RNN-based Early Cyber-Attack Detection for the Tennessee Eastman Process
Paper and Code
Sep 07, 2017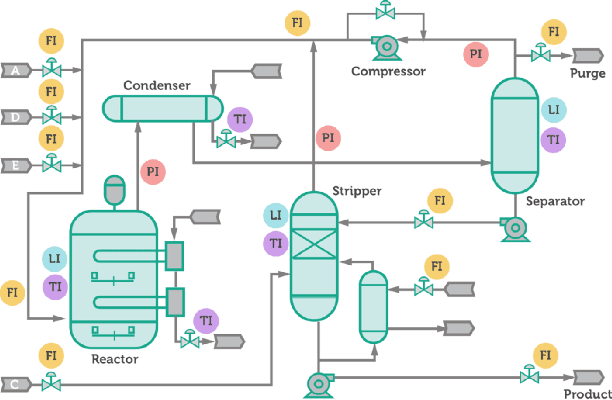
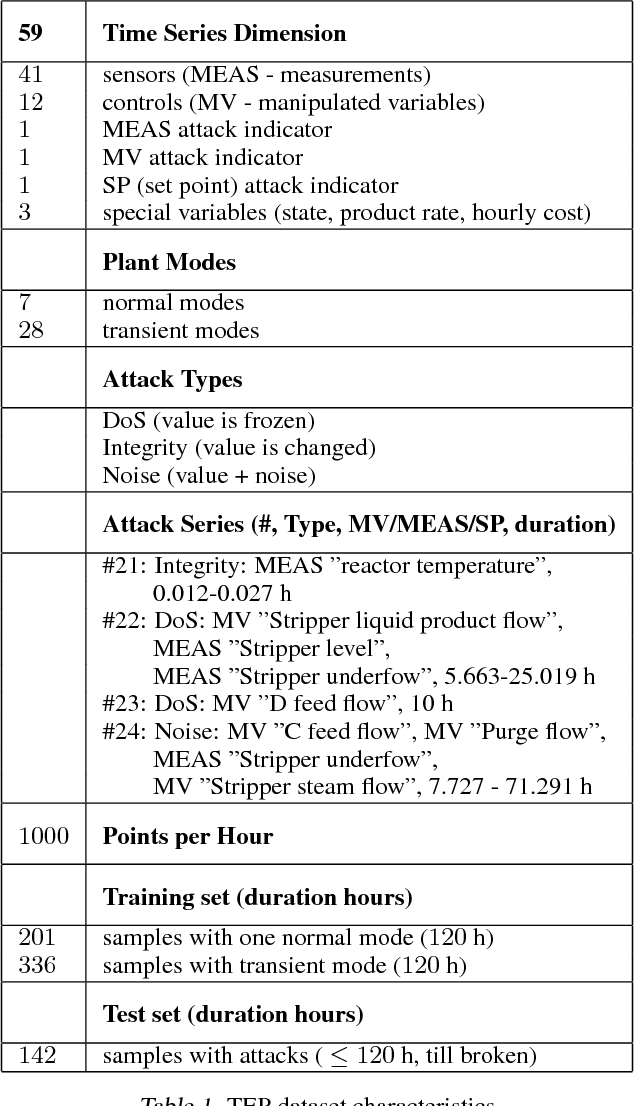
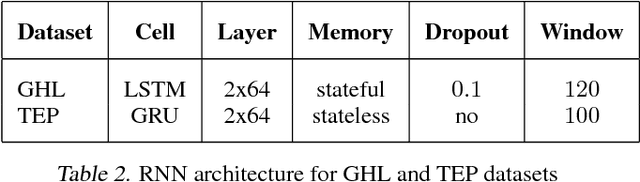
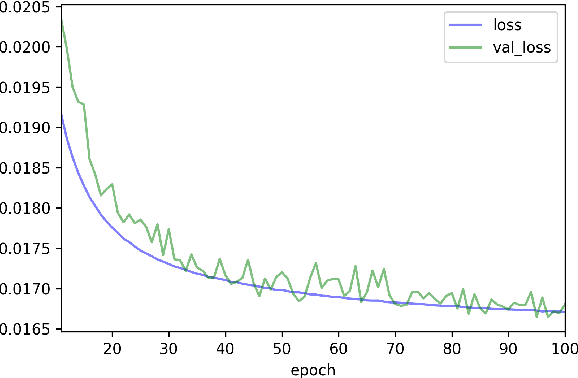
An RNN-based forecasting approach is used to early detect anomalies in industrial multivariate time series data from a simulated Tennessee Eastman Process (TEP) with many cyber-attacks. This work continues a previously proposed LSTM-based approach to the fault detection in simpler data. It is considered necessary to adapt the RNN network to deal with data containing stochastic, stationary, transitive and a rich variety of anomalous behaviours. There is particular focus on early detection with special NAB-metric. A comparison with the DPCA approach is provided. The generated data set is made publicly available.
* ICML 2017 Time Series Workshop, Sydney, Australia, 2017
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge