Muhammad Asam
IoT Malware Detection Architecture using a Novel Channel Boosted and Squeezed CNN
Feb 08, 2022



Abstract:Interaction between devices, people, and the Internet has given birth to a new digital communication model, the Internet of Things (IoT). The seamless network of these smart devices is the core of this IoT model. However, on the other hand, integrating smart devices to constitute a network introduces many security challenges. These connected devices have created a security blind spot, where cybercriminals can easily launch an attack to compromise the devices using malware proliferation techniques. Therefore, malware detection is considered a lifeline for the survival of IoT devices against cyberattacks. This study proposes a novel IoT Malware Detection Architecture (iMDA) using squeezing and boosting dilated convolutional neural network (CNN). The proposed architecture exploits the concepts of edge and smoothing, multi-path dilated convolutional operations, channel squeezing, and boosting in CNN. Edge and smoothing operations are employed with split-transform-merge (STM) blocks to extract local structure and minor contrast variation in the malware images. STM blocks performed multi-path dilated convolutional operations, which helped recognize the global structure of malware patterns. Additionally, channel squeezing and merging helped to get the prominent reduced and diverse feature maps, respectively. Channel squeezing and boosting are applied with the help of STM block at the initial, middle and final levels to capture the texture variation along with the depth for the sake of malware pattern hunting. The proposed architecture has shown substantial performance compared with the customized CNN models. The proposed iMDA has achieved Accuracy: 97.93%, F1-Score: 0.9394, Precision: 0.9864, MCC: 0. 8796, Recall: 0.8873, AUC-PR: 0.9689 and AUC-ROC: 0.9938.
Malware Classification Using Deep Boosted Learning
Jul 08, 2021
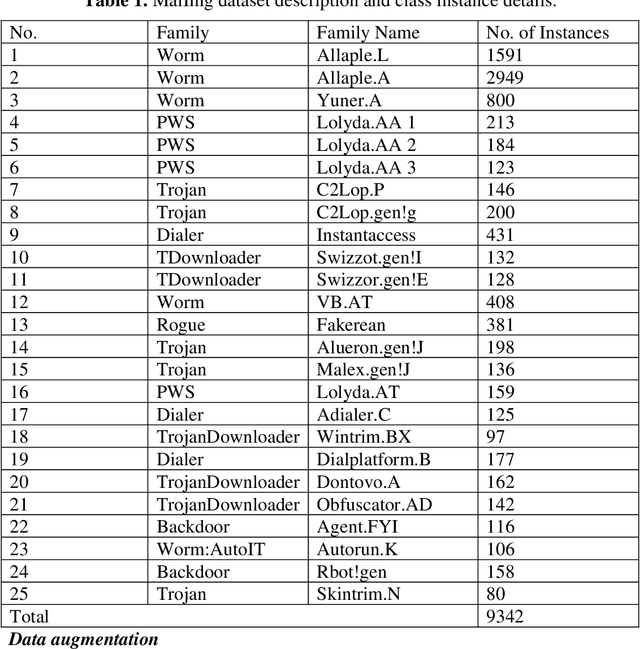
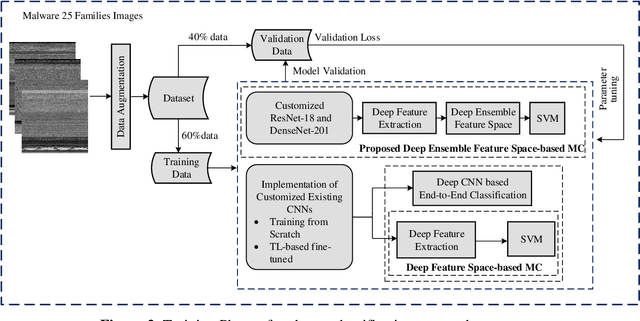
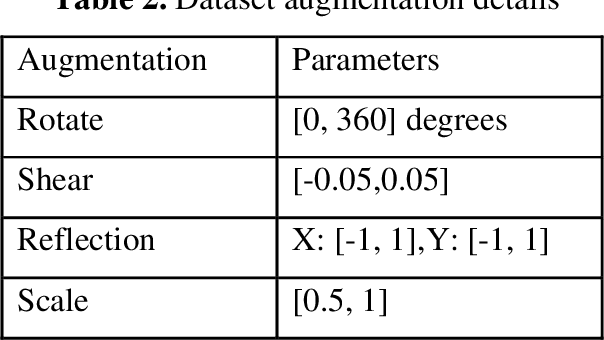
Abstract:Malicious activities in cyberspace have gone further than simply hacking machines and spreading viruses. It has become a challenge for a nations survival and hence has evolved to cyber warfare. Malware is a key component of cyber-crime, and its analysis is the first line of defence against attack. This work proposes a novel deep boosted hybrid learning-based malware classification framework and named as Deep boosted Feature Space-based Malware classification (DFS-MC). In the proposed framework, the discrimination power is enhanced by fusing the feature spaces of the best performing customized CNN architectures models and its discrimination by an SVM for classification. The discrimination capacity of the proposed classification framework is assessed by comparing it against the standard customized CNNs. The customized CNN models are implemented in two ways: softmax classifier and deep hybrid learning-based malware classification. In the hybrid learning, Deep features are extracted from customized CNN architectures and fed into the conventional machine learning classifier to improve the classification performance. We also introduced the concept of transfer learning in a customized CNN architecture based malware classification framework through fine-tuning. The performance of the proposed malware classification approaches are validated on the MalImg malware dataset using the hold-out cross-validation technique. Experimental comparisons were conducted by employing innovative, customized CNN, trained from scratch and fine-tuning the customized CNN using transfer learning. The proposed classification framework DFS-MC showed improved results, Accuracy: 98.61%, F-score: 0.96, Precision: 0.96, and Recall: 0.96.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge