Yingbo Hua
On Secret-Message Transmission by Echoing Encrypted Probes
Oct 04, 2024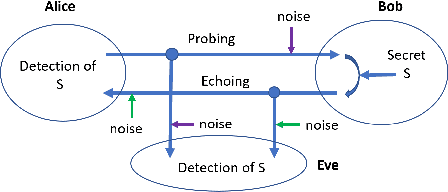
Abstract:A scheme for secure communications, called ``Secret-message Transmission by Echoing Encrypted Probes (STEEP)'', is revisited. STEEP is a round-trip scheme with a probing phase from one user to another and an echoing phase in the reverse direction. STEEP is broadly applicable to yield a positive secrecy rate in bits per channel use even if the receive channels at eavesdropper (Eve) are stronger than those between legitimate users in both directions. Differing from prior cases of STEEP, this paper presents STEEP in each of the following settings: using Gaussian channel probing (GCP) and Gaussian linear encryption (GLE) over MIMO channels; using phase-shift-keying (PSK) channel probing and PSK nonlinear encryption over SISO channels; and using GCP and GLE over multiple access channels. In each setting, Eve is assumed to have any number of antennas, and STEEP is shown to yield a positive secrecy rate subject to a sufficiently large power in the echoing phase relative to the power in the probing phase, as long as Eve's receive channel in the probing phase is not noiseless. Also shown is that the GCP-GLE based STEEP for two users, subject to a form of large powers from the users, has its secrecy rate approaching the secret-key capacity based on GCP.
A Simple Method for Secret-Key Generation Between Mobile Users Across Networks
Oct 03, 2024Abstract:Two or more mobiles users can continuously superimpose sequences of bits chosen from different packets or files already exchanged and authenticated between themselves to continuously renew a secret key for continuous strengthening of their privacy and authentication. This accumulative, adaptable and additive (AAA) method is discussed in this paper. The equivocation to Eve of any bit in the generated key by the AAA method equals to the probability that not all corresponding independent bits exchanged between the users are intercepted by Eve. This performance, achieved without using any knowledge of non-stationary probabilities of bits being intercepted by Eve, is compared to an established capacity achievable using that knowledge. A secrecy robustness of the AAA method against some correlations known to Eve is also discussed.
Unification of Secret Key Generation and Wiretap Channel Transmission
Mar 11, 2024



Abstract:This paper presents further insights into a recently developed round-trip communication scheme called ``Secret-message Transmission by Echoing Encrypted Probes (STEEP)''. A legitimate wireless channel between a multi-antenna user (Alice) and a single-antenna user (Bob) in the presence of a multi-antenna eavesdropper (Eve) is focused on. STEEP does not require full-duplex, channel reciprocity or Eve's channel state information, but is able to yield a positive secrecy rate in bits per channel use between Alice and Bob in every channel coherence period as long as Eve's receive channel is not noiseless. This secrecy rate does not diminish as coherence time increases. Various statistical behaviors of STEEP's secrecy capacity due to random channel fading are also illustrated.
Secret-Key Capacity from MIMO Channel Probing
Mar 04, 2024Abstract:Revealing expressions of secret-key capacity (SKC) based on data sets from Gaussian MIMO channel probing are presented. It is shown that Maurer's upper and lower bounds on SKC coincide when the used data sets are produced from one-way channel probing. As channel coherence time increases, SKC in bits per probing channel use is always lower bounded by a positive value unless eavesdropper's observations are noiseless, which is unlike SKC solely based on reciprocal channels.
Secret-Message Transmission by Echoing Encrypted Probes -- STEEP
Sep 25, 2023

Abstract:This paper examines the properties of the lower and upper bounds established by Maurer, Ahlswede and Csiszar (MAC) for secret-key capacity in the case of channel probing over single-input and single-output (SISO) channels. Inspired by the insights into MAC's bounds, a scheme called secret-message transmission by echoing encrypted probes (STEEP) is proposed. STEEP consists of two phases: in phase 1, Alice sends random probes over a probing channel to Bob; in phase 2, Bob echoes back an estimated version of the probes, but encrypted by a secret, over a high-quality return channel. Provided that Eve is unable to obtain the exact probes transmitted by Alice in phase 1, STEEP guarantees a positive secrecy rate from Bob to Alice over the return channel even if Eve's channel strength during channel probing is stronger than Bob's. STEEP is applicable to both physical layer and upper layers in connected networks.
Secure Degree of Freedom of Wireless Networks Using Collaborative Pilots
Sep 21, 2023Abstract:A wireless network of full-duplex nodes/users, using anti-eavesdropping channel estimation (ANECE) based on collaborative pilots, can yield a positive secure degree-of-freedom (SDoF) regardless of the number of antennas an eavesdropper may have. This paper presents novel results on SDoF of ANECE by analyzing secret-key capacity (SKC) of each pair of nodes in a network of multiple collaborative nodes per channel coherence period. Each transmission session of ANECE has two phases: phase 1 is used for pilots, and phase 2 is used for random symbols. This results in two parts of SDoF of ANECE. Both lower and upper bounds on the SDoF of ANECE for any number of users are shown, and the conditions for the two bounds to meet are given. This leads to important discoveries, including: a) The phase-1 SDoF is the same for both multi-user ANECE and pair-wise ANECE while the former may require only a fraction of the number of time slots needed by the latter; b) For a three-user network, the phase-2 SDoF of all-user ANECE is generally larger than that of pair-wise ANECE; c) For a two-user network, a modified ANECE deploying square-shaped nonsingular pilot matrices yields a higher total SDoF than the original ANECE. The multi-user ANECE and the modified two-user ANECE shown in this paper appear to be the best full-duplex schemes known today in terms of SDoF subject to each node using a given number of antennas for both transmitting and receiving.
Continuous Encryption Functions for Security Over Networks
Nov 04, 2021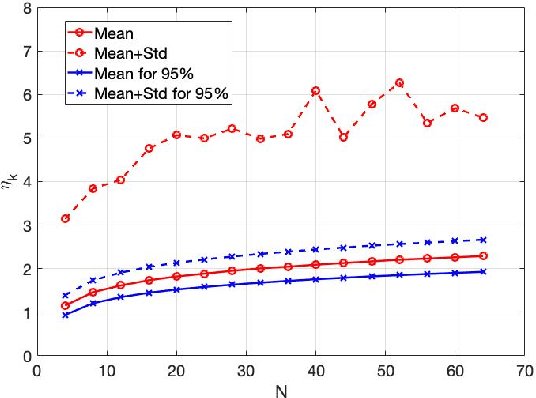
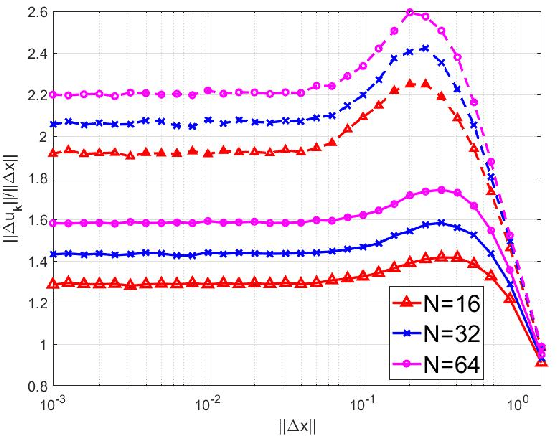
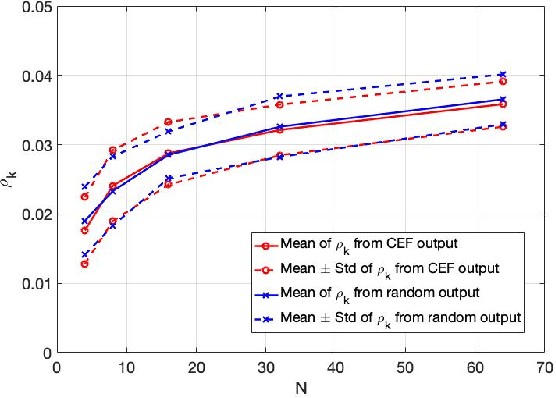
Abstract:This paper presents a study of continuous encryption functions (CEFs) of secret feature vectors for security over networks such as physical layer encryption for wireless communications and biometric template security for online Internet applications. CEFs are defined to include all prior continuous "one-way" functions. It is shown that dynamic random projection and index-of-max (IoM) hashing algorithm 1 are not hard to attack, IoM algorithm 2 is not as hard to attack as it was thought to be, and higher-order polynomials are easy to attack via substitution. Also presented is a new family of CEFs based on selected components of singular value decomposition (SVD) of a randomly modulated matrix of feature vector. Detailed empirical evidence suggests that SVD-CEF is hard to attack. Statistical analysis of SVD-CEF reveals its useful properties including its sensitivity to noise. The bit-error-rate performance of a quantized SVD-CEF is shown to exceed that of IoM algorithm 2.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge