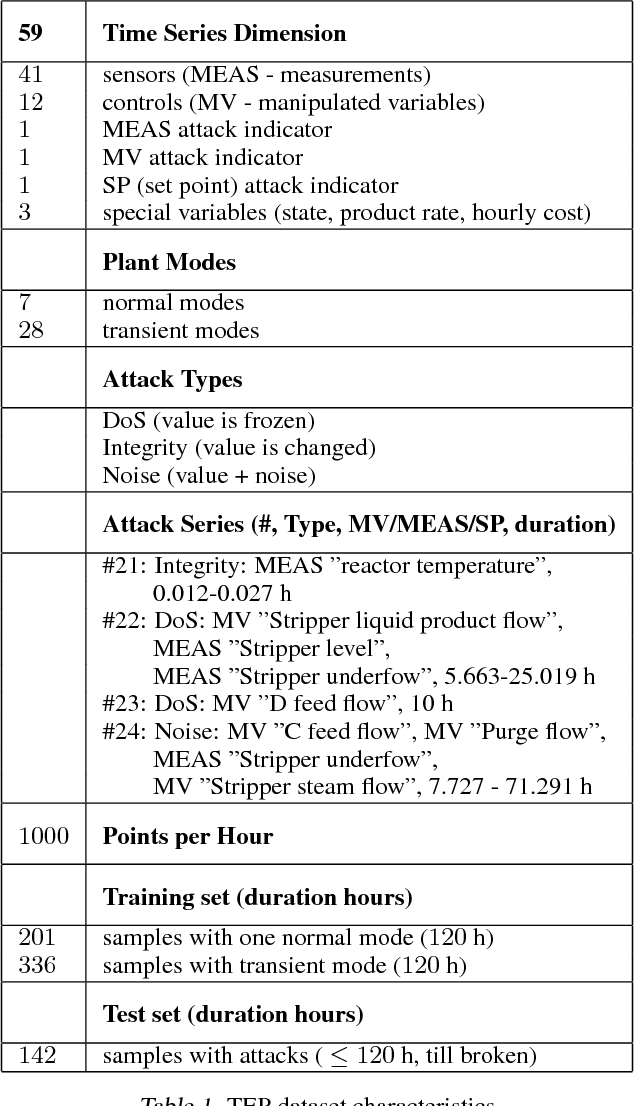
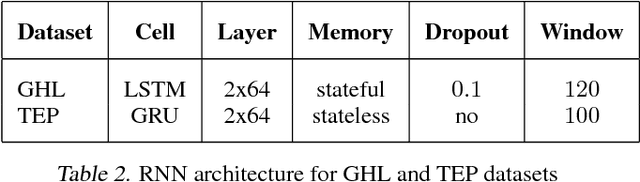
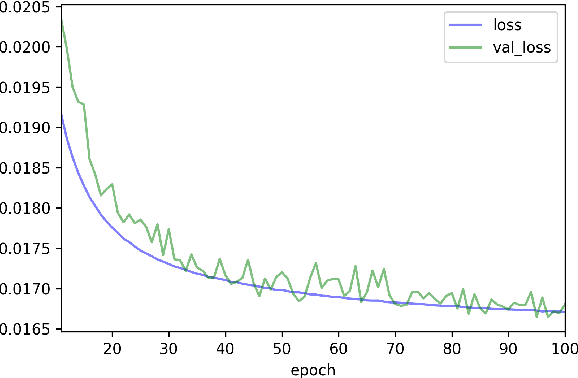
Abstract:An RNN-based forecasting approach is used to early detect anomalies in industrial multivariate time series data from a simulated Tennessee Eastman Process (TEP) with many cyber-attacks. This work continues a previously proposed LSTM-based approach to the fault detection in simpler data. It is considered necessary to adapt the RNN network to deal with data containing stochastic, stationary, transitive and a rich variety of anomalous behaviours. There is particular focus on early detection with special NAB-metric. A comparison with the DPCA approach is provided. The generated data set is made publicly available.
Multivariate Industrial Time Series with Cyber-Attack Simulation: Fault Detection Using an LSTM-based Predictive Data Model
Dec 26, 2016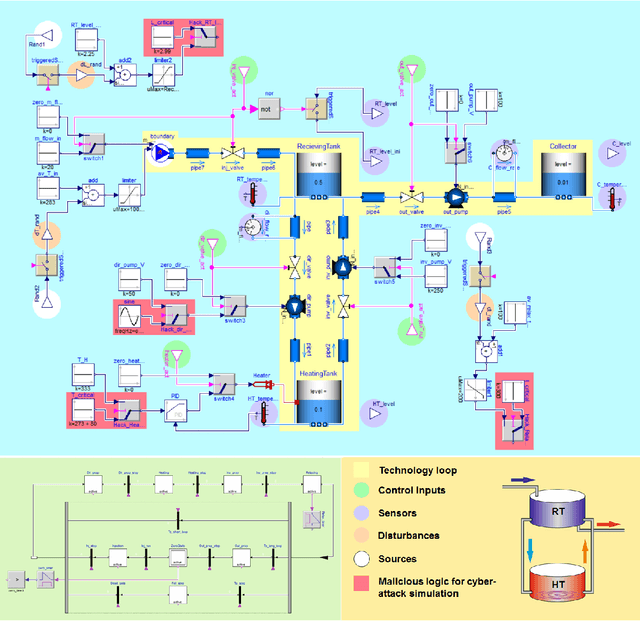
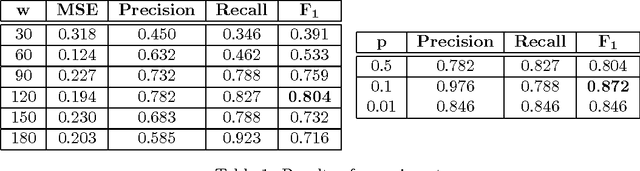
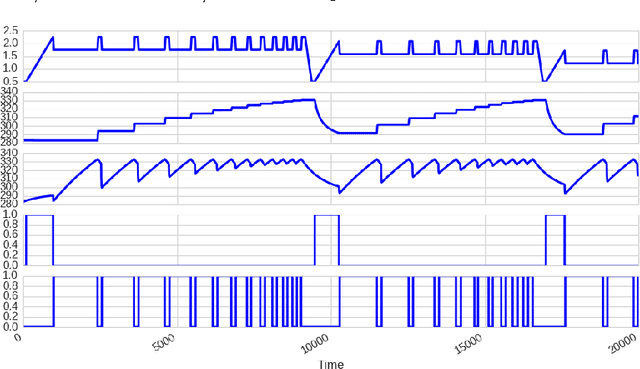
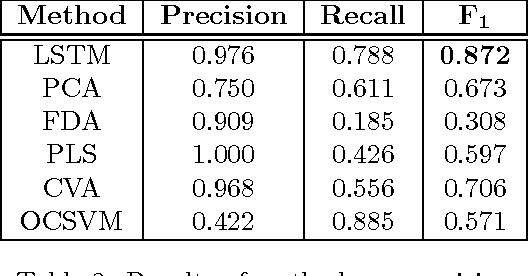
Abstract:We adopted an approach based on an LSTM neural network to monitor and detect faults in industrial multivariate time series data. To validate the approach we created a Modelica model of part of a real gasoil plant. By introducing hacks into the logic of the Modelica model, we were able to generate both the roots and causes of fault behavior in the plant. Having a self-consistent data set with labeled faults, we used an LSTM architecture with a forecasting error threshold to obtain precision and recall quality metrics. The dependency of the quality metric on the threshold level is considered. An appropriate mechanism such as "one handle" was introduced for filtering faults that are outside of the plant operator field of interest.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge