Laura Anitori
Sensor Selection using the Two-Target Cramér-Rao Bound for Angle of Arrival Estimation
Jul 31, 2023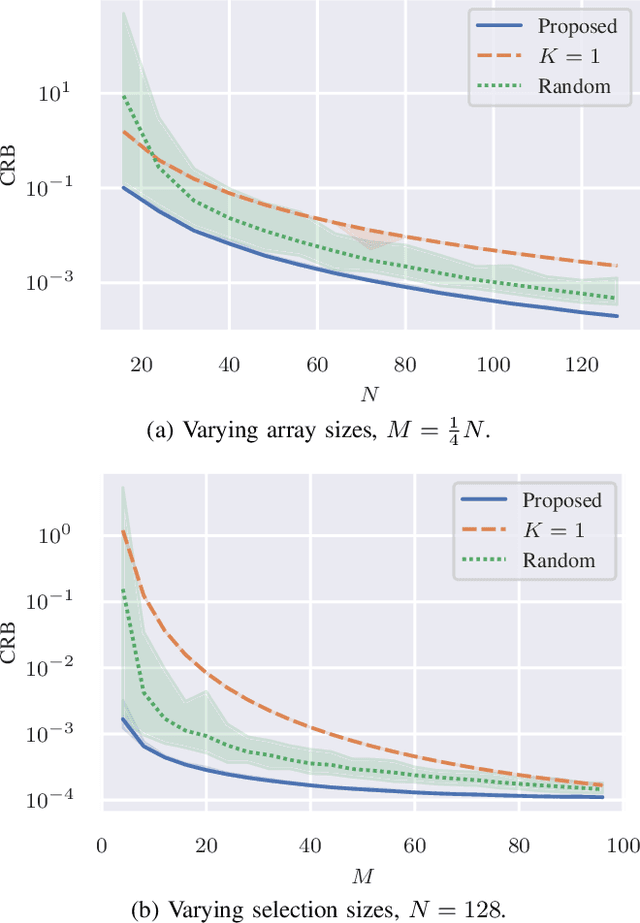
Abstract:Sensor selection is a useful method to help reduce data throughput, as well as computational, power, and hardware requirements, while still maintaining acceptable performance. Although minimizing the Cram\'er-Rao bound has been adopted previously for sparse sensing, it did not consider multiple targets and unknown source models. We propose to tackle the sensor selection problem for angle of arrival estimation using the worst-case Cram\'er-Rao bound of two uncorrelated sources. We cast the problem as a convex semi-definite program and retrieve the binary selection by randomized rounding. Through numerical examples related to a linear array, we illustrate the proposed method and show that it leads to the selection of elements at the edges plus the center of the linear array.
Run-Time Monitors Design for Adaptive Radar Systems: A Practical Framework
Feb 20, 2023


Abstract:Adaptivity in multi-function radar systems is rapidly increasing, especially when moving towards fully adaptive, cognitive radar systems. However, the large number of available system configurations makes the rigorous verification and certification process during the testing phase, deployment, and after hardware and software upgrades, challenging, if not infeasible. To alleviate the verification process, run-time verification can be applied to oversee the correct function of a system during its operation as done in applications where on-the-fly reconfiguration/adaptation is pervasive, e.g., spacecrafts and self-driving cars. Though possible, the application of run-time verification into a radar system is not straightforward, e.g., when verifying (adaptive) radar resource managers or performance measures, such as track initiation time in dynamic environments. The goal of this paper is to introduce a framework to identify, characterize, and map the various aspects necessary for implementing run-time verification for (components of) multi-function radar systems. The proposed framework can be used by radar practitioners and researchers for applying run-time-verification to adaptive, re-configurable radar systems. In addition, we discuss how run-time verification can be leveraged to gather new insights from operational data to improve functionalities in upcoming update cycles and present an example of a verifier designed using the introduced framework.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge