Nuno Oliveira
Enhancing Machine Learning Performance with Continuous In-Session Ground Truth Scores: Pilot Study on Objective Skeletal Muscle Pain Intensity Prediction
Aug 02, 2023Abstract:Machine learning (ML) models trained on subjective self-report scores struggle to objectively classify pain accurately due to the significant variance between real-time pain experiences and recorded scores afterwards. This study developed two devices for acquisition of real-time, continuous in-session pain scores and gathering of ANS-modulated endodermal activity (EDA).The experiment recruited N = 24 subjects who underwent a post-exercise circulatory occlusion (PECO) with stretch, inducing discomfort. Subject data were stored in a custom pain platform, facilitating extraction of time-domain EDA features and in-session ground truth scores. Moreover, post-experiment visual analog scale (VAS) scores were collected from each subject. Machine learning models, namely Multi-layer Perceptron (MLP) and Random Forest (RF), were trained using corresponding objective EDA features combined with in-session scores and post-session scores, respectively. Over a 10-fold cross-validation, the macro-averaged geometric mean score revealed MLP and RF models trained with objective EDA features and in-session scores achieved superior performance (75.9% and 78.3%) compared to models trained with post-session scores (70.3% and 74.6%) respectively. This pioneering study demonstrates that using continuous in-session ground truth scores significantly enhances ML performance in pain intensity characterization, overcoming ground truth sparsity-related issues, data imbalance, and high variance. This study informs future objective-based ML pain system training.
Deep Learning for Short-term Instant Energy Consumption Forecasting in the Manufacturing Sector
Jul 04, 2022
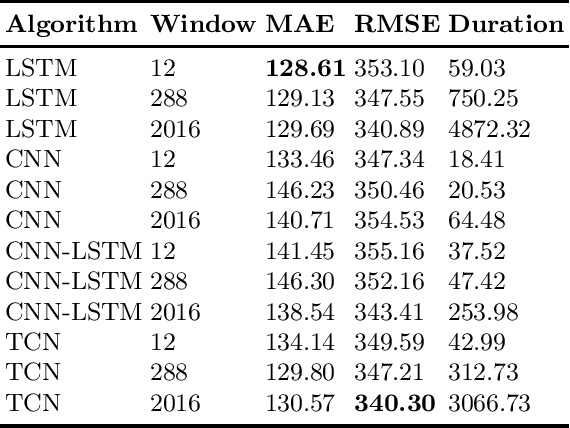
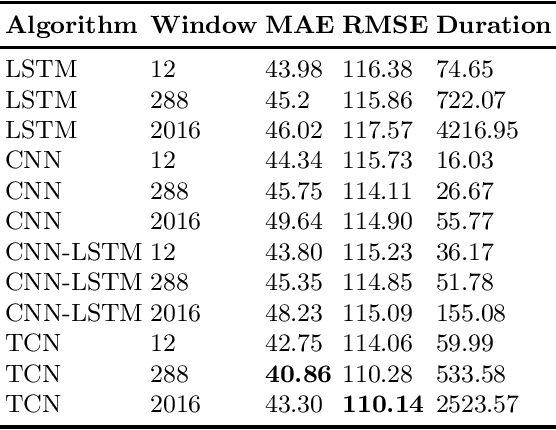
Abstract:Electricity is a volatile power source that requires great planning and resource management for both short and long term. More specifically, in the short-term, accurate instant energy consumption forecasting contributes greatly to improve the efficiency of buildings, opening new avenues for the adoption of renewable energy. In that regard, data-driven approaches, namely the ones based on machine learning, are begin to be preferred over more traditional ones since they provide not only more simplified ways of deployment but also state of the art results. In that sense, this work applies and compares the performance of several deep learning algorithms, LSTM, CNN, mixed CNN-LSTM and TCN, in a real testbed within the manufacturing sector. The experimental results suggest that the TCN is the most reliable method for predicting instant energy consumption in the short-term.
Adaptative Perturbation Patterns: Realistic Adversarial Learning for Robust Intrusion Detection
Mar 29, 2022



Abstract:Adversarial attacks pose a major threat to machine learning and to the systems that rely on it. In the cybersecurity domain, adversarial cyber-attack examples capable of evading detection are especially concerning. Nonetheless, an example generated for a domain with tabular data must be realistic within that domain. This work establishes the fundamental constraint levels required to achieve realism and introduces the Adaptative Perturbation Pattern Method (A2PM) to fulfill these constraints in a gray-box setting. A2PM relies on pattern sequences that are independently adapted to the characteristics of each class to create valid and coherent data perturbations. The proposed method was evaluated in a cybersecurity case study with two scenarios: Enterprise and Internet of Things (IoT) networks. Multilayer Perceptron (MLP) and Random Forest (RF) classifiers were created with regular and adversarial training, using the CIC-IDS2017 and IoT-23 datasets. In each scenario, targeted and untargeted attacks were performed against the classifiers, and the generated examples were compared with the original network traffic flows to assess their realism. The obtained results demonstrate that A2PM provides a scalable generation of realistic adversarial examples, which can be advantageous for both adversarial training and attacks.
A Hybrid Approach for an Interpretable and Explainable Intrusion Detection System
Nov 19, 2021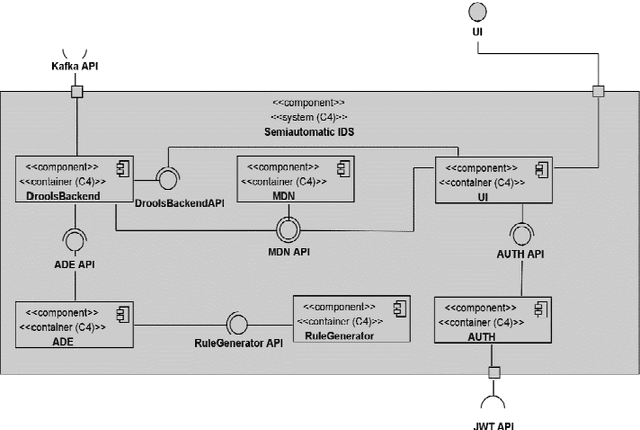


Abstract:Cybersecurity has been a concern for quite a while now. In the latest years, cyberattacks have been increasing in size and complexity, fueled by significant advances in technology. Nowadays, there is an unavoidable necessity of protecting systems and data crucial for business continuity. Hence, many intrusion detection systems have been created in an attempt to mitigate these threats and contribute to a timelier detection. This work proposes an interpretable and explainable hybrid intrusion detection system, which makes use of artificial intelligence methods to achieve better and more long-lasting security. The system combines experts' written rules and dynamic knowledge continuously generated by a decision tree algorithm as new shreds of evidence emerge from network activity.
A Multi-Agent System for Autonomous Mobile Robot Coordination
Sep 25, 2021
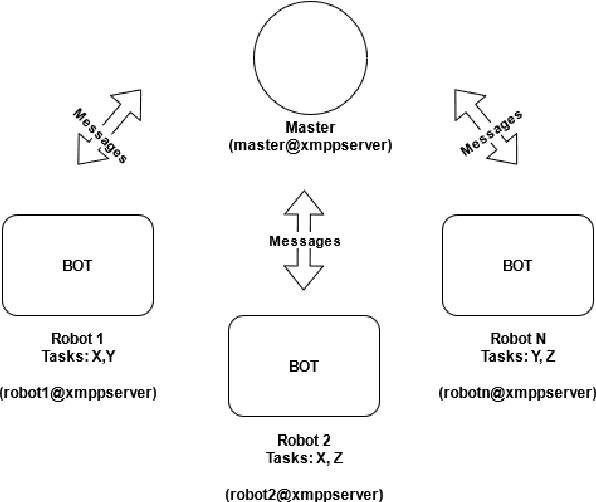
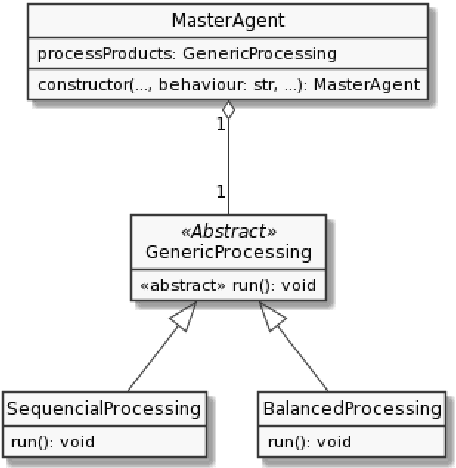
Abstract:The automation of internal logistics and inventory-related tasks is one of the main challenges of modern-day manufacturing corporations since it allows a more effective application of their human resources. Nowadays, Autonomous Mobile Robots (AMR) are state of the art technologies for such applications due to their great adaptability in dynamic environments, replacing more traditional solutions such as Automated Guided Vehicles (AGV), which are quite limited in terms of flexibility and require expensive facility updates for their installation. The application of Artificial Intelligence (AI) to increase AMRs capabilities has been contributing for the development of more sophisticated and efficient robots. Nevertheless, multi-robot coordination and cooperation for solving complex tasks is still a hot research line with increasing interest. This work proposes a Multi-Agent System for coordinating multiple TIAGo robots in tasks related to the manufacturing ecosystem such as the transportation and dispatching of raw materials, finished products and tools. Furthermore, the system is showcased in a realistic simulation using both Gazebo and Robot Operating System (ROS).
A Search Engine for Scientific Publications: a Cybersecurity Case Study
Jun 30, 2021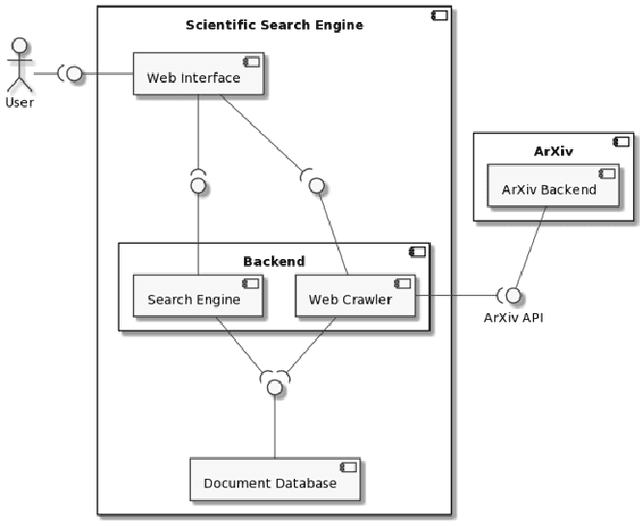
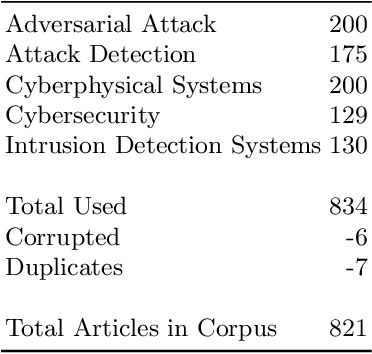
Abstract:Cybersecurity is a very challenging topic of research nowadays, as digitalization increases the interaction of people, software and services on the Internet by means of technology devices and networks connected to it. The field is broad and has a lot of unexplored ground under numerous disciplines such as management, psychology, and data science. Its large disciplinary spectrum and many significant research topics generate a considerable amount of information, making it hard for us to find what we are looking for when researching a particular subject. This work proposes a new search engine for scientific publications which combines both information retrieval and reading comprehension algorithms to extract answers from a collection of domain-specific documents. The proposed solution although being applied to the context of cybersecurity exhibited great generalization capabilities and can be easily adapted to perform under other distinct knowledge domains.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge