Access Control of Object Detection Models Using Encrypted Feature Maps
Paper and Code
Feb 01, 2022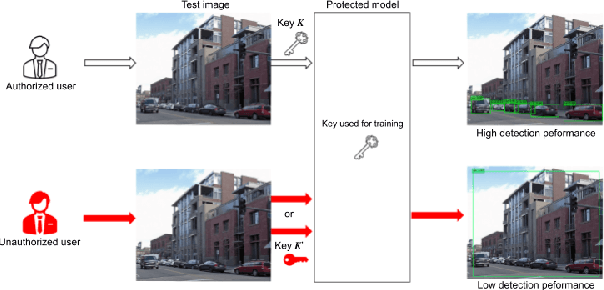
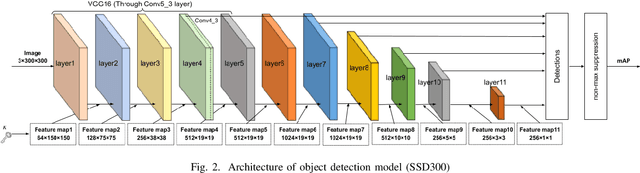
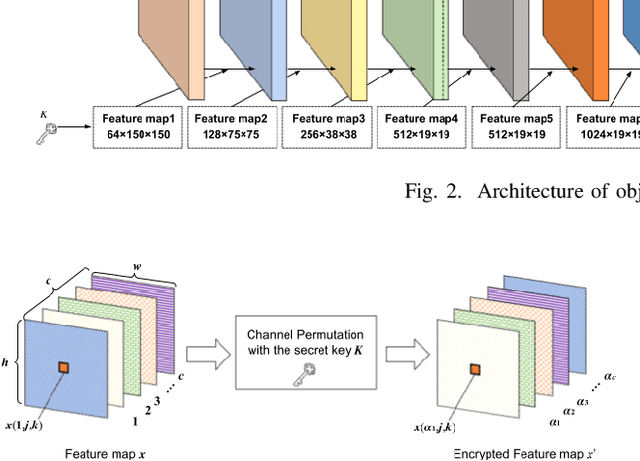

In this paper, we propose an access control method for object detection models. The use of encrypted images or encrypted feature maps has been demonstrated to be effective in access control of models from unauthorized access. However, the effectiveness of the approach has been confirmed in only image classification models and semantic segmentation models, but not in object detection models. In this paper, the use of encrypted feature maps is shown to be effective in access control of object detection models for the first time.
* To appear in 2022 IEEE 4th Global Conference on Life Sciences and
Technologies (LifeTech 2022)
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge