Nadeem Ahmed
Examining the Rat in the Tunnel: Interpretable Multi-Label Classification of Tor-based Malware
Sep 25, 2024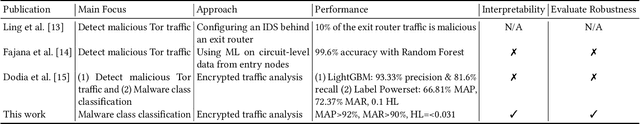
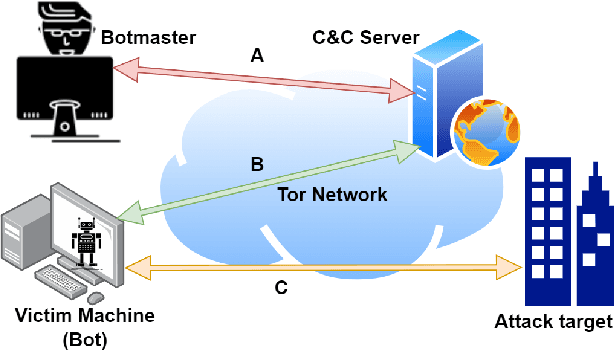
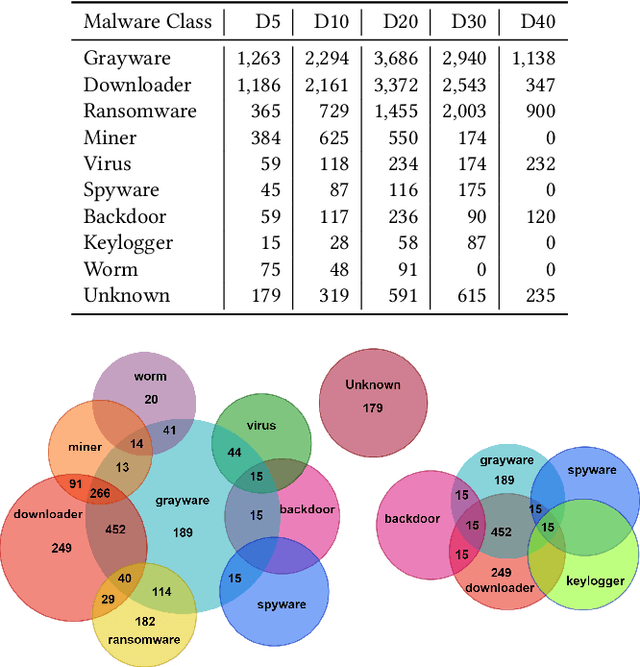
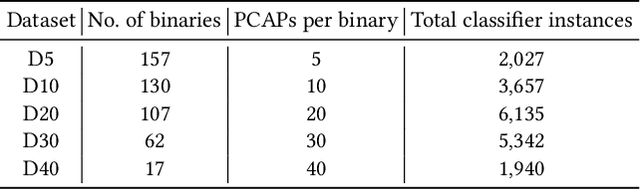
Abstract:Despite being the most popular privacy-enhancing network, Tor is increasingly adopted by cybercriminals to obfuscate malicious traffic, hindering the identification of malware-related communications between compromised devices and Command and Control (C&C) servers. This malicious traffic can induce congestion and reduce Tor's performance, while encouraging network administrators to block Tor traffic. Recent research, however, demonstrates the potential for accurately classifying captured Tor traffic as malicious or benign. While existing efforts have addressed malware class identification, their performance remains limited, with micro-average precision and recall values around 70%. Accurately classifying specific malware classes is crucial for effective attack prevention and mitigation. Furthermore, understanding the unique patterns and attack vectors employed by different malware classes helps the development of robust and adaptable defence mechanisms. We utilise a multi-label classification technique based on Message-Passing Neural Networks, demonstrating its superiority over previous approaches such as Binary Relevance, Classifier Chains, and Label Powerset, by achieving micro-average precision (MAP) and recall (MAR) exceeding 90%. Compared to previous work, we significantly improve performance by 19.98%, 10.15%, and 59.21% in MAP, MAR, and Hamming Loss, respectively. Next, we employ Explainable Artificial Intelligence (XAI) techniques to interpret the decision-making process within these models. Finally, we assess the robustness of all techniques by crafting adversarial perturbations capable of manipulating classifier predictions and generating false positives and negatives.
Intelligence at the Extreme Edge: A Survey on Reformable TinyML
Apr 02, 2022


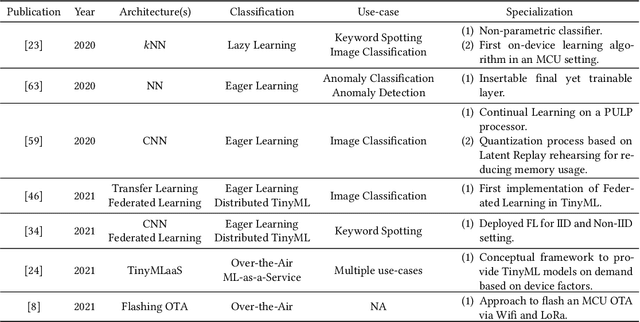
Abstract:The rapid miniaturization of Machine Learning (ML) for low powered processing has opened gateways to provide cognition at the extreme edge (E.g., sensors and actuators). Dubbed Tiny Machine Learning (TinyML), this upsurging research field proposes to democratize the use of Machine Learning (ML) and Deep Learning (DL) on frugal Microcontroller Units (MCUs). MCUs are highly energy-efficient pervasive devices capable of operating with less than a few Milliwatts of power. Nevertheless, many solutions assume that TinyML can only run inference. Despite this, growing interest in TinyML has led to work that makes them reformable, i.e., work that permits TinyML to improve once deployed. In line with this, roadblocks in MCU based solutions in general, such as reduced physical access and long deployment periods of MCUs, deem reformable TinyML to play a significant part in more effective solutions. In this work, we present a survey on reformable TinyML solutions with the proposal of a novel taxonomy for ease of separation. Here, we also discuss the suitability of each hierarchical layer in the taxonomy for allowing reformability. In addition to these, we explore the workflow of TinyML and analyze the identified deployment schemes and the scarcely available benchmarking tools. Furthermore, we discuss how reformable TinyML can impact a few selected industrial areas and discuss the challenges and future directions.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge