Gueltoum Bendiab
BotSpot: Deep Learning Classification of Bot Accounts within Twitter
Sep 08, 2021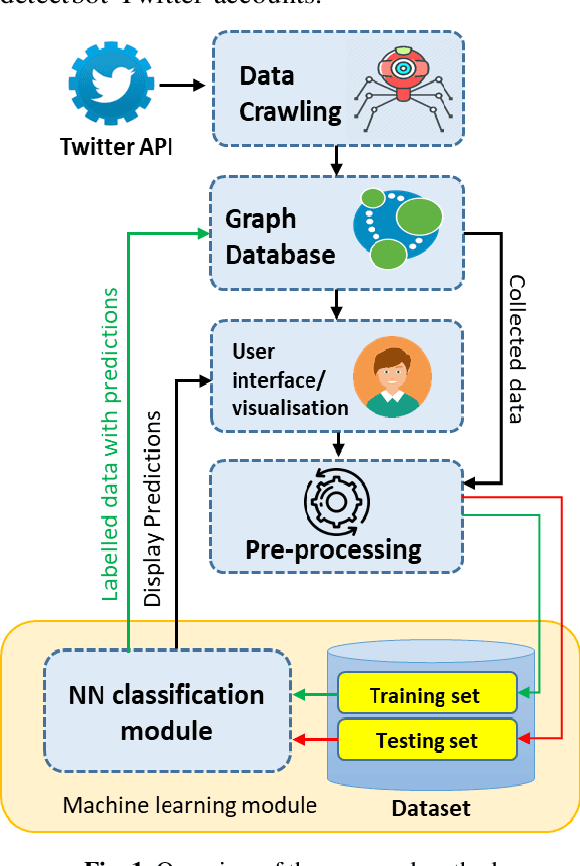



Abstract:The openness feature of Twitter allows programs to generate and control Twitter accounts automatically via the Twitter API. These accounts, which are known as bots, can automatically perform actions such as tweeting, re-tweeting, following, unfollowing, or direct messaging other accounts, just like real people. They can also conduct malicious tasks such as spreading of fake news, spams, malicious software and other cyber-crimes. In this paper, we introduce a novel bot detection approach using deep learning, with the Multi-layer Perceptron Neural Networks and nine features of a bot account. A web crawler is developed to automatically collect data from public Twitter accounts and build the testing and training datasets, with 860 samples of human and bot accounts. After the initial training is done, the Multilayer Perceptron Neural Networks achieved an overall accuracy rate of 92%, which proves the performance of the proposed approach.
* 7 pages, 3 figures, 2 tables
Insider Detection using Deep Autoencoder and Variational Autoencoder Neural Networks
Sep 06, 2021



Abstract:Insider attacks are one of the most challenging cybersecurity issues for companies, businesses and critical infrastructures. Despite the implemented perimeter defences, the risk of this kind of attack is still very high. In fact, the detection of insider attacks is a very complicated security task and presents a serious challenge to the research community. In this paper, we aim to address this issue by using deep learning algorithms Autoencoder and Variational Autoencoder deep. We will especially investigate the usefulness of applying these algorithms to automatically defend against potential internal threats, without human intervention. The effectiveness of these two models is evaluated on the public dataset CERT dataset (CERT r4.2). This version of the CERT Insider Threat Test dataset includes both benign and malicious activities generated from 1000 simulated users. The comparison results with other models show that the Variational Autoencoder neural network provides the best overall performance with a greater detection accuracy and a reasonable false positive rate
* 7 pages, 3 figures, 3 tables
Intrusion Detection using Network Traffic Profiling and Machine Learning for IoT
Sep 06, 2021



Abstract:The rapid increase in the use of IoT devices brings many benefits to the digital society, ranging from improved efficiency to higher productivity. However, the limited resources and the open nature of these devices make them vulnerable to various cyber threats. A single compromised device can have an impact on the whole network and lead to major security and physical damages. This paper explores the potential of using network profiling and machine learning to secure IoT against cyber-attacks. The proposed anomaly-based intrusion detection solution dynamically and actively profiles and monitors all networked devices for the detection of IoT device tampering attempts as well as suspicious network transactions. Any deviation from the defined profile is considered to be an attack and is subject to further analysis. Raw traffic is also passed on to the machine learning classifier for examination and identification of potential attacks. Performance assessment of the proposed methodology is conducted on the Cyber-Trust testbed using normal and malicious network traffic. The experimental results show that the proposed anomaly detection system delivers promising results with an overall accuracy of 98.35% and 0.98% of false-positive alarms.
* 11 pages, 4 figures, 2 tables
Detection of Insider Threats using Artificial Intelligence and Visualisation
Sep 06, 2021



Abstract:Insider threats are one of the most damaging risk factors for the IT systems and infrastructure of a company or an organization; identification of insider threats has prompted the interest of the world academic research community, with several solutions having been proposed to alleviate their potential impact. For the implementation of the experimental stage described in this study, the Convolutional Neural Network (from now on CNN) algorithm was used and implemented via the Google TensorFlow program, which was trained to identify potential threats from images produced by the available dataset. From the examination of the images that were produced and with the help of Machine Learning, the question of whether the activity of each user is classified as malicious or not for the Information System was answered.
* 8 pages, 5 figures, 1 table
CHAINGE: A Blockchain Solution to Automate Payment Detail Updates to Subscription Services
Aug 28, 2021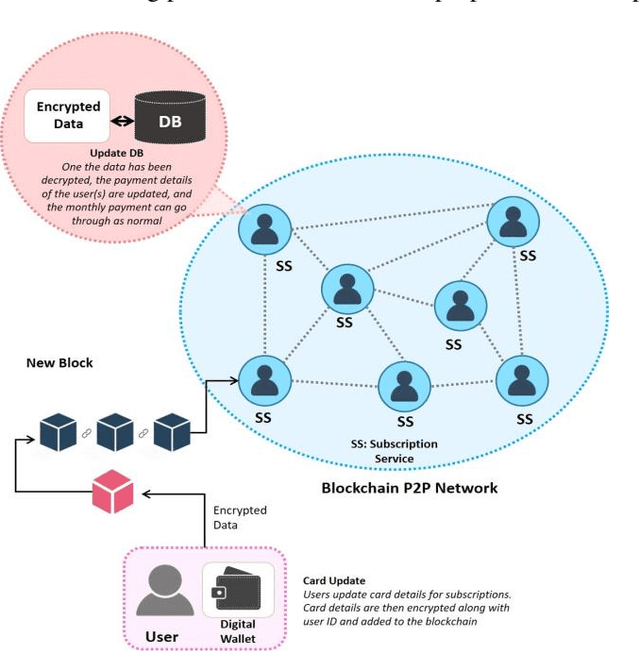
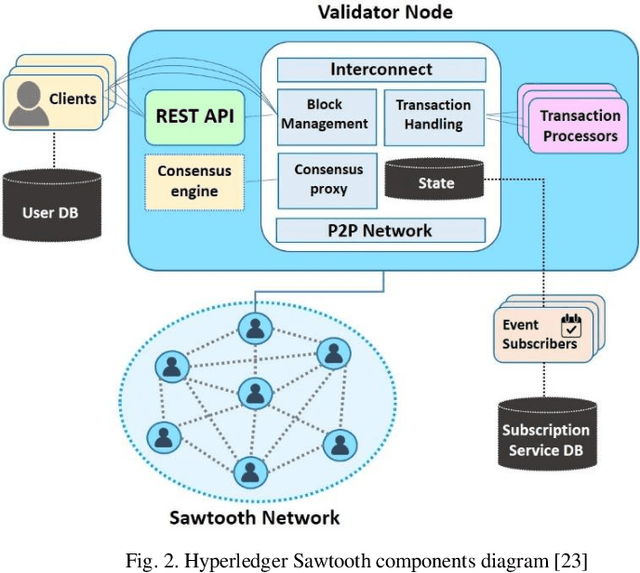
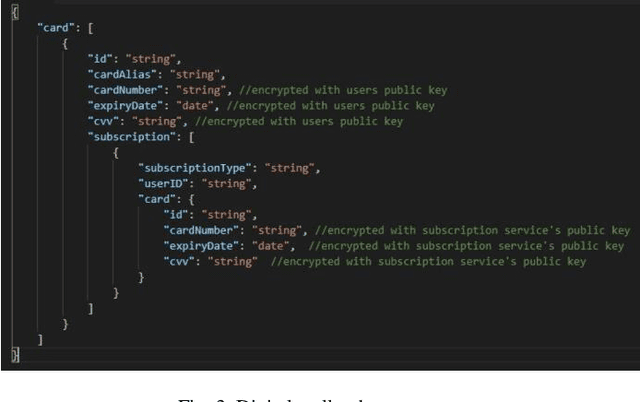
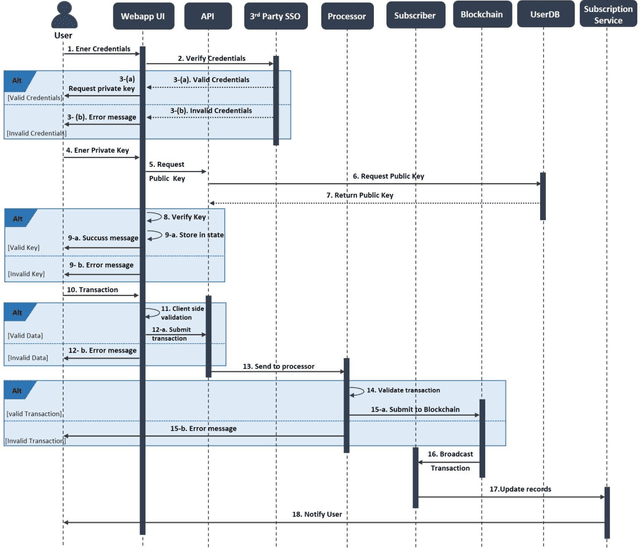
Abstract:The rise of the subscription-based business model has led to a corresponding increase in the number of subscriptions where a customer needs to manage their payments. This management of payments for multiple subscriptions has become a very complicated and insecure task for customers, especially when it comes to renewing payment details when the card is lost, stolen, or expires. In addition, this, mostly manual, process is vulnerable to human error, digital frauds, and data breaches, according to security reports. Thus, in this paper, we propose a novel approach to automate, manage and simplify the Financial Supply Chain involved in the process of updating and managing payments to user subscriptions. This is done by utilising the Hyperledger Sawtooth blockchain framework, that allows a consumer to enter their payment card details in a central digital wallet and link their subscriptions to their cards. The card being updated triggers an event on the blockchain, which allow for the payment details to be updated on subscription systems automatically. The verification tests performed on the prototype of the proposed system shows that its current implementation has been securely achieved.
* 7 pages, 4 figures, 1 table
IoT Malware Network Traffic Classification using Visual Representation and Deep Learning
Oct 04, 2020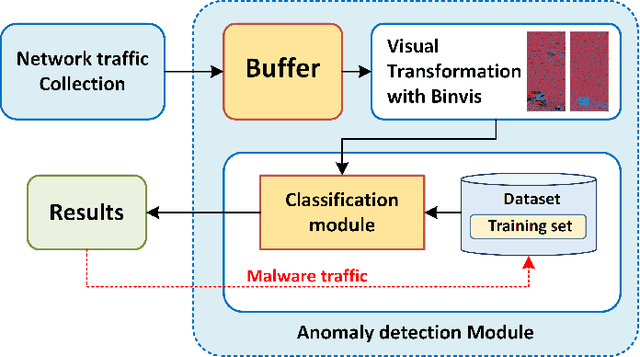

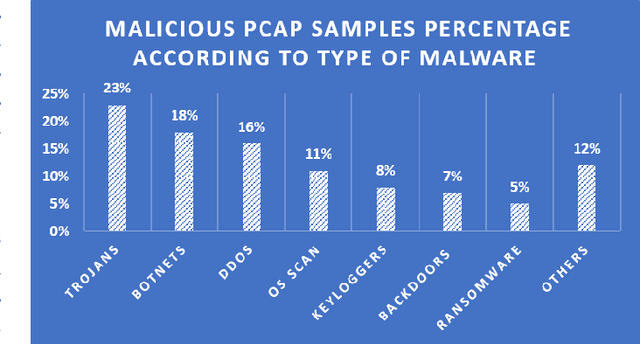
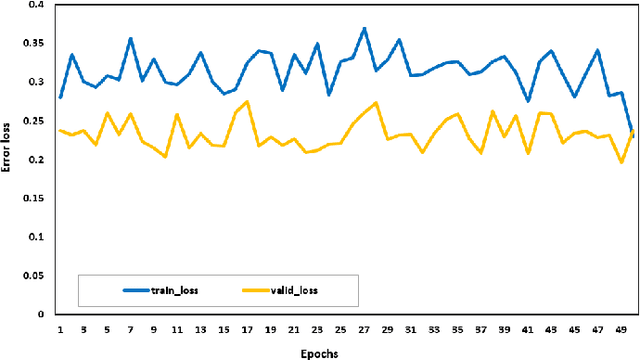
Abstract:With the increase of IoT devices and technologies coming into service, Malware has risen as a challenging threat with increased infection rates and levels of sophistication. Without strong security mechanisms, a huge amount of sensitive data is exposed to vulnerabilities, and therefore, easily abused by cybercriminals to perform several illegal activities. Thus, advanced network security mechanisms that are able of performing a real-time traffic analysis and mitigation of malicious traffic are required. To address this challenge, we are proposing a novel IoT malware traffic analysis approach using deep learning and visual representation for faster detection and classification of new malware (zero-day malware). The detection of malicious network traffic in the proposed approach works at the package level, significantly reducing the time of detection with promising results due to the deep learning technologies used. To evaluate our proposed method performance, a dataset is constructed which consists of 1000 pcap files of normal and malware traffic that are collected from different network traffic sources. The experimental results of Residual Neural Network (ResNet50) are very promising, providing a 94.50% accuracy rate for detection of malware traffic.
* 10 pages, 5 figures, 2 tables
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge