Félix Gómez Mármol
A Big Data Architecture for Early Identification and Categorization of Dark Web Sites
Jan 24, 2024Abstract:The dark web has become notorious for its association with illicit activities and there is a growing need for systems to automate the monitoring of this space. This paper proposes an end-to-end scalable architecture for the early identification of new Tor sites and the daily analysis of their content. The solution is built using an Open Source Big Data stack for data serving with Kubernetes, Kafka, Kubeflow, and MinIO, continuously discovering onion addresses in different sources (threat intelligence, code repositories, web-Tor gateways, and Tor repositories), downloading the HTML from Tor and deduplicating the content using MinHash LSH, and categorizing with the BERTopic modeling (SBERT embedding, UMAP dimensionality reduction, HDBSCAN document clustering and c-TF-IDF topic keywords). In 93 days, the system identified 80,049 onion services and characterized 90% of them, addressing the challenge of Tor volatility. A disproportionate amount of repeated content is found, with only 6.1% unique sites. From the HTML files of the dark sites, 31 different low-topics are extracted, manually labeled, and grouped into 11 high-level topics. The five most popular included sexual and violent content, repositories, search engines, carding, cryptocurrencies, and marketplaces. During the experiments, we identified 14 sites with 13,946 clones that shared a suspiciously similar mirroring rate per day, suggesting an extensive common phishing network. Among the related works, this study is the most representative characterization of onion services based on topics to date.
Tackling Cyberattacks through AI-based Reactive Systems: A Holistic Review and Future Vision
Dec 11, 2023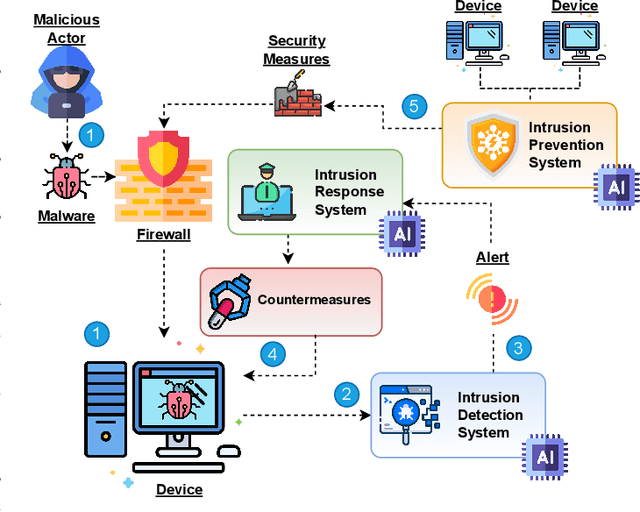

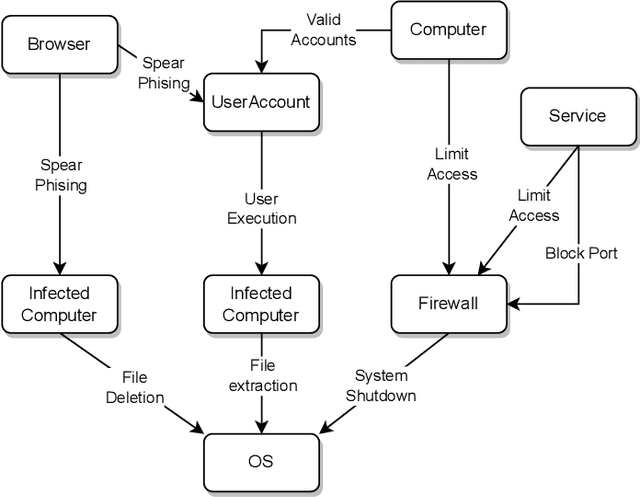
Abstract:There is no denying that the use of Information Technology (IT) is undergoing exponential growth in today's world. This digital transformation has also given rise to a multitude of security challenges, notably in the realm of cybercrime. In response to these growing threats, public and private sectors have prioritized the strengthening of IT security measures. In light of the growing security concern, Artificial Intelligence (AI) has gained prominence within the cybersecurity landscape. This paper presents a comprehensive survey of recent advancements in AI-driven threat response systems. To the best of our knowledge, the most recent survey covering the AI reaction domain was conducted in 2017. Since then, considerable literature has been published and therefore it is worth reviewing it. By means of several shared features, each of the studies is compared on a common ground. Through an analysis of the research papers conducted on a standardized basis, this survey aims to unravel the complexities and opportunities of integrating AI into cyber defense. The conclusions drawn from this collective analysis provide a comprehensive snapshot of the evolving landscape at the intersection of AI and cybersecurity. This landscape underscores the growing significance of not only anticipating and detecting threats but also responding to them effectively. Additionally, from these reviews, various research challenges for the future are presented. These challenges serve as a roadmap for researchers and practitioners in the field of AI-integrated reactive strategies.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge