Manish Agrawal
FGM optimization in complex domains using Gaussian process regression based profile generation algorithm
Nov 15, 2025Abstract:This manuscript addresses the challenge of designing functionally graded materials (FGMs) for arbitrary-shaped domains. Towards this goal, the present work proposes a generic volume fraction profile generation algorithm based on Gaussian Process Regression (GPR). The proposed algorithm can handle complex-shaped domains and generate smooth FGM profiles while adhering to the specified volume fraction values at boundaries/part of boundaries. The resulting design space from GPR comprises diverse profiles, enhancing the potential for discovering optimal configurations. Further, the algorithm allows the user to control the smoothness of the underlying profiles and the size of the design space through a length scale parameter. Further, the proposed profile generation scheme is coupled with the genetic algorithm to find the optimum FGM profiles for a given application. To make the genetic algorithm consistent with the GPR profile generation scheme, the standard simulated binary crossover operator in the genetic algorithm has been modified with a projection operator. We present numerous thermoelastic optimization examples to demonstrate the efficacy of the proposed profile generation algorithm and optimization framework.
Unsupervised Threat Hunting using Continuous Bag-of-Terms-and-Time (CBoTT)
Mar 15, 2024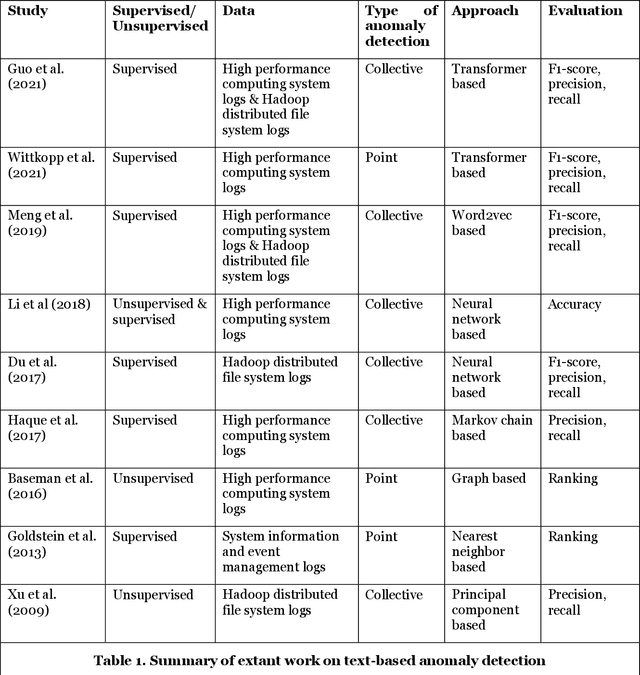
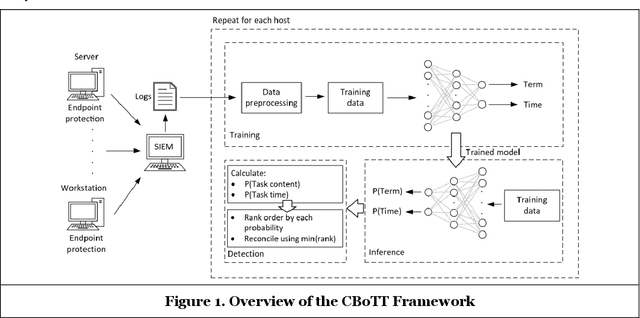
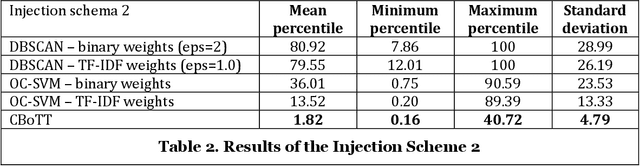
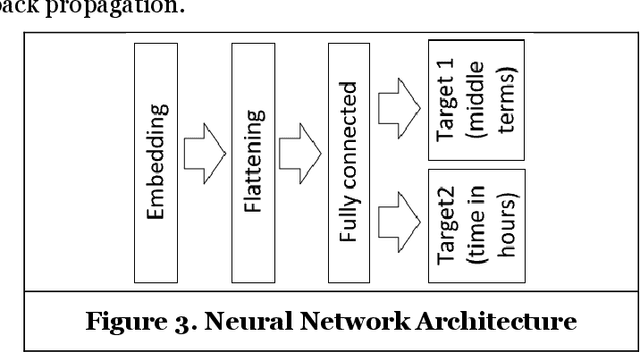
Abstract:Threat hunting is sifting through system logs to detect malicious activities that might have bypassed existing security measures. It can be performed in several ways, one of which is based on detecting anomalies. We propose an unsupervised framework, called continuous bag-of-terms-and-time (CBoTT), and publish its application programming interface (API) to help researchers and cybersecurity analysts perform anomaly-based threat hunting among SIEM logs geared toward process auditing on endpoint devices. Analyses show that our framework consistently outperforms benchmark approaches. When logs are sorted by likelihood of being an anomaly (from most likely to least), our approach identifies anomalies at higher percentiles (between 1.82-6.46) while benchmark approaches identify the same anomalies at lower percentiles (between 3.25-80.92). This framework can be used by other researchers to conduct benchmark analyses and cybersecurity analysts to find anomalies in SIEM logs.
A novel data generation scheme for surrogate modelling with deep operator networks
Feb 24, 2024



Abstract:Operator-based neural network architectures such as DeepONets have emerged as a promising tool for the surrogate modeling of physical systems. In general, towards operator surrogate modeling, the training data is generated by solving the PDEs using techniques such as Finite Element Method (FEM). The computationally intensive nature of data generation is one of the biggest bottleneck in deploying these surrogate models for practical applications. In this study, we propose a novel methodology to alleviate the computational burden associated with training data generation for DeepONets. Unlike existing literature, the proposed framework for data generation does not use any partial differential equation integration strategy, thereby significantly reducing the computational cost associated with generating training dataset for DeepONet. In the proposed strategy, first, the output field is generated randomly, satisfying the boundary conditions using Gaussian Process Regression (GPR). From the output field, the input source field can be calculated easily using finite difference techniques. The proposed methodology can be extended to other operator learning methods, making the approach widely applicable. To validate the proposed approach, we employ the heat equations as the model problem and develop the surrogate model for numerous boundary value problems.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge