Mohammad Almseidin
Fuzzy Rule Interpolation Toolbox for the GNU Open-Source OCTAVE
Dec 10, 2019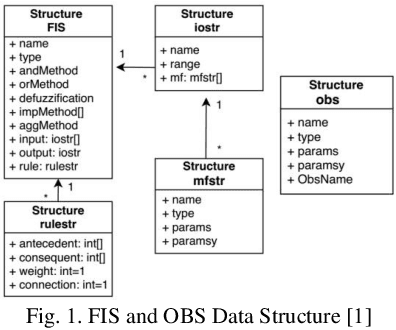
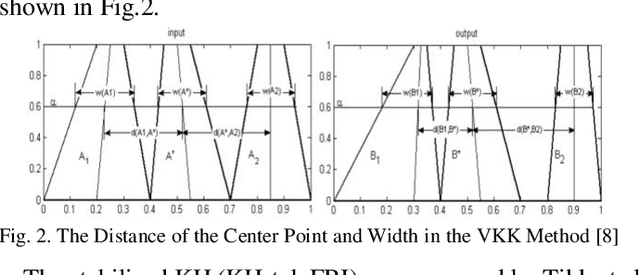
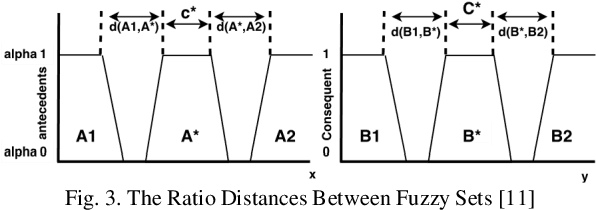
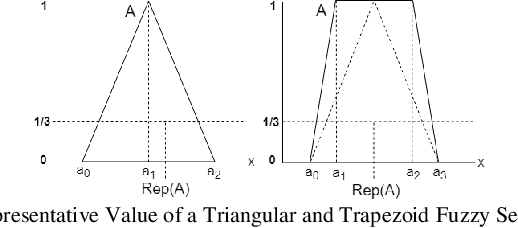
Abstract:In most fuzzy control applications (applying classical fuzzy reasoning), the reasoning method requires a complete fuzzy rule-base, i.e all the possible observations must be covered by the antecedents of the fuzzy rules, which is not always available. Fuzzy control systems based on the Fuzzy Rule Interpolation (FRI) concept play a major role in different platforms, in case if only a sparse fuzzy rule-base is available. This cases the fuzzy model contains only the most relevant rules, without covering all the antecedent universes. The first FRI toolbox being able to handle different FRI methods was developed by Johanyak et. al. in 2006 for the MATLAB environment. The goal of this paper is to introduce some details of the adaptation of the FRI toolbox to support the GNU/OCTAVE programming language. The OCTAVE Fuzzy Rule Interpolation (OCTFRI) Toolbox is an open-source toolbox for OCTAVE programming language, providing a large functionally compatible subset of the MATLAB FRI toolbox as well as many extensions. The OCTFRI Toolbox includes functions that enable the user to evaluate Fuzzy Inference Systems (FISs) from the command line and from OCTAVE scripts, read/write FISs and OBS to/from files, and produce a graphical visualisation of both the membership functions and the FIS outputs. Future work will focus on implementing advanced fuzzy inference techniques and GUI tools.
Intensive Preprocessing of KDD Cup 99 for Network Intrusion Classification Using Machine Learning Techniques
Oct 05, 2018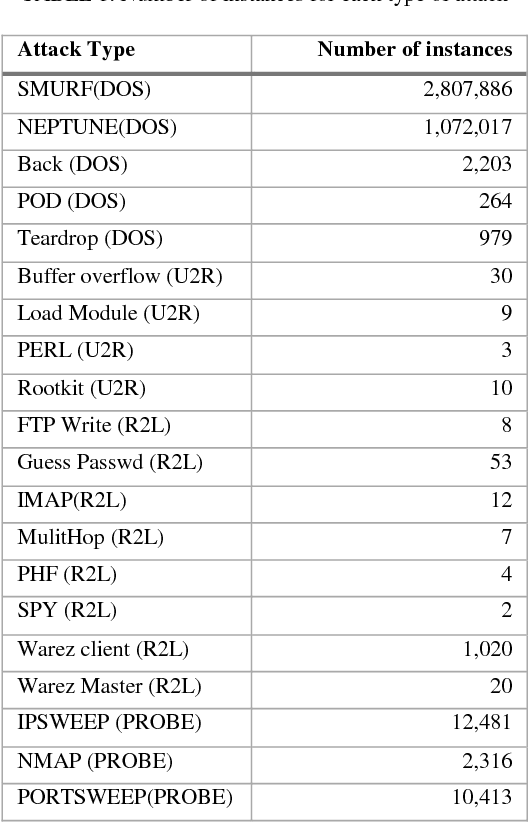
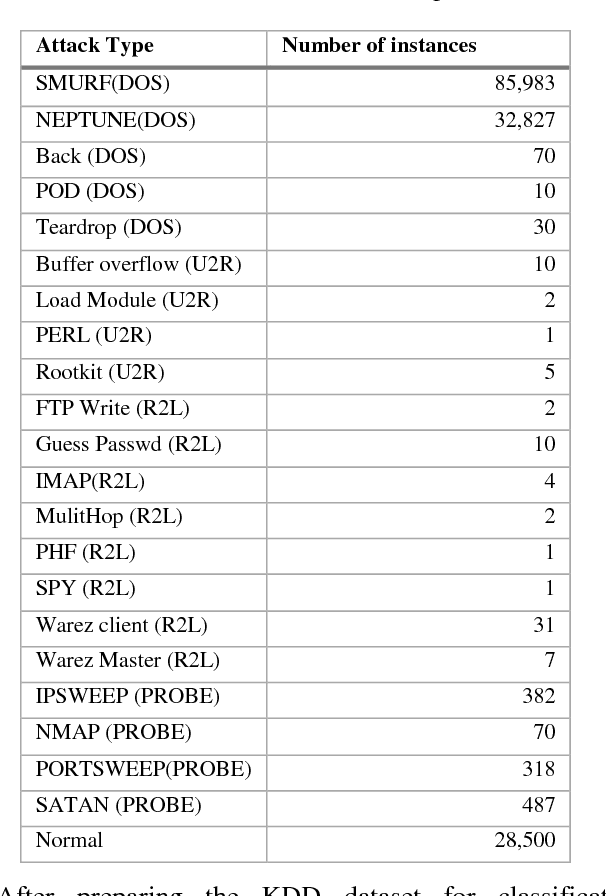
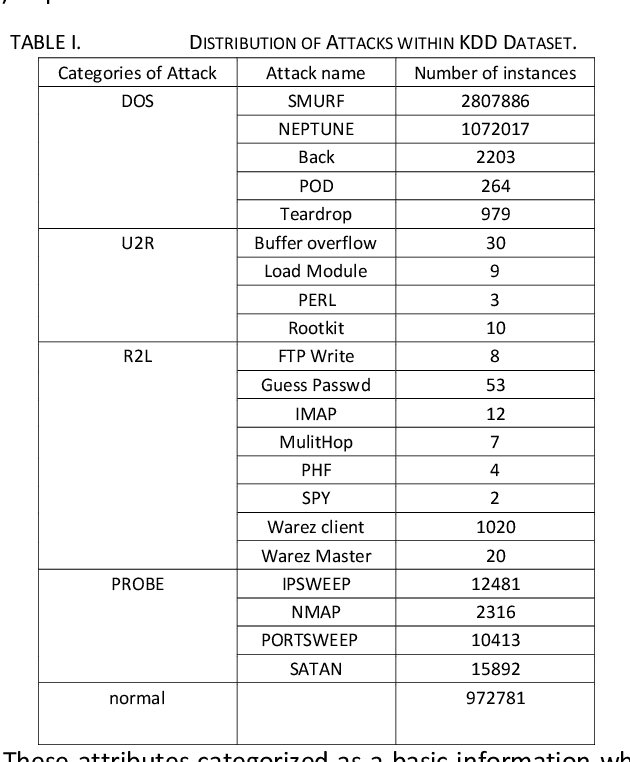
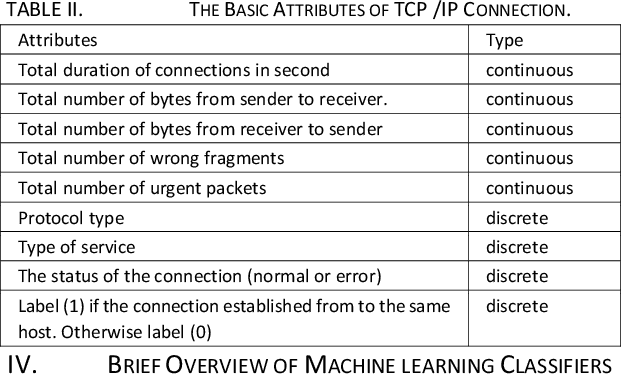
Abstract:Network security engineers work to keep services available all the time by handling intruder attacks. Intrusion Detection System (IDS) is one of the obtainable mechanism that used to sense and classify any abnormal actions. Therefore, the IDS must be always up to date with the latest intruder attacks signatures to preserve confidentiality, integrity and availability of the services. The speed of the IDS is very important issue as well learning the new attacks. This research work illustrates how the Knowledge Discovery and Data Mining (or Knowledge Discovery in Databases) KDD dataset is very handy for testing and evaluating different Machine Learning Techniques. It mainly focuses on the KDD preprocess part in order to prepare a decent and fair experimental data set. The techniques J48, Random Forest, Random Tree, MLP, Na\"ive Bayes and Bayes Network classifiers have been chosen for this study. It has been proven that the Random forest classifier has achieved the highest accuracy rate for detecting and classifying all KDD dataset attacks, which are of type (DOS, R2L, U2R, and PROBE)
Evaluation of Machine Learning Algorithms for Intrusion Detection System
Jan 08, 2018
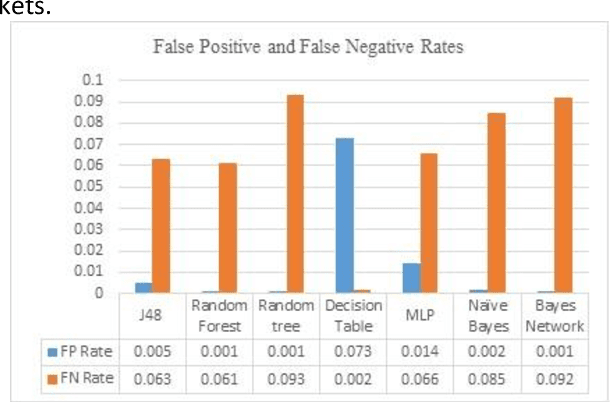
Abstract:Intrusion detection system (IDS) is one of the implemented solutions against harmful attacks. Furthermore, attackers always keep changing their tools and techniques. However, implementing an accepted IDS system is also a challenging task. In this paper, several experiments have been performed and evaluated to assess various machine learning classifiers based on KDD intrusion dataset. It succeeded to compute several performance metrics in order to evaluate the selected classifiers. The focus was on false negative and false positive performance metrics in order to enhance the detection rate of the intrusion detection system. The implemented experiments demonstrated that the decision table classifier achieved the lowest value of false negative while the random forest classifier has achieved the highest average accuracy rate.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge