Karthik Upadhya
Downlink Power Control based UE-Sided Initial Access for Tactical 5G NR
May 22, 2024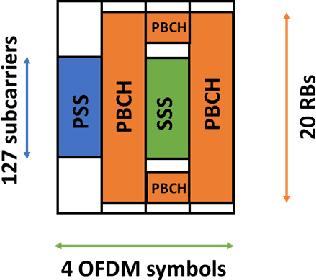
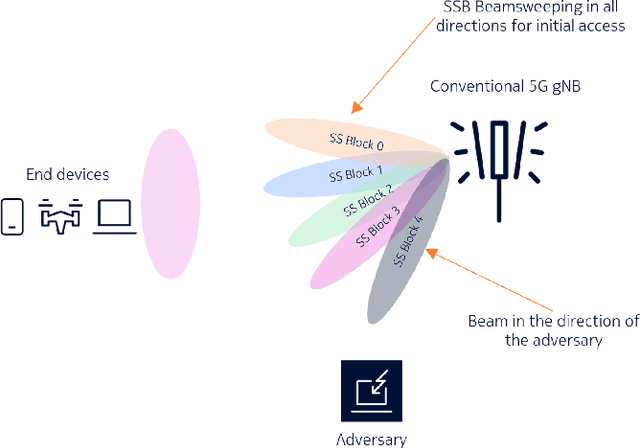
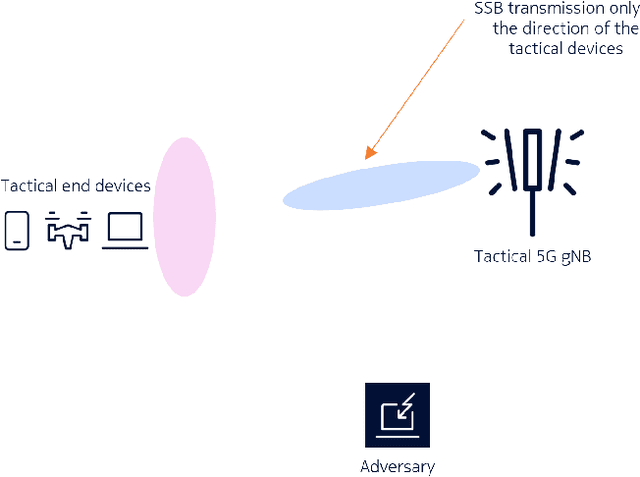
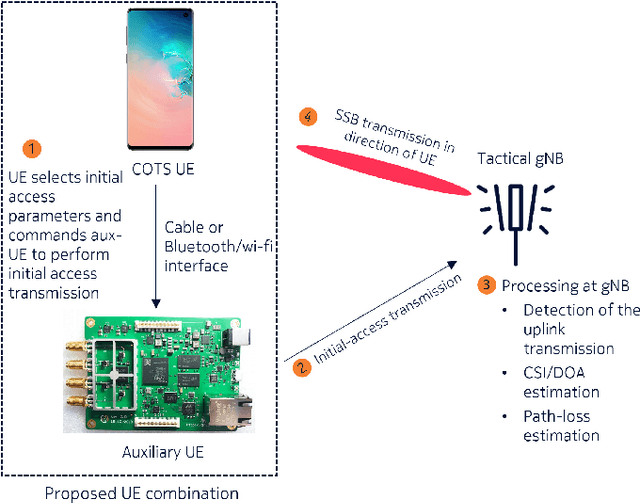
Abstract:Communication technologies play a crucial role in battlefields. They are an inalienable part of any tactical response, whether at the battlefront or inland. Such scenarios require that the communication technologies be versatile, scalable, cost-effective, and stealthy. While multiple studies and past products have tried to address these requirements, none of them have been able to solve all the four challenges simultaneously. Hence, in this paper, we propose a tactical solution that is based on the versatile, scalable, and cost effective 5G NR system. Our focus is on the initial-access phase which is subject to a high probability of detection by an eavesdropper. To address this issue, we propose some modifications to how the UE performs initial access that lower the probability of detection while not affecting standards compliance and not requiring any modifications to the user equipment (UE) chipset implementation. Further, we demonstrate that with a simple downlink power control algorithm, we reduce the probability of detection at an eavesdropper. The result is a 5G NR based initial-access method that improves stealthiness when compared with a vanilla 5G NR implementation.
Demystifying 5G NR Downlink Synchronization for Tactical Networks
May 21, 2024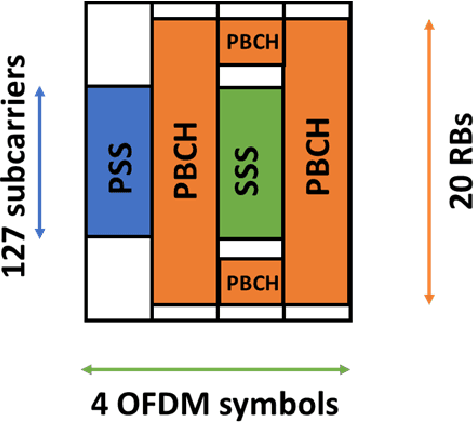
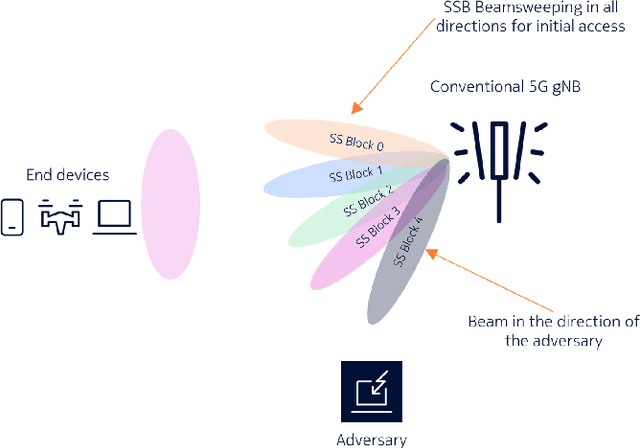
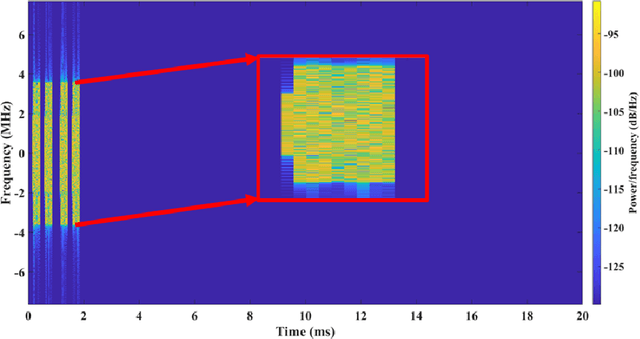
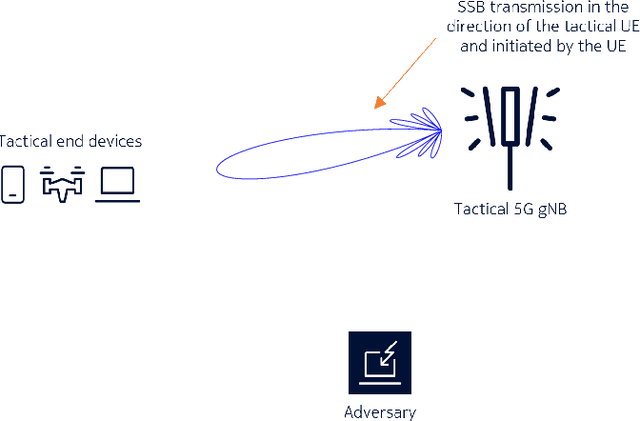
Abstract:5G NR is touted to be an attractive candidate for tactical networks owing to its versatility, scalability, and low cost. However, tactical networks need to be stealthy, where an adversary is not able to detect or intercept the tactical communication. In this paper, we investigate the stealthiness of 5G NR by looking at the probability with which an adversary that monitors the downlink synchronization signals can detect the presence of the network. We simulate a single-cell single-eavesdropper scenario and evaluate the probability with which the eavesdropper can detect the synchronization signal block when using either a correlator or an energy detector. We show that this probability is close to $ 100 $% suggesting that 5G out-of-the-box is not suitable for a tactical network. We then propose methods that lower this value without affecting the performance of a legitimate tactical UE.
Jamming Resilient Indoor Factory Deployments: Design and Performance Evaluation
Feb 02, 2022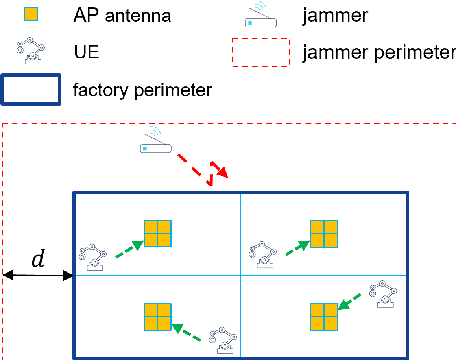
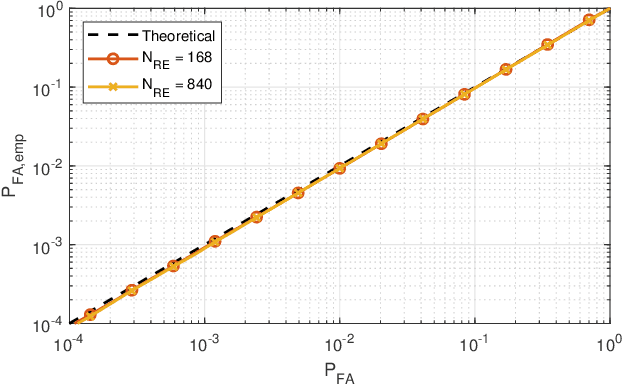
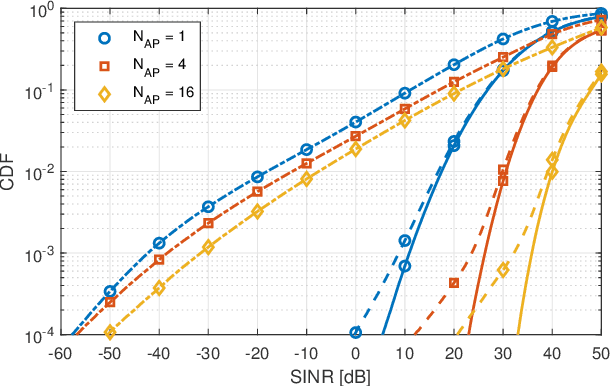
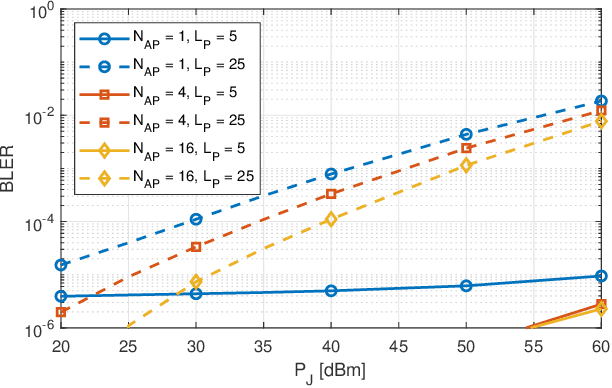
Abstract:In the framework of 5G-and-beyond Industry 4.0, jamming attacks for denial of service are a rising threat which can severely compromise the system performance. Therefore, in this paper we deal with the problem of jamming detection and mitigation in indoor factory deployments. We design two jamming detectors based on pseudo-random blanking of subcarriers with orthogonal frequency division multiplexing and consider jamming mitigation with frequency hopping and random scheduling of the user equipments. We then evaluate the performance of the system in terms of achievable BLER with ultra-reliable low-latency communications traffic and jamming missed detection probability. Simulations are performed considering a 3rd Generation Partnership Project spatial channel model for the factory floor with a jammer stationed outside the plant trying to disrupt the communication inside the factory. Numerical results show that jamming resiliency increases when using a distributed access point deployment and exploiting channel correlation among antennas for jamming detection, while frequency hopping is helpful in jamming mitigation only for strict BLER requirements.
Jamming Detection With Subcarrier Blanking for 5G and Beyond in Industry 4.0 Scenarios
Jun 15, 2021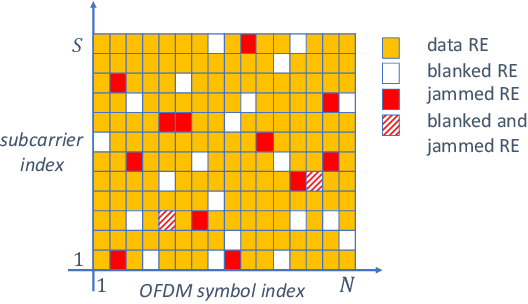
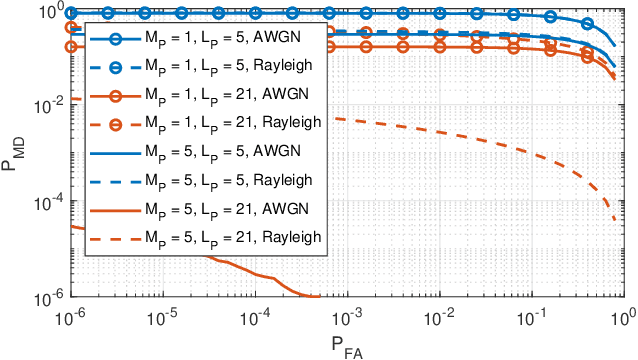
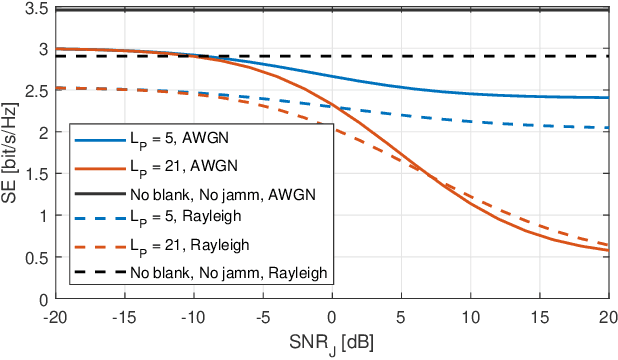
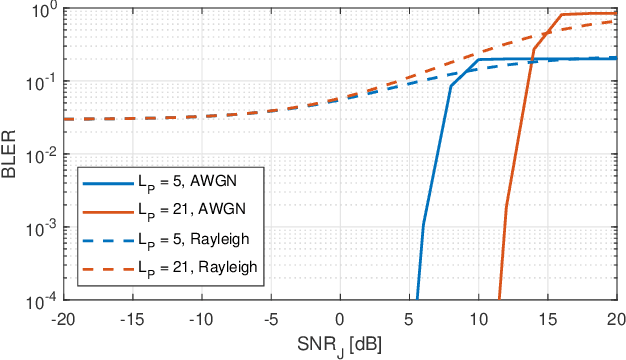
Abstract:Security attacks at the physical layer, in the form of radio jamming for denial of service, are an increasing threat in the Industry 4.0 scenarios. In this paper, we consider the problem of jamming detection in 5G-and-beyond communication systems and propose a defense mechanism based on pseudo-random blanking of subcarriers with orthogonal frequency division multiplexing (OFDM). We then design a detector by applying the generalized likelihood ratio test (GLRT) on those subcarriers. We finally evaluate the performance of the proposed technique against a smart jammer, which is pursuing one of the following objectives: maximize stealthiness, minimize spectral efficiency (SE) with mobile broadband (MBB) type of traffic, and maximize block error rate (BLER) with ultra-reliable low-latency communications (URLLC). Numerical results show that a smart jammer a) needs to compromise between missed detection (MD) probability and SE reduction with MBB and b) can achieve low detectability and high system performance degradation with URLLC only if it has sufficiently high power.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge