Scott Wallace
Defending Against Adversarial Attacks in Transmission- and Distribution-level PMU Data
Aug 20, 2020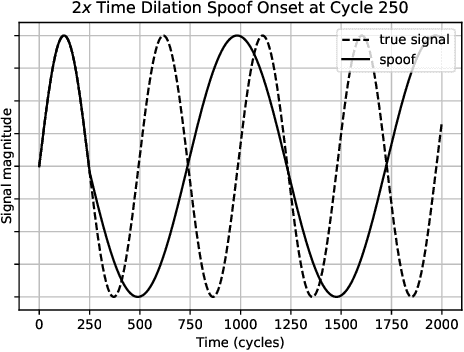
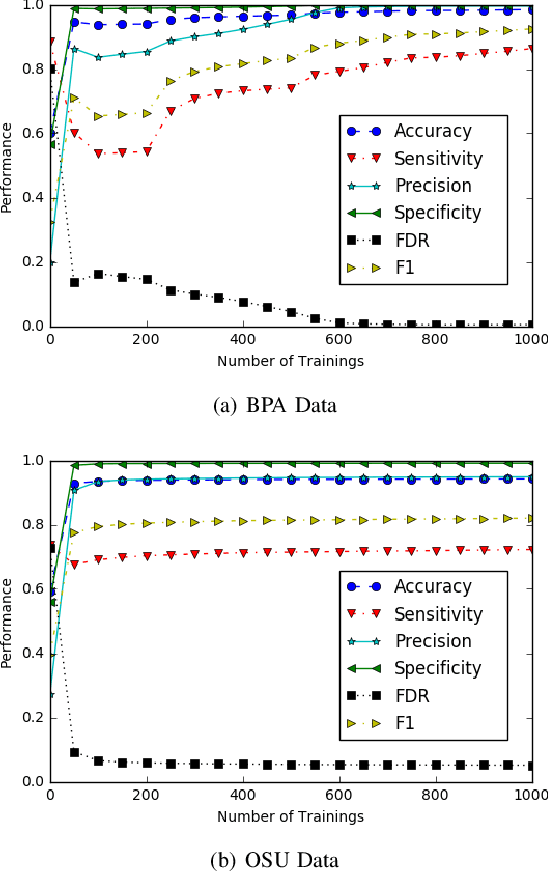
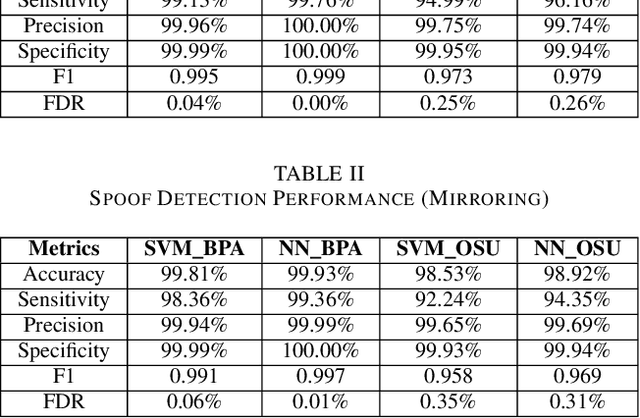
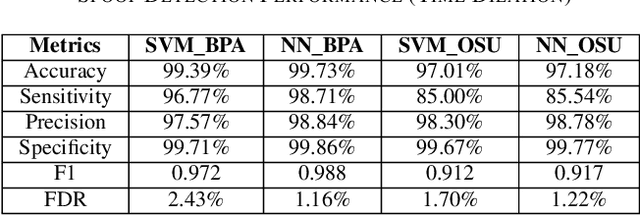
Abstract:Phasor measurement units (PMUs) provide high-fidelity data that improve situation awareness of electric power grid operations. PMU datastreams inform wide-area state estimation, monitor area control error, and facilitate event detection in real time. As PMU data become more available and increasingly reliable, these devices are found in new roles within control systems, such as remedial action schemes and early warning detection systems. As with other cyber physical systems, maintaining data integrity and security pose a significant challenge for power system operators. In this paper, we present a comprehensive analysis of multiple machine learning techniques to detect malicious data injection within PMU data streams. The two datasets used in this study come from two PMU networks: an inter-university, research-grade distribution network spanning three institutions in the U.S. Pacific Northwest, and a utility transmission network from the Bonneville Power Administration. We implement the detection algorithms with TensorFlow, an open-source software library for machine learning, and the results demonstrate potential for distributing the training workload and achieving higher performance, while maintaining effectiveness in the detection of spoofed data.
Fast Sequence Component Analysis for Attack Detection in Synchrophasor Networks
Sep 17, 2015



Abstract:Modern power systems have begun integrating synchrophasor technologies into part of daily operations. Given the amount of solutions offered and the maturity rate of application development it is not a matter of "if" but a matter of "when" in regards to these technologies becoming ubiquitous in control centers around the world. While the benefits are numerous, the functionality of operator-level applications can easily be nullified by injection of deceptive data signals disguised as genuine measurements. Such deceptive action is a common precursor to nefarious, often malicious activity. A correlation coefficient characterization and machine learning methodology are proposed to detect and identify injection of spoofed data signals. The proposed method utilizes statistical relationships intrinsic to power system parameters, which are quantified and presented. Several spoofing schemes have been developed to qualitatively and quantitatively demonstrate detection capabilities.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge