Lorenzo Marconi
CQE under Epistemic Dependencies: Algorithms and Experiments (extended version)
Jul 23, 2025Abstract:We investigate Controlled Query Evaluation (CQE) over ontologies, where information disclosure is regulated by epistemic dependencies (EDs), a family of logical rules recently proposed for the CQE framework. In particular, we combine EDs with the notion of optimal GA censors, i.e. maximal sets of ground atoms that are entailed by the ontology and can be safely revealed. We focus on answering Boolean unions of conjunctive queries (BUCQs) with respect to the intersection of all optimal GA censors - an approach that has been shown in other contexts to ensure strong security guarantees with favorable computational behavior. First, we characterize the security of this intersection-based approach and identify a class of EDs (namely, full EDs) for which it remains safe. Then, for a subclass of EDs and for DL-Lite_R ontologies, we show that answering BUCQs in the above CQE semantics is in AC^0 in data complexity by presenting a suitable, detailed first-order rewriting algorithm. Finally, we report on experiments conducted in two different evaluation scenarios, showing the practical feasibility of our rewriting function.
Controlled Query Evaluation through Epistemic Dependencies
May 03, 2024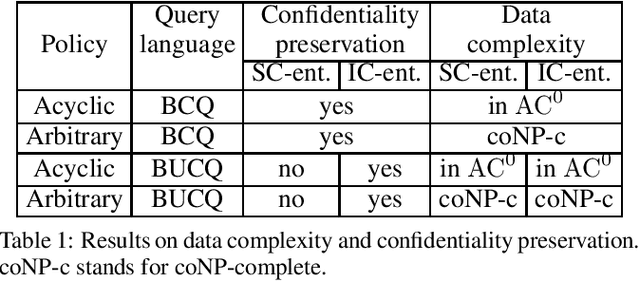
Abstract:In this paper, we propose the use of epistemic dependencies to express data protection policies in Controlled Query Evaluation (CQE), which is a form of confidentiality-preserving query answering over ontologies and databases. The resulting policy language goes significantly beyond those proposed in the literature on CQE so far, allowing for very rich and practically interesting forms of data protection rules. We show the expressive abilities of our framework and study the data complexity of CQE for (unions of) conjunctive queries when ontologies are specified in the Description Logic DL-Lite_R. Interestingly, while we show that the problem is in general intractable, we prove tractability for the case of acyclic epistemic dependencies by providing a suitable query rewriting algorithm. The latter result paves the way towards the implementation and practical application of this new approach to CQE.
Consistent Query Answering for Existential Rules under Tuple-Deletion Semantics
Jan 11, 2024Abstract:We study consistent query answering over knowledge bases expressed by existential rules. Specifically, we establish the data complexity of consistent query answering and repair checking under tuple-deletion semantics for a general class of disjunctive existential rules and for several subclasses thereof (acyclic, linear, full, guarded, and sticky). In particular, we identify several cases in which the above problems are tractable or even first-order rewritable, and present new query rewriting techniques that can be the basis for practical inconsistency-tolerant query answering systems.
CQE in OWL 2 QL: A "Longest Honeymoon" Approach
Jul 22, 2022Abstract:Controlled Query Evaluation (CQE) has been recently studied in the context of Semantic Web ontologies. The goal of CQE is concealing some query answers so as to prevent external users from inferring confidential information. In general, there exist multiple, mutually incomparable ways of concealing answers, and previous CQE approaches choose in advance which answers are visible and which are not. In this paper, instead, we study a dynamic CQE method, namely, we propose to alter the answer to the current query based on the evaluation of previous ones. We aim at a system that, besides being able to protect confidential data, is maximally cooperative, which intuitively means that it answers affirmatively to as many queries as possible; it achieves this goal by delaying answer modifications as much as possible. We also show that the behavior we get cannot be intensionally simulated through a static approach, independent of query history. Interestingly, for OWL 2 QL ontologies and policy expressed through denials, query evaluation under our semantics is first-order rewritable, and thus in AC0 in data complexity. This paves the way for the development of practical algorithms, which we also preliminarily discuss in the paper.
Direct Bézier-Based Trajectory Planner for Improved Local Exploration of Unknown Environments
Mar 02, 2022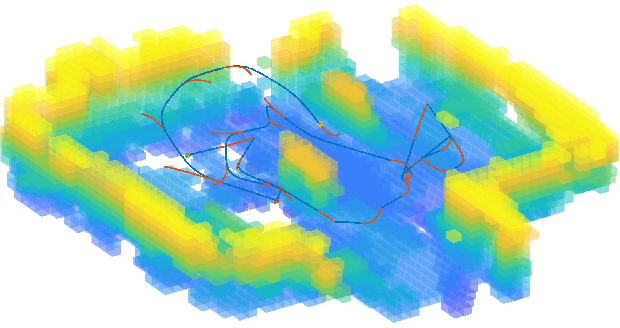
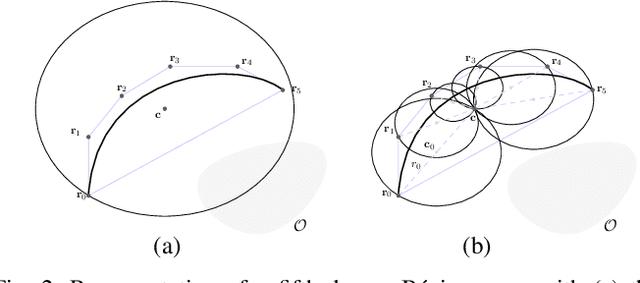
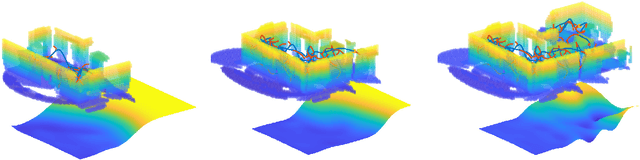
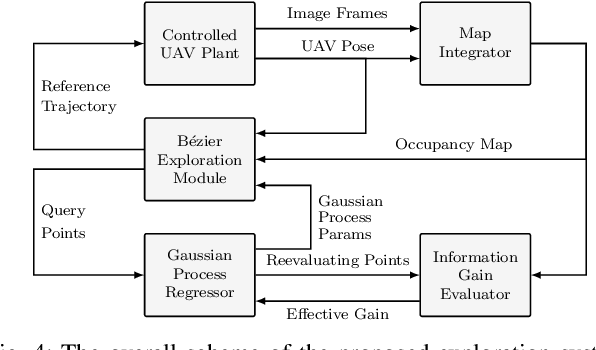
Abstract:Autonomous exploration is an essential capability for mobile robots, as the majority of their applications require the ability to efficiently collect information about their surroundings. In the literature, there are several approaches, ranging from frontier-based methods to hybrid solutions involving the ability to plan both local and global exploring paths, but only few of them focus on improving local exploration by properly tuning the planned trajectory, often leading to "stop-and-go" like behaviors. In this work we propose a novel RRT-inspired B\'ezier-based next-best-view trajectory planner able to deal with the problem of fast local exploration. Gaussian process inference is used to guarantee fast exploration gain retrieval while still being consistent with the exploration task. The proposed approach is compared with other available state-of-the-art algorithms and tested in a real-world scenario. The implemented code is publicly released as open-source code to encourage further developments and benchmarking.
UAV-Based Search and Rescue in Avalanches using ARVA: An Extremum Seeking Approach
Jun 28, 2021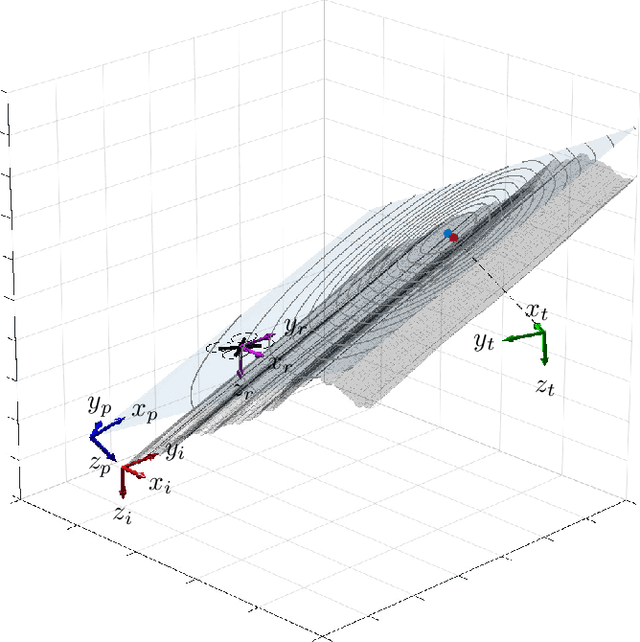
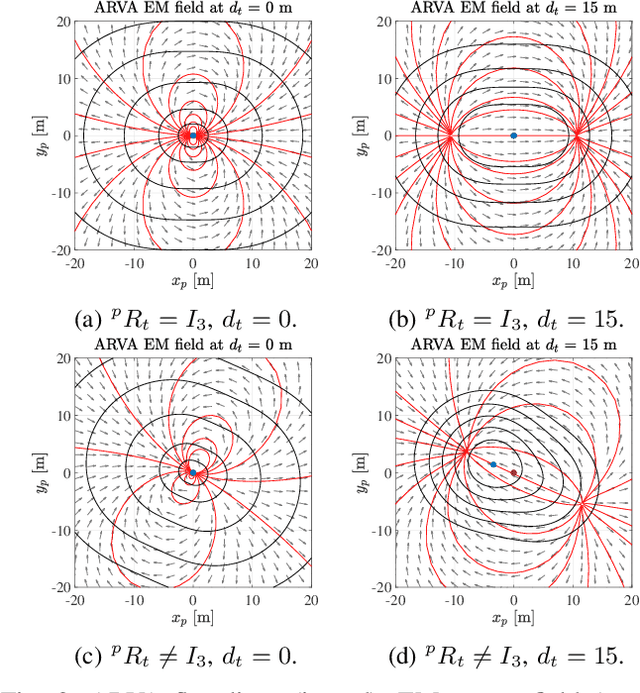
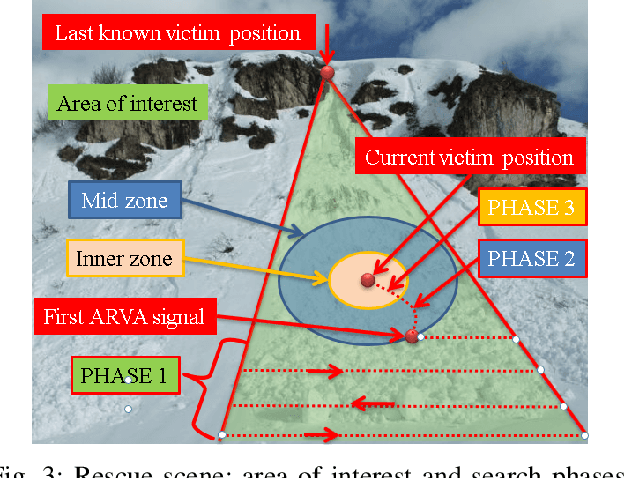
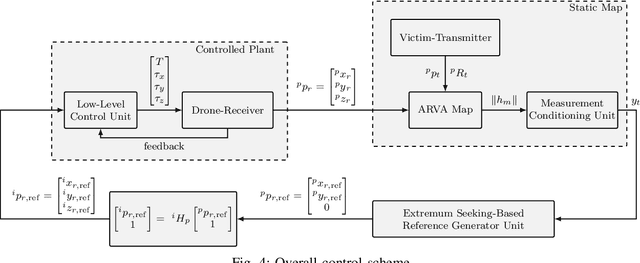
Abstract:This work deals with the problem of localizing a victim buried by an avalanche by means of a drone equipped with an ARVA (Appareil de Recherche de Victimes d'Avalanche) sensor. The proposed control solution is based on a "model-free" extremum seeking strategy which is shown to succeed in steering the drone in a neighborhood of the victim position. The effectiveness and robustness of the proposed algorithm is tested in Gazebo simulation environment, where a new flight mode and a new controller module have been implemented as an extension of the well-known PX4 open source flight stack. Finally, to test usability, we present hardware-in-the-loop simulations on a Pixhawk 2 Cube board.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge