Mouhammd Al-kasassbeh
Detecting Network Anomalies using Rule-based machine learning within SNMP-MIB dataset
Jan 18, 2020
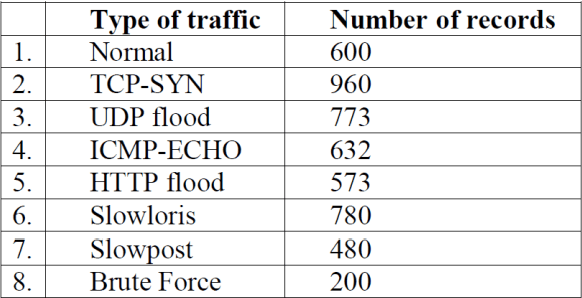

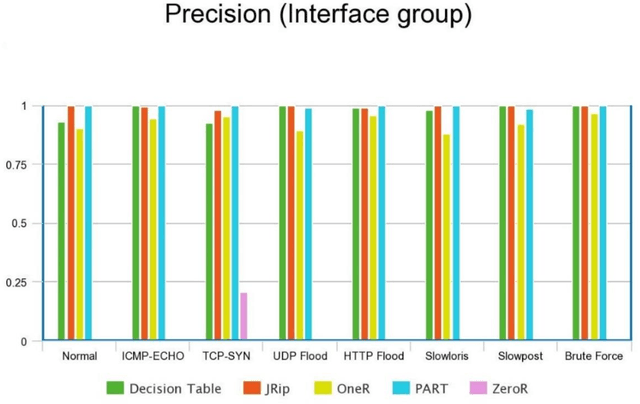
Abstract:One of the most effective threats that targeting cybercriminals to limit network performance is Denial of Service (DOS) attack. Thus, data security, completeness and efficiency could be greatly damaged by this type of attacks. This paper developed a network traffic system that relies on adopted dataset to differentiate the DOS attacks from normal traffic. The detection model is built with five Rule-based machine learning classifiers (DecisionTable, JRip, OneR, PART and ZeroR). The findings have shown that the ICMP variables are implemented in the identification of ICMP attack, HTTP flood attack, and Slowloris at a high accuracy of approximately 99.7% using PART classifier. In addition, PART classifier has succeeded in classifying normal traffic from different DOS attacks at 100%.
Intensive Preprocessing of KDD Cup 99 for Network Intrusion Classification Using Machine Learning Techniques
Oct 05, 2018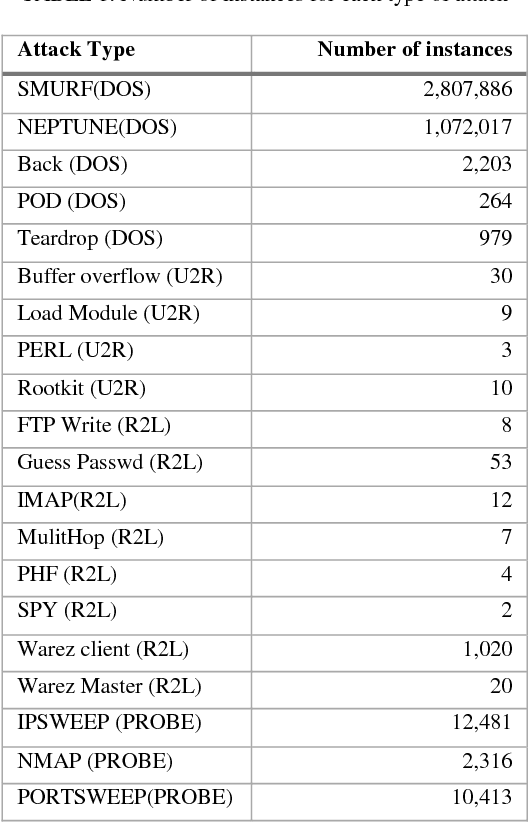
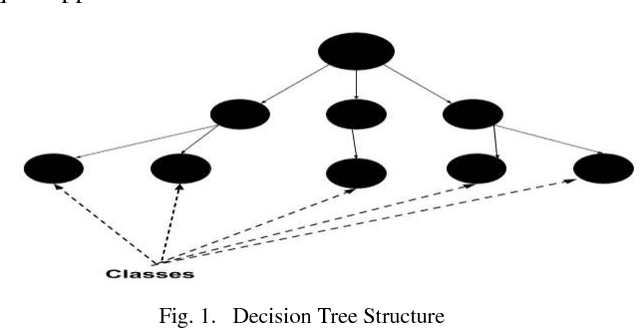
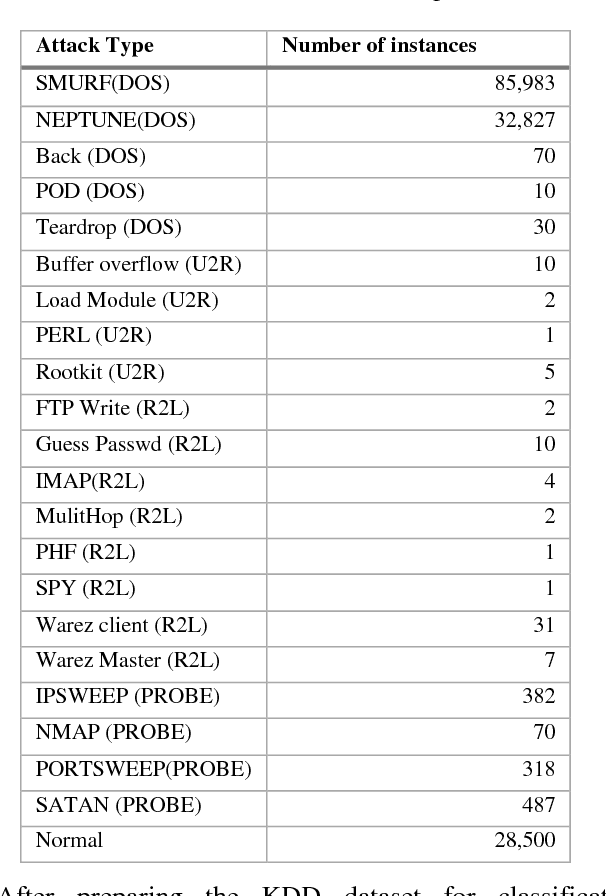
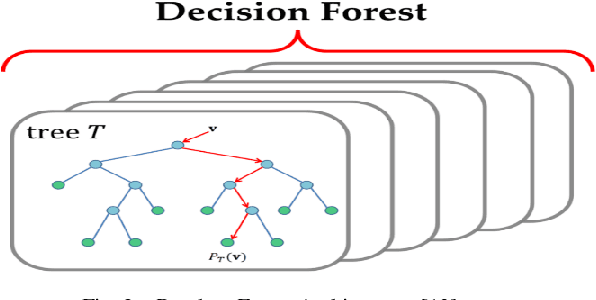
Abstract:Network security engineers work to keep services available all the time by handling intruder attacks. Intrusion Detection System (IDS) is one of the obtainable mechanism that used to sense and classify any abnormal actions. Therefore, the IDS must be always up to date with the latest intruder attacks signatures to preserve confidentiality, integrity and availability of the services. The speed of the IDS is very important issue as well learning the new attacks. This research work illustrates how the Knowledge Discovery and Data Mining (or Knowledge Discovery in Databases) KDD dataset is very handy for testing and evaluating different Machine Learning Techniques. It mainly focuses on the KDD preprocess part in order to prepare a decent and fair experimental data set. The techniques J48, Random Forest, Random Tree, MLP, Na\"ive Bayes and Bayes Network classifiers have been chosen for this study. It has been proven that the Random forest classifier has achieved the highest accuracy rate for detecting and classifying all KDD dataset attacks, which are of type (DOS, R2L, U2R, and PROBE)
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge