Alfred Bruckstein
Guidance of Agents in Cyclic Pursuit
Jul 02, 2020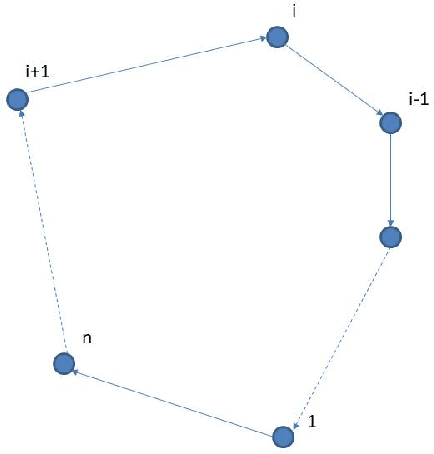
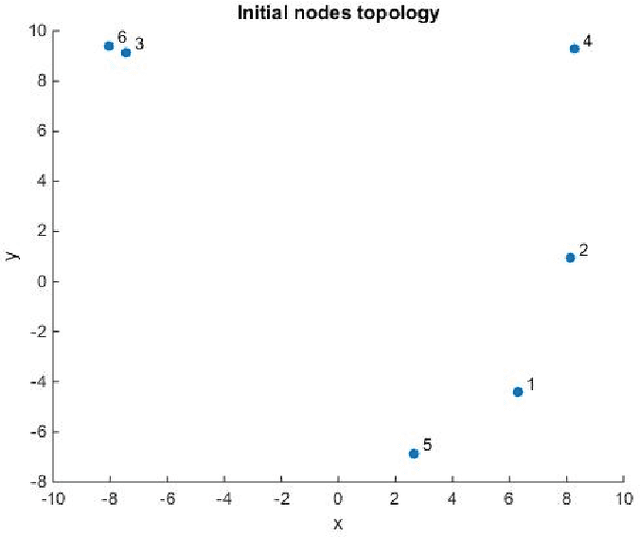
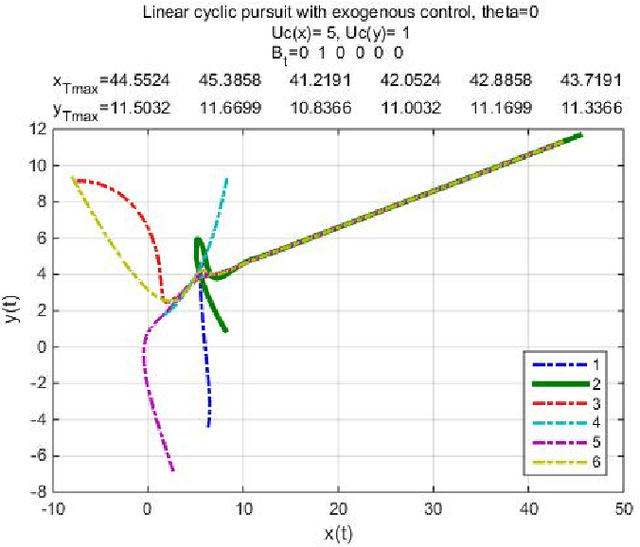
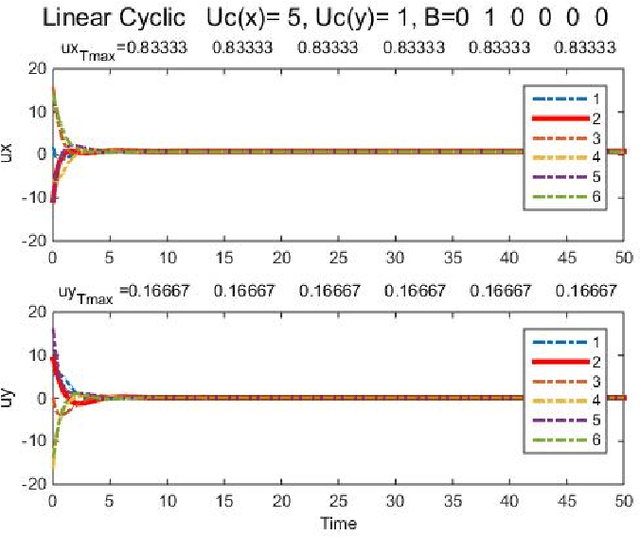
Abstract:This report studies the emergent behavior of systems of agents performing cyclic pursuit controlled by an external broadcast signal detected by a random set of the agents. Two types of cyclic pursuit are analyzed: 1)linear cyclic pursuit, where each agent senses the relative position of its target or leading agent 2)non-linear cyclic pursuit, where the agents can sense only bearing to their leading agent and colliding agents merge and continue on the path of the pursued agent (a so-called "bugs" model). Cyclic pursuit is, in both cases, a gathering algorithm, which has been previously analyzed. The novelty of our work is the derivation of emergent behaviours, in both linear and non-linear cyclic pursuit, in the presence of an exogenous broadcast control detected by a random subset of agents. We show that the emergent behavior of the swarm depends on the type of cyclic pursuit. In the linear case, the agents asymptotically align in the desired direction and move with a common speed which is a proportional to the ratio of the number of agents detecting the broadcast control to the total number of agents in the swarm, for any magnitude of input (velocity) signal. In the non-linear case, the agents gather and move with a shared velocity, which equals the input velocity signal, independently of the number of agents detecting the broadcast signal.
Optimal Dynamic Coverage Infrastructure for Large-Scale Fleets of Reconnaissance UAVs
Nov 17, 2016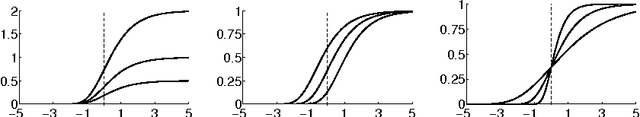
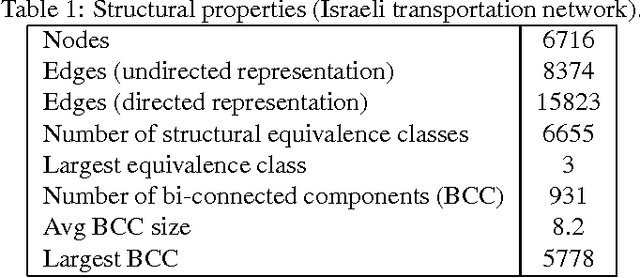
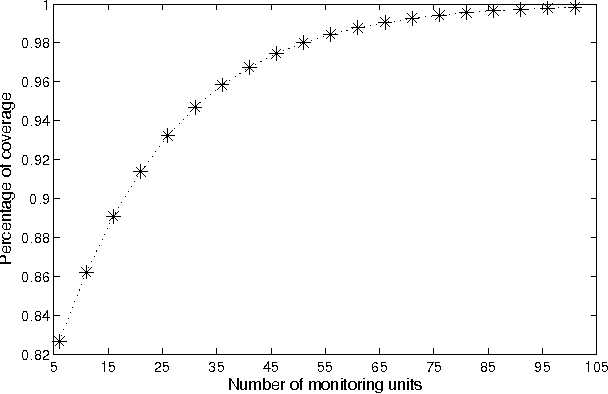
Abstract:Current state of the art in the field of UAV activation relies solely on human operators for the design and adaptation of the drones' flying routes. Furthermore, this is being done today on an individual level (one vehicle per operators), with some exceptions of a handful of new systems, that are comprised of a small number of self-organizing swarms, manually guided by a human operator. Drones-based monitoring is of great importance in variety of civilian domains, such as road safety, homeland security, and even environmental control. In its military aspect, efficiently detecting evading targets by a fleet of unmanned drones has an ever increasing impact on the ability of modern armies to engage in warfare. The latter is true both traditional symmetric conflicts among armies as well as asymmetric ones. Be it a speeding driver, a polluting trailer or a covert convoy, the basic challenge remains the same -- how can its detection probability be maximized using as little number of drones as possible. In this work we propose a novel approach for the optimization of large scale swarms of reconnaissance drones -- capable of producing on-demand optimal coverage strategies for any given search scenario. Given an estimation cost of the threat's potential damages, as well as types of monitoring drones available and their comparative performance, our proposed method generates an analytically provable strategy, stating the optimal number and types of drones to be deployed, in order to cost-efficiently monitor a pre-defined region for targets maneuvering using a given roads networks. We demonstrate our model using a unique dataset of the Israeli transportation network, on which different deployment schemes for drones deployment are evaluated.
Stochastic Broadcast Control of Multi-Agent Swarms
Jul 17, 2016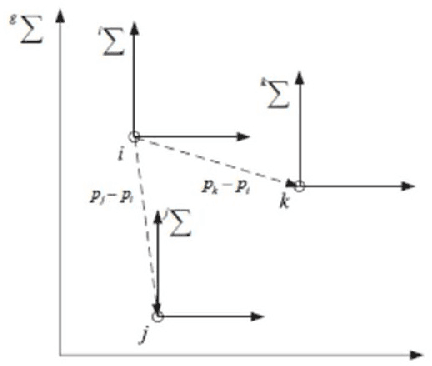
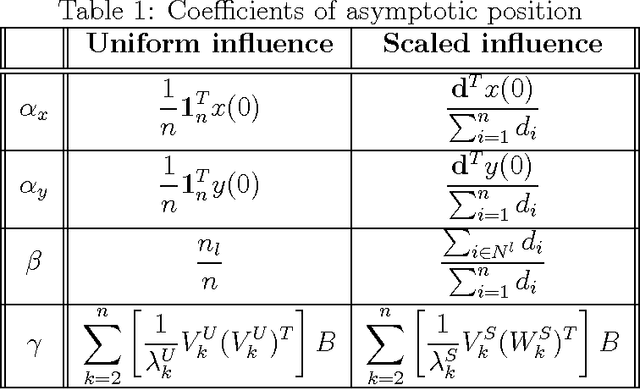
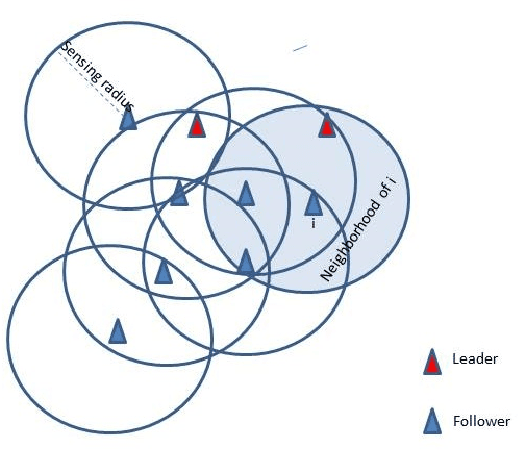
Abstract:We present a model for controlling swarms of mobile agents via broadcast control, assumed to be detected by a random set of agents in the swarm. The agents that detect the control signal become ad-hoc leaders of the swarm. The agents are assumed to be velocity controlled, identical, anonymous, memory-less units with limited capabilities of sensing their neighborhood. Each agent is programmed to behave according to a linear local gathering process, based on the relative position of all its neighbors. The detected exogenous control, which is a desired velocity vector, is added by the leaders to the local gathering control. The graph induced by the agents adjacency is referred to as the visibility graph. We show that for piece-wise constant system parameters and a connected visibility graph, the swarm asymptotically aligns in each time-interval on a line in the direction of the exogenous control signal, and all the agents move with identical speed. These results hold for two models of pairwise influence in the gathering process, uniform and scaled. The impact of the influence model is mostly evident when the visibility graph is incomplete. These results are conditioned by the preservation of the connectedness of the visibility graph. In the second part of the report we analyze sufficient conditions for preserving the connectedness of the visibility graph. We show that if the visibility graph is complete then certain bounds on the control signal suffice to preserve the completeness of the graph. However, when the graph is incomplete, general conditions, independent of the leaders topology, could not be found.
On Cyclic and Nearly Cyclic Multiagent Interactions in the Plane
Jul 16, 2009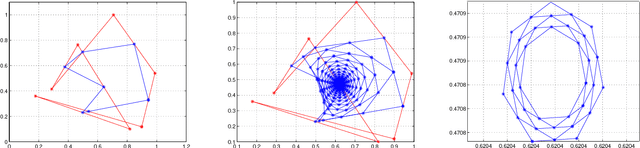
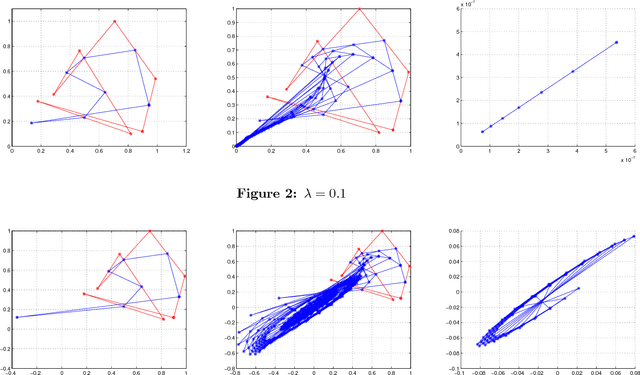
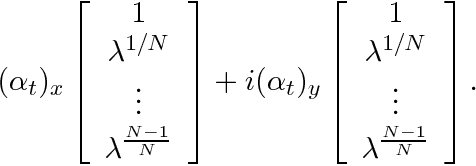
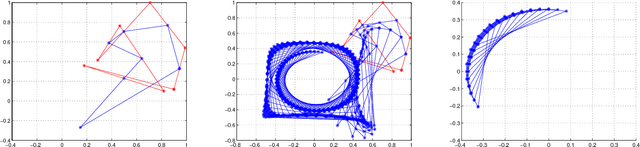
Abstract:We discuss certain types of cyclic and nearly cyclic interactions among N "point"-agents in the plane, leading to formations of interesting limiting geometric configurations. Cyclic pursuit and local averaging interactions have been analyzed in the context of multi-agent gathering. In this paper, we consider some nearly cyclic interactions that break symmetry leading to factor circulants rather than circulant interaction matrices.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge