Nick Savage
BotSpot: Deep Learning Classification of Bot Accounts within Twitter
Sep 08, 2021



Abstract:The openness feature of Twitter allows programs to generate and control Twitter accounts automatically via the Twitter API. These accounts, which are known as bots, can automatically perform actions such as tweeting, re-tweeting, following, unfollowing, or direct messaging other accounts, just like real people. They can also conduct malicious tasks such as spreading of fake news, spams, malicious software and other cyber-crimes. In this paper, we introduce a novel bot detection approach using deep learning, with the Multi-layer Perceptron Neural Networks and nine features of a bot account. A web crawler is developed to automatically collect data from public Twitter accounts and build the testing and training datasets, with 860 samples of human and bot accounts. After the initial training is done, the Multilayer Perceptron Neural Networks achieved an overall accuracy rate of 92%, which proves the performance of the proposed approach.
* 7 pages, 3 figures, 2 tables
CHAINGE: A Blockchain Solution to Automate Payment Detail Updates to Subscription Services
Aug 28, 2021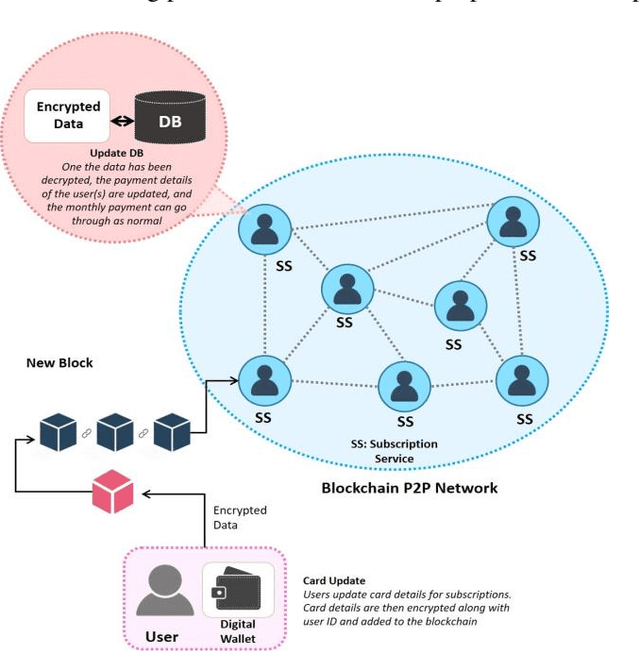
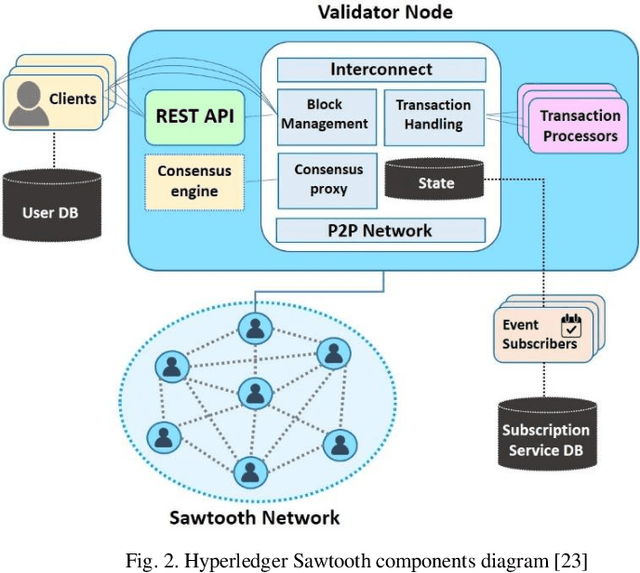
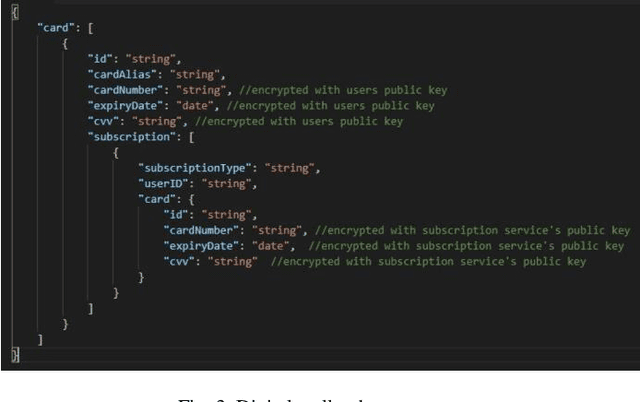
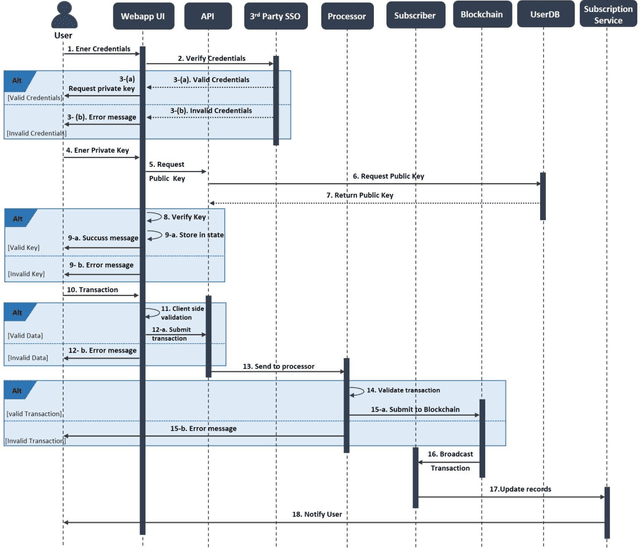
Abstract:The rise of the subscription-based business model has led to a corresponding increase in the number of subscriptions where a customer needs to manage their payments. This management of payments for multiple subscriptions has become a very complicated and insecure task for customers, especially when it comes to renewing payment details when the card is lost, stolen, or expires. In addition, this, mostly manual, process is vulnerable to human error, digital frauds, and data breaches, according to security reports. Thus, in this paper, we propose a novel approach to automate, manage and simplify the Financial Supply Chain involved in the process of updating and managing payments to user subscriptions. This is done by utilising the Hyperledger Sawtooth blockchain framework, that allows a consumer to enter their payment card details in a central digital wallet and link their subscriptions to their cards. The card being updated triggers an event on the blockchain, which allow for the payment details to be updated on subscription systems automatically. The verification tests performed on the prototype of the proposed system shows that its current implementation has been securely achieved.
* 7 pages, 4 figures, 1 table
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge