Sarbani Ghose
Opportunistic User Scheduling for Secure RIS-aided Wireless Communications
Mar 05, 2024Abstract:In this paper, we provide expressions for the secrecy outage probability (SOP) for suboptimal and optimal opportunistic scheduling schemes in a reconfigurable intelligent surface (RIS) aided system with multiple eavesdroppers in approximate closed form. A suboptimal scheduling (SS) scheme is analyzed, which is used when the channel state information (CSI) of the eavesdropping links is unavailable, and the optimal scheduling (OS) scheme is also analyzed, which is used when the global CSI is available. For each scheme, we provide a simplified expression for the SOP in the high signal-to-noise ratio (SNR) regime to demonstrate its behavior as a function of the key system parameters. At high SNR, the SOP saturates to a constant level which decreases exponentially with the number of RIS elements in the SS scheme and with the product of the number of RIS elements and the number of users in the OS scheme. We compare the performance of the opportunistic user scheduling schemes with that of a non-orthogonal multiple access (NOMA) based scheduling scheme which chooses a pair of users in each time slot for scheduling and we show that the opportunistic schemes outperform the NOMA-based scheme. We also derive a closed-form expression for the SOP of a decode-and-forward (DF) relay-aided scheduling scheme in order to compare it with that of the RIS-aided system. It is found that the RIS-aided system outperforms the relay-aided systems when the number of RIS elements is sufficiently large. An increased number of RIS elements is required to outperform the relay-aided system at higher operating frequencies.
Jointly Optimal RIS Placement and Power Allocation for Underlay D2D Communications: An Outage Probability Minimization Approach
Jan 07, 2024Abstract:In this paper, we study underlay device-to-device (D2D) communication systems empowered by a reconfigurable intelligent surface (RIS) for cognitive cellular networks. Considering Rayleigh fading channels and the general case where there exist both the direct and RIS-enabled D2D channels, the outage probability (OP) of the D2D communication link is presented in closed-form. Next, for the considered RIS-empowered underlaid D2D system, we frame an OP minimization problem. We target the joint optimization of the transmit power at the D2D source and the RIS placement, under constraints on the transmit power at the D2D source and on the limited interference imposed on the cellular user for two RIS deployment topologies. Due to the coupled optimization variables, the formulated optimization problem is extremely intractable. We propose an equivalent transformation which we are able to solve analytically. In the transformed problem, an expression for the average value of the signal-to-interference-noise ratio (SINR) at the D2D receiver is derived in closed-form. Our theoretical derivations are corroborated through simulation results, and various system design insights are deduced. It is indicatively showcased that the proposed RIS-empowered underlaid D2D system design outperforms the benchmark semi-adaptive optimal power and optimal distance schemes, offering $44\%$ and $20\%$ performance improvement, respectively.
Secrecy of Opportunistic User Scheduling in RIS-Aided Systems: A Comparison with NOMA Scheduling
Jun 05, 2023Abstract:In this paper, we propose an opportunistic user scheduling scheme in a multi-user reconfigurable intelligent surface (RIS) aided wireless system to improve secrecy. We derive the secrecy outage probability (SOP) and its asymptotic expression in approximate closed form. The asymptotic analysis shows that the SOP does not depend on the transmitter-to-RIS distance and saturates to a fixed value depending on the ratio of the path loss of the RIS-to-destination and RIS-to-eavesdropper links and the number of users at high signal-to-noise ratio. It is shown that increasing the number of RIS elements leads to an exponential decrease in the SOP. We also compare our scheme with that of a non-orthogonal multiple access (NOMA) scheduling scheme, which chooses a pair of users to schedule in each time slot. The comparison shows that the SOP of all of the NOMA users is compromised, and that our proposed scheduling scheme has better performance.
Secrecy Outage of Dual-hop Regenerative Multi-relay System with Relay Selection
Mar 07, 2021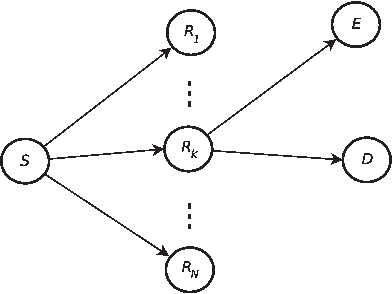
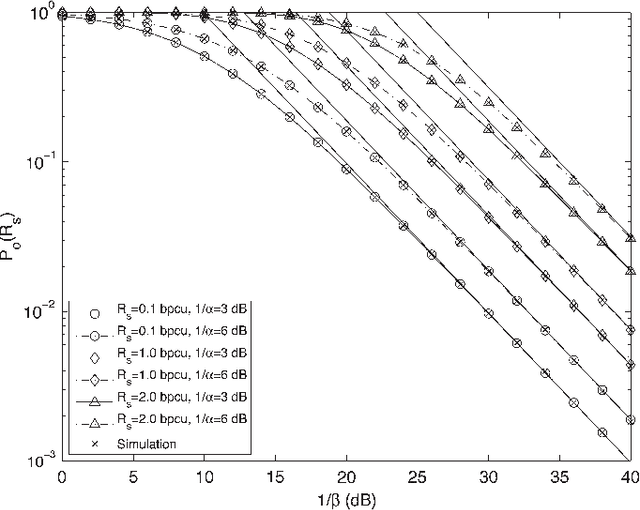
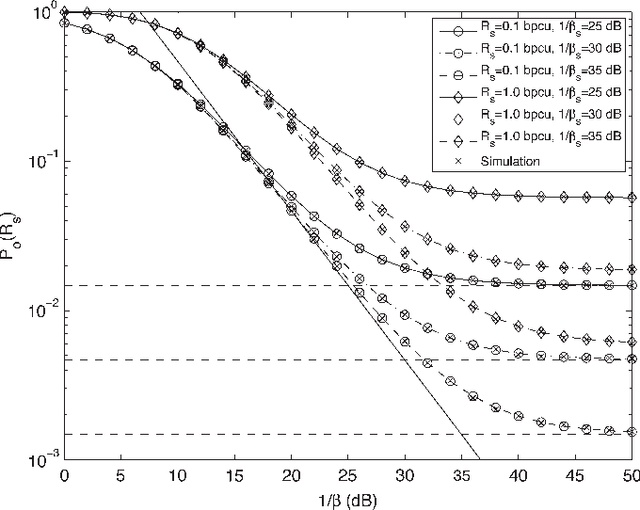
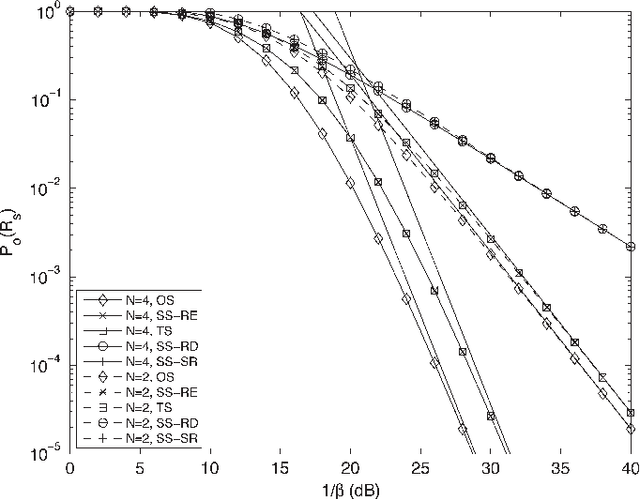
Abstract:Relay selection is considered to enhance the secrecy of a dual-hop regenerative multi-relay system with an eavesdropper. Without assuming perfect decoding at the relays, the secrecy outage probability of a single relay system is obtained first. Secrecy outage of optimal, traditional and suboptimal relay selection schemes is then evaluated. To reduce the power consumption, partial relay selection schemes based only on either of the source-relay or relay-destination instantaneous channel state information (ICSI) are introduced. Its secrecy outage is evaluated and compared with the other schemes. Secrecy outage of all the selection schemes are obtained in closed-form. An optimal relay selection scheme is proposed using secrecy outage which does not require any ICSI. Asymptotic and diversity gain analysis of the secrecy outage is presented when source-relay and relay-destination average SNRs are same or different. We observe that the improvement in eavesdropper link quality affects the secrecy outage more when required secrecy rate is low as compared to the case when rate is high. We also observe that relay selection improves performance more when number of relays are more. It is important to note that either of the source-relay or the relay-destination link quality can equally limit the secrecy outage performance even if the other link quality is infinitely good.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge