Sokratis Katsikas
Impact of Recurrent Neural Networks and Deep Learning Frameworks on Real-time Lightweight Time Series Anomaly Detection
Jul 26, 2024



Abstract:Real-time lightweight time series anomaly detection has become increasingly crucial in cybersecurity and many other domains. Its ability to adapt to unforeseen pattern changes and swiftly identify anomalies enables prompt responses and critical decision-making. While several such anomaly detection approaches have been introduced in recent years, they primarily utilize a single type of recurrent neural networks (RNNs) and have been implemented in only one deep learning framework. It is unclear how the use of different types of RNNs available in various deep learning frameworks affects the performance of these anomaly detection approaches due to the absence of comprehensive evaluations. Arbitrarily choosing a RNN variant and a deep learning framework to implement an anomaly detection approach may not reflect its true performance and could potentially mislead users into favoring one approach over another. In this paper, we aim to study the influence of various types of RNNs available in popular deep learning frameworks on real-time lightweight time series anomaly detection. We reviewed several state-of-the-art approaches and implemented a representative anomaly detection approach using well-known RNN variants supported by three widely recognized deep learning frameworks. A comprehensive evaluation is then conducted to analyze the performance of each implementation across real-world, open-source time series datasets. The evaluation results provide valuable guidance for selecting the appropriate RNN variant and deep learning framework for real-time, lightweight time series anomaly detection.
GAD: A Real-time Gait Anomaly Detection System with Online Adaptive Learning
May 04, 2024



Abstract:Gait anomaly detection is a task that involves detecting deviations from a person's normal gait pattern. These deviations can indicate health issues and medical conditions in the healthcare domain, or fraudulent impersonation and unauthorized identity access in the security domain. A number of gait anomaly detection approaches have been introduced, but many of them require offline data preprocessing, offline model learning, setting parameters, and so on, which might restrict their effectiveness and applicability in real-world scenarios. To address these issues, this paper introduces GAD, a real-time gait anomaly detection system. GAD focuses on detecting anomalies within an individual's three-dimensional accelerometer readings based on dimensionality reduction and Long Short-Term Memory (LSTM). Upon being launched, GAD begins collecting a gait segment from the user and training an anomaly detector to learn the user's walking pattern on the fly. If the subsequent model verification is successful, which involves validating the trained detector using the user's subsequent steps, the detector is employed to identify abnormalities in the user's subsequent gait readings at the user's request. The anomaly detector will be retained online to adapt to minor pattern changes and will undergo retraining as long as it cannot provide adequate prediction. We explored two methods for capturing users' gait segments: a personalized method tailored to each individual's step length, and a uniform method utilizing a fixed step length. Experimental results using an open-source gait dataset show that GAD achieves a higher detection accuracy ratio when combined with the personalized method.
A Location-Based Global Authorization Method for Underwater Security
Oct 14, 2022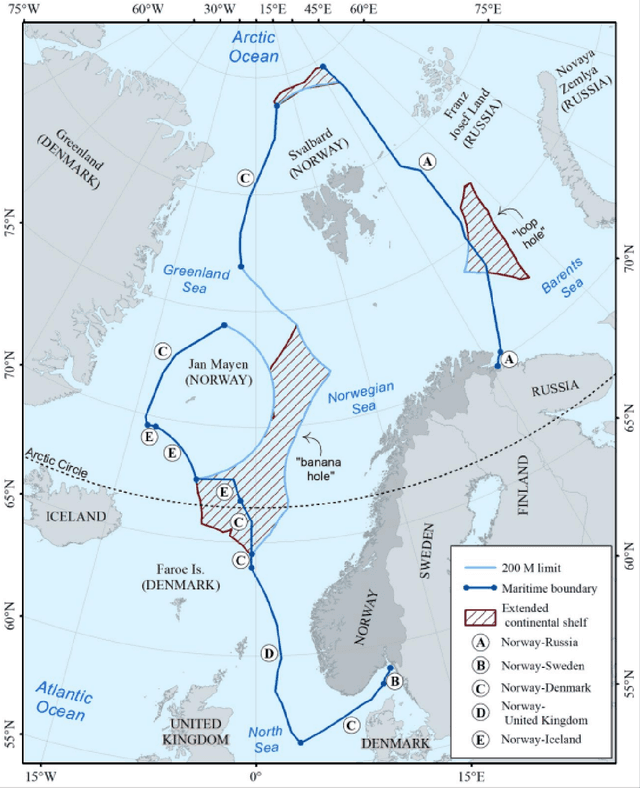
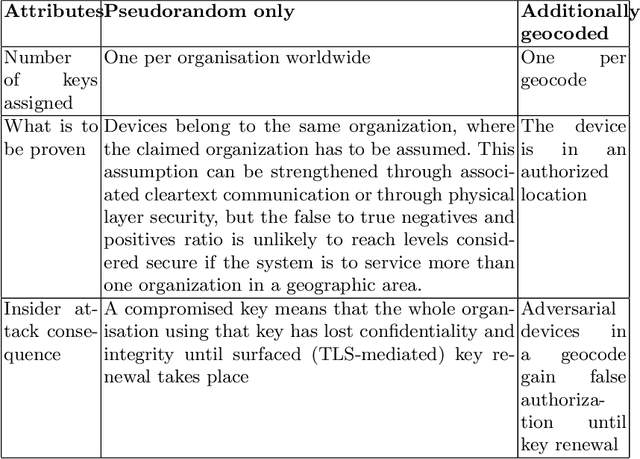
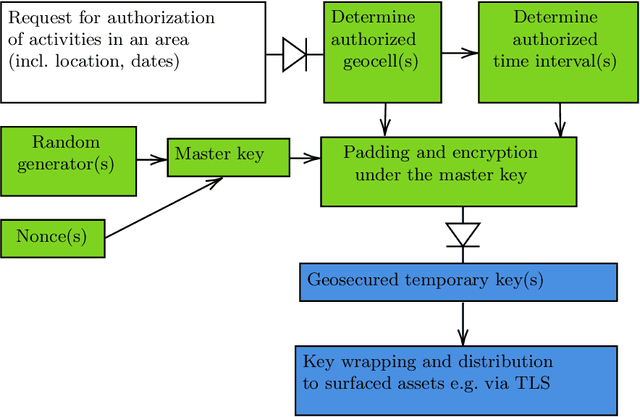
Abstract:National or international maritime authorities are used to handle requests for licenses for all kinds of marine activities. These licenses constitute authorizations limited in time and space, but there is no technical security service to check for the authorization of a wide range of marine assets. We have noted secure AIS solutions suitable for more or less constantly internet-connected assets such as ships with satellite connections. The additional constraints posed by underwater autonomous assets, namely less power and connectivity, can be mitigated by using symmetric cryptography. We propose a security service that allows the automatized check of asset authorization status based on large symmetric keys. Key generation can take place at a central authority according to the time and space limitations of a license, i.e. timestamped and geocoded. Our solution harnesses the exceptionally large key size of the RC5 cipher and the standardized encoding of geocells in the Open Location Code system. While we developed and described our solution for offshore underwater use, aerial and terrestrial environments could also make use of it if they are similarly bandwidth constrained or want to rely on quantum-resistant and computationally economic symmetric methods.
Authentication of Underwater Assets
Sep 05, 2022
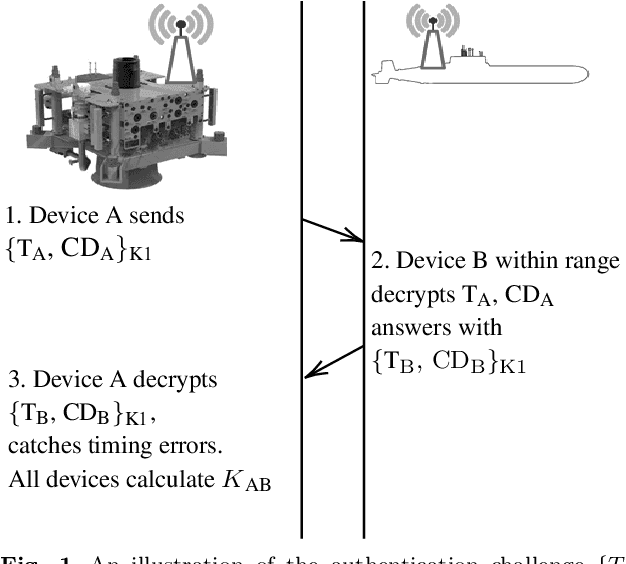
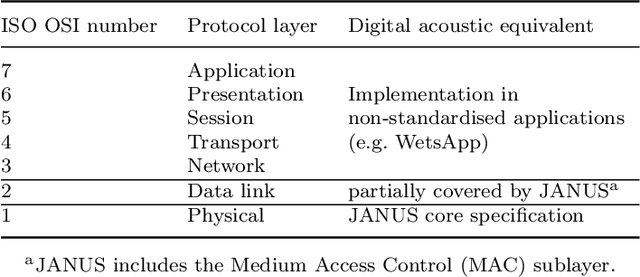
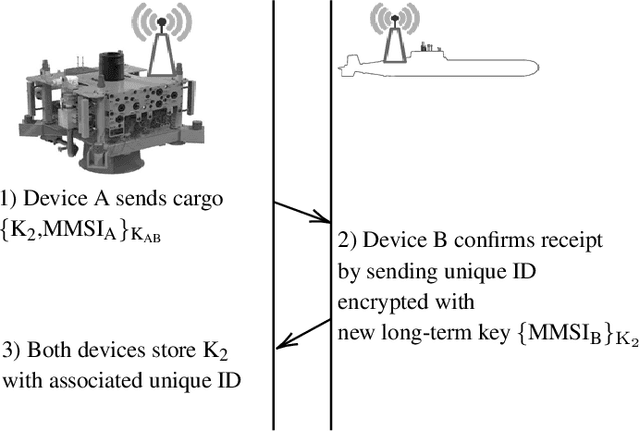
Abstract:Secure digital wireless communication underwater has become a key issue as maritime operations shift towards employing a heterogeneous mix of robotic assets and as the security of digital systems becomes challenged across all domains. At the same time, a proliferation of underwater signal coding and physical layer options are delivering greater bandwidth and flexibility, but mostly without the standards necessary for interoperability. We address here an essential requirement for security, namely a confirmation of asset identities also known as authentication. We propose, implement, verify and validate an authentication protocol based on the first digital underwater communications standard. Our scheme is applicable primarily to AUVs operating around offshore oil and gas facilities, but also to other underwater devices that may in the future have acoustic modems. It makes communication including command and control significantly more secure and provides a foundation for the development of more sophisticated security mechanisms.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge