Katherine Davis
Bayesian Reinforcement Learning for Automatic Voltage Control under Cyber-Induced Uncertainty
May 25, 2023Abstract:Voltage control is crucial to large-scale power system reliable operation, as timely reactive power support can help prevent widespread outages. However, there is currently no built in mechanism for power systems to ensure that the voltage control objective to maintain reliable operation will survive or sustain the uncertainty caused under adversary presence. Hence, this work introduces a Bayesian Reinforcement Learning (BRL) approach for power system control problems, with focus on sustained voltage control under uncertainty in a cyber-adversarial environment. This work proposes a data-driven BRL-based approach for automatic voltage control by formulating and solving a Partially-Observable Markov Decision Problem (POMDP), where the states are partially observable due to cyber intrusions. The techniques are evaluated on the WSCC and IEEE 14 bus systems. Additionally, BRL techniques assist in automatically finding a threshold for exploration and exploitation in various RL techniques.
Infinite Impulse Response Graph Neural Networks for Cyberattack Localization in Smart Grids
Jun 25, 2022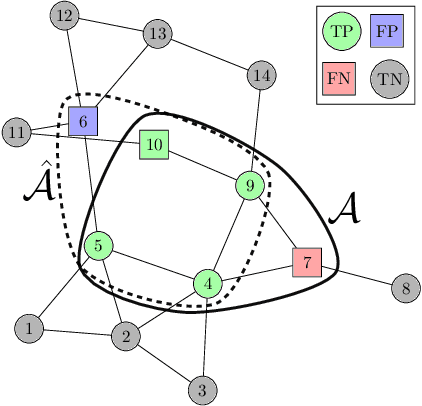
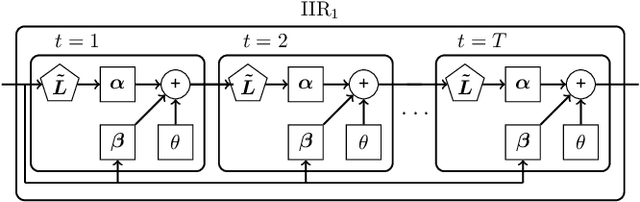
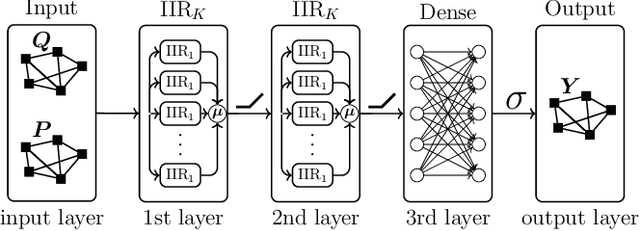
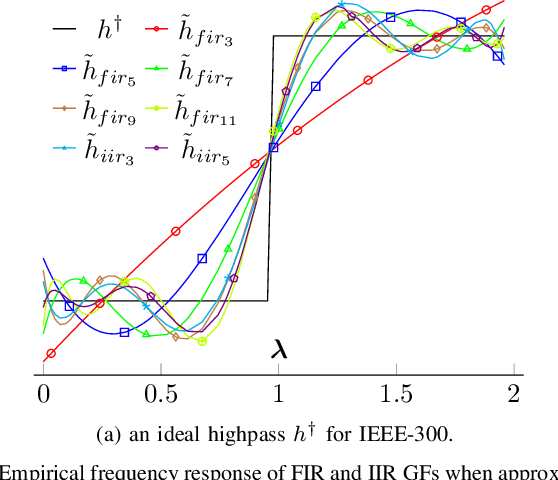
Abstract:This study employs Infinite Impulse Response (IIR) Graph Neural Networks (GNN) to efficiently model the inherent graph network structure of the smart grid data to address the cyberattack localization problem. First, we numerically analyze the empirical frequency response of the Finite Impulse Response (FIR) and IIR graph filters (GFs) to approximate an ideal spectral response. We show that, for the same filter order, IIR GFs provide a better approximation to the desired spectral response and they also present the same level of approximation to a lower order GF due to their rational type filter response. Second, we propose an IIR GNN model to efficiently predict the presence of cyberattacks at the bus level. Finally, we evaluate the model under various cyberattacks at both sample-wise (SW) and bus-wise (BW) level, and compare the results with the existing architectures. It is experimentally verified that the proposed model outperforms the state-of-the-art FIR GNN model by 9.2% and 14% in terms of SW and BW localization, respectively.
Spatio-Temporal Failure Propagation in Cyber-Physical Power Systems
Feb 05, 2022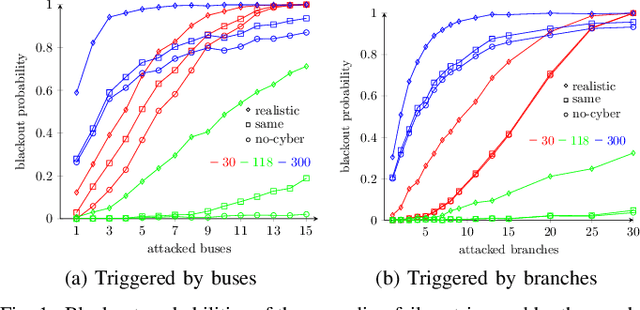
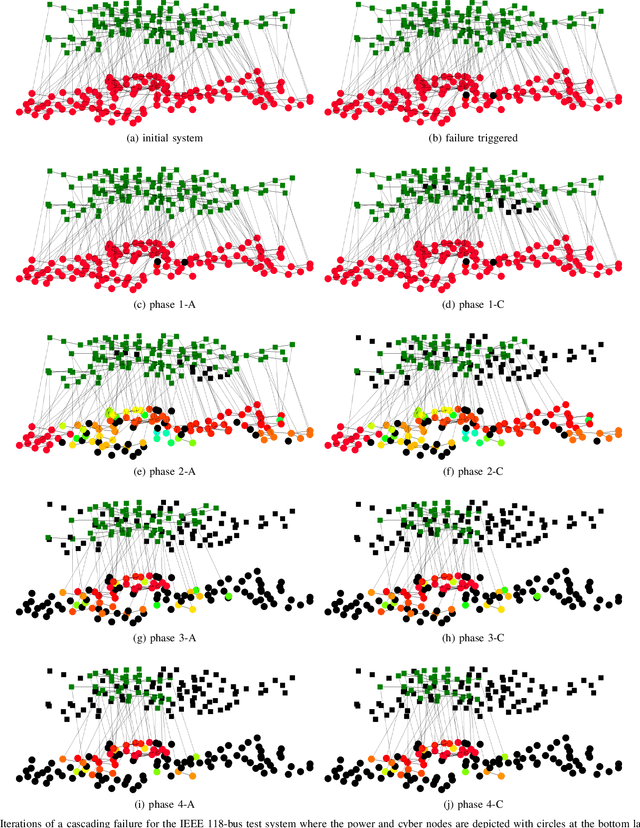
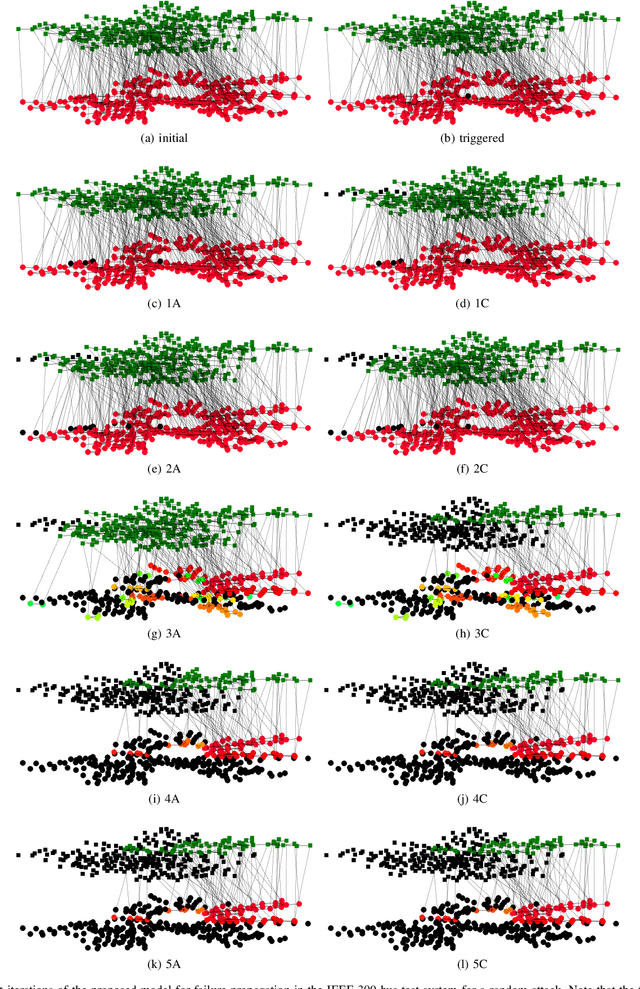
Abstract:Cascading failure in power systems is triggered by a small perturbation that leads to a sequence of failures spread through the system. The interconnection between different components in a power system causes failures to easily propagate across the system. The situation gets worse by considering the interconnection between cyber and physical layers in power systems. A plethora of work has studied the cascading failure in power systems to calculate its impact on the system. Understanding how failures propagate into the system in time and space can help the system operator to take preventive actions and upgrade the system accordingly. Due to the nonlinearity of the power flow equation as well as the engineering constraints in the power system, it is essential to understand the spatio-temporal failure propagation in cyber-physical power systems (CPPS). This paper proposes an asynchronous algorithm for investigating failure propagation in CPPS. The physics of the power system is addressed by the full AC power flow equations. Various practical constraints including load shedding, load-generation balance, and island operation are considered to address practical constraints in power system operation. The propagation of various random initial attacks of different sizes is analyzed and visualized to elaborate on the applicability of the proposed approach. Our findings shed light on the cascading failure evolution in CPPS.
Cyberattack Detection in Large-Scale Smart Grids using Chebyshev Graph Convolutional Networks
Dec 25, 2021


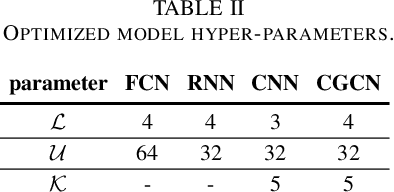
Abstract:As a highly complex and integrated cyber-physical system, modern power grids are exposed to cyberattacks. False data injection attacks (FDIAs), specifically, represent a major class of cyber threats to smart grids by targeting the measurement data's integrity. Although various solutions have been proposed to detect those cyberattacks, the vast majority of the works have ignored the inherent graph structure of the power grid measurements and validated their detectors only for small test systems with less than a few hundred buses. To better exploit the spatial correlations of smart grid measurements, this paper proposes a deep learning model for cyberattack detection in large-scale AC power grids using Chebyshev Graph Convolutional Networks (CGCN). By reducing the complexity of spectral graph filters and making them localized, CGCN provides a fast and efficient convolution operation to model the graph structural smart grid data. We numerically verify that the proposed CGCN based detector surpasses the state-of-the-art model by 7.86 in detection rate and 9.67 in false alarm rate for a large-scale power grid with 2848 buses. It is notable that the proposed approach detects cyberattacks under 4 milliseconds for a 2848-bus system, which makes it a good candidate for real-time detection of cyberattacks in large systems.
Inter-Domain Fusion for Enhanced Intrusion Detection in Power Systems: An Evidence Theoretic and Meta-Heuristic Approach
Nov 20, 2021



Abstract:False alerts due to misconfigured/ compromised IDS in ICS networks can lead to severe economic and operational damage. To solve this problem, research has focused on leveraging deep learning techniques that help reduce false alerts. However, a shortcoming is that these works often require or implicitly assume the physical and cyber sensors to be trustworthy. Implicit trust of data is a major problem with using artificial intelligence or machine learning for CPS security, because during critical attack detection time they are more at risk, with greater likelihood and impact, of also being compromised. To address this shortcoming, the problem is reframed on how to make good decisions given uncertainty. Then, the decision is detection, and the uncertainty includes whether the data used for ML-based IDS is compromised. Thus, this work presents an approach for reducing false alerts in CPS power systems by dealing uncertainty without the knowledge of prior distribution of alerts. Specifically, an evidence theoretic based approach leveraging Dempster Shafer combination rules are proposed for reducing false alerts. A multi-hypothesis mass function model is designed that leverages probability scores obtained from various supervised-learning classifiers. Using this model, a location-cum-domain based fusion framework is proposed and evaluated with different combination rules, that fuse multiple evidence from inter-domain and intra-domain sensors. The approach is demonstrated in a cyber-physical power system testbed with Man-In-The-Middle attack emulation in a large-scale synthetic electric grid. For evaluating the performance, plausibility, belief, pignistic, etc. metrics as decision functions are considered. To improve the performance, a multi-objective based genetic algorithm is proposed for feature selection considering the decision metrics as the fitness function.
Joint Detection and Localization of Stealth False Data Injection Attacks in Smart Grids using Graph Neural Networks
Apr 24, 2021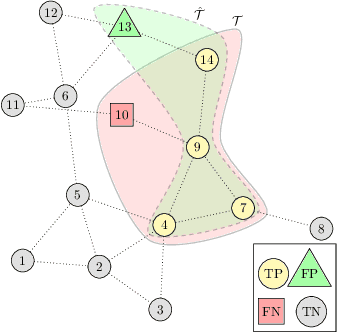
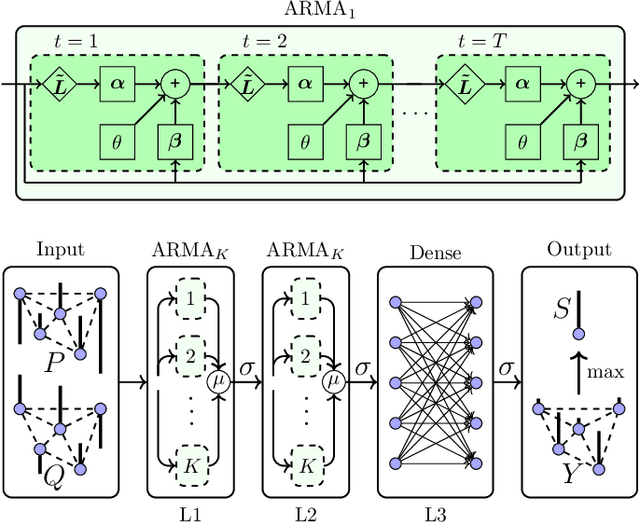
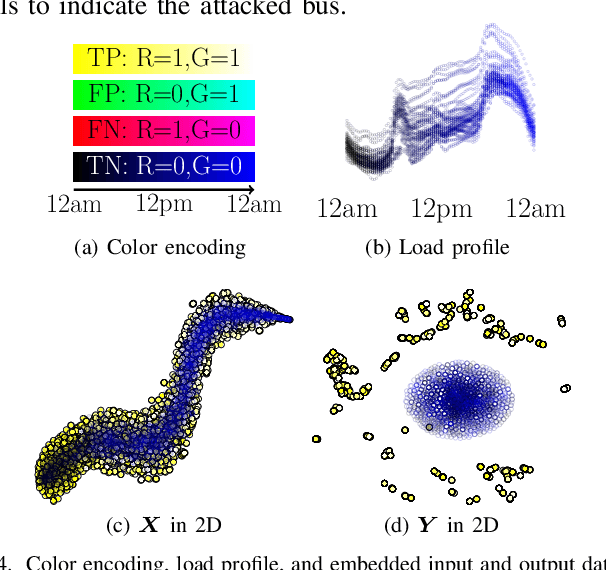
Abstract:False data injection attacks (FDIA) are becoming an active avenue of research as such attacks are more frequently encountered in power systems. Contrary to the detection of these attacks, less attention has been paid to identifying the attacked units of the grid. To this end, this work jointly studies detecting and localizing the stealth FDIA in modern power grids. Exploiting the inherent graph topology of power systems as well as the spatial correlations of smart meters' data, this paper proposes an approach based on the graph neural network (GNN) to identify the presence and location of the FDIA. The proposed approach leverages the auto-regressive moving average (ARMA) type graph convolutional filters which offer better noise robustness and frequency response flexibility compared to the polynomial type graph convolutional filters such as Chebyshev. To the best of our knowledge, this is the first work based on GNN that automatically detects and localizes FDIA in power systems. Extensive simulations and visualizations show that the proposed approach outperforms the available methods in both detection and localization FDIA for different IEEE test systems. Thus, the targeted areas in power grids can be identified and preventive actions can be taken before the attack impacts the grid.
Graph Neural Networks Based Detection of Stealth False Data Injection Attacks in Smart Grids
Apr 05, 2021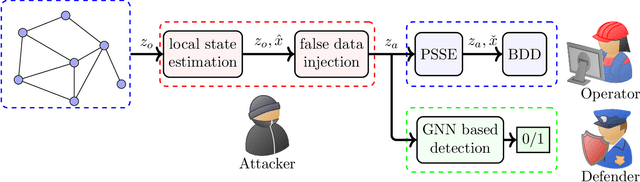
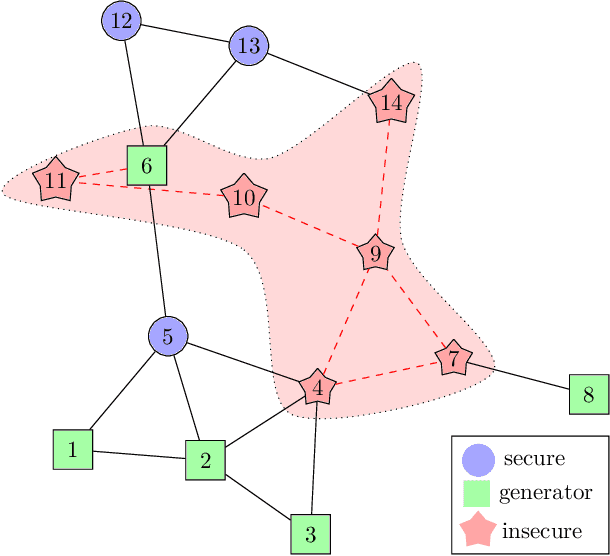
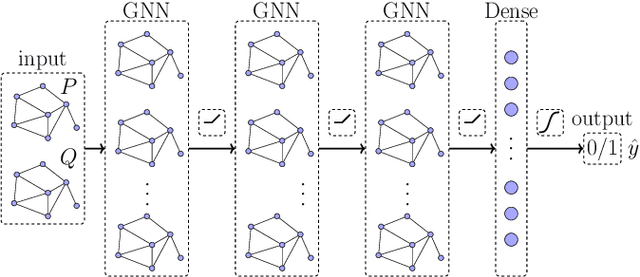
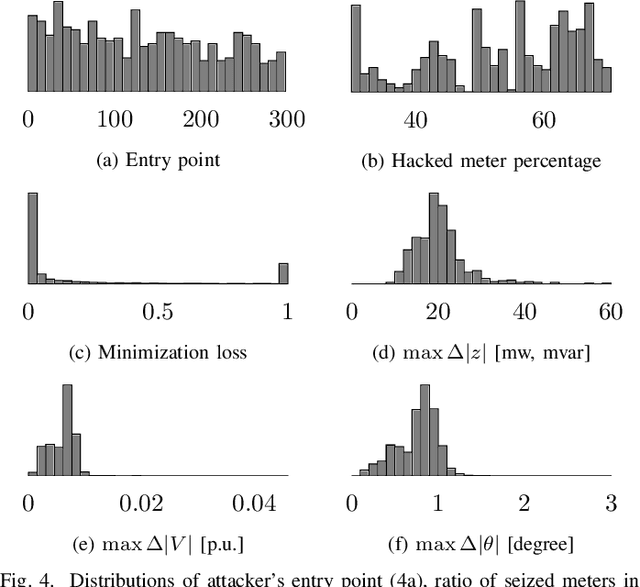
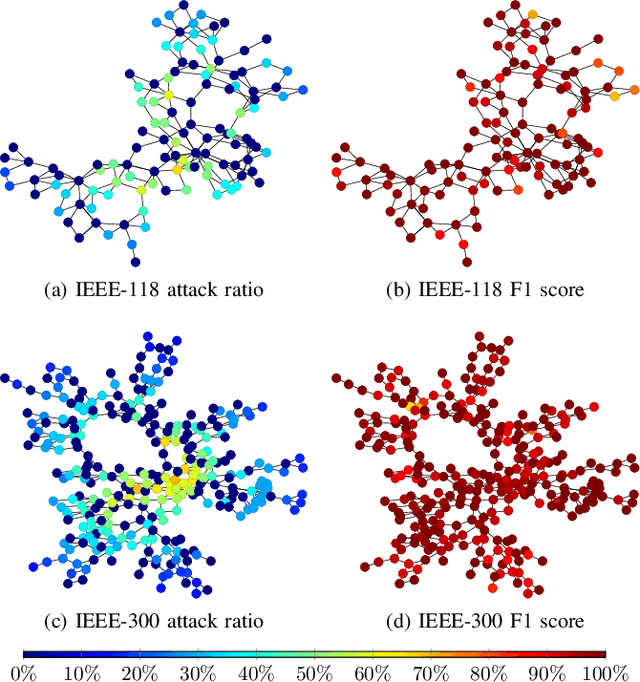
Abstract:False data injection attacks (FDIAs) represent a major class of attacks that aim to break the integrity of measurements by injecting false data into the smart metering devices in power grid. To the best of authors' knowledge, no study has attempted to design a detector that automatically models the underlying graph topology and spatially correlated measurement data of the smart grids to better detect cyber attacks. The contributions of this paper to detect and mitigate FDIAs are twofold. First, we present a generic, localized, and stealth (unobservable) attack generation methodology and a publicly accessible dataset for researchers to develop and test their algorithms. Second, we propose a Graph Neural Network (GNN) based, scalable and real-time detector of FDIAs that efficiently combines model-driven and data-driven approaches by incorporating the inherent physical connections of modern AC power grids and exploiting the spatial correlations of the measurement data. It is experimentally verified by comparing the proposed GNN based detector with the currently available FDIA detectors in literature that our algorithm outperforms the best available solutions by 6.21\%, 0.69\%, and 2.73\% in detection rate and by 3.65\%, 0.34\% and 1.38\% in F1 score for standard IEEE testbeds with 14, 118, and 300 buses, respectively.
Multi-Source Data Fusion for Cyberattack Detection in Power Systems
Jan 18, 2021



Abstract:Cyberattacks can cause a severe impact on power systems unless detected early. However, accurate and timely detection in critical infrastructure systems presents challenges, e.g., due to zero-day vulnerability exploitations and the cyber-physical nature of the system coupled with the need for high reliability and resilience of the physical system. Conventional rule-based and anomaly-based intrusion detection system (IDS) tools are insufficient for detecting zero-day cyber intrusions in the industrial control system (ICS) networks. Hence, in this work, we show that fusing information from multiple data sources can help identify cyber-induced incidents and reduce false positives. Specifically, we present how to recognize and address the barriers that can prevent the accurate use of multiple data sources for fusion-based detection. We perform multi-source data fusion for training IDS in a cyber-physical power system testbed where we collect cyber and physical side data from multiple sensors emulating real-world data sources that would be found in a utility and synthesizes these into features for algorithms to detect intrusions. Results are presented using the proposed data fusion application to infer False Data and Command injection-based Man-in- The-Middle (MiTM) attacks. Post collection, the data fusion application uses time-synchronized merge and extracts features followed by pre-processing such as imputation and encoding before training supervised, semi-supervised, and unsupervised learning models to evaluate the performance of the IDS. A major finding is the improvement of detection accuracy by fusion of features from cyber, security, and physical domains. Additionally, we observed the co-training technique performs at par with supervised learning methods when fed with our features.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge