Mohamed K. M. Fadul
Transformers -- Messages in Disguise
Nov 15, 2024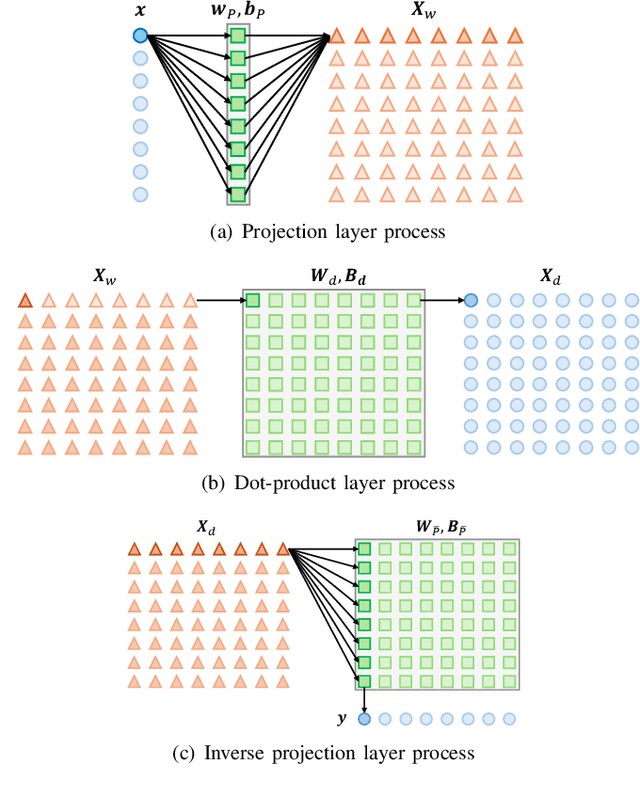
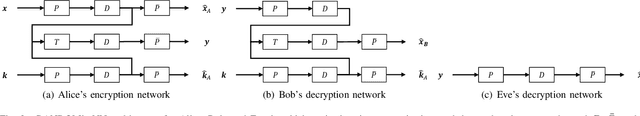

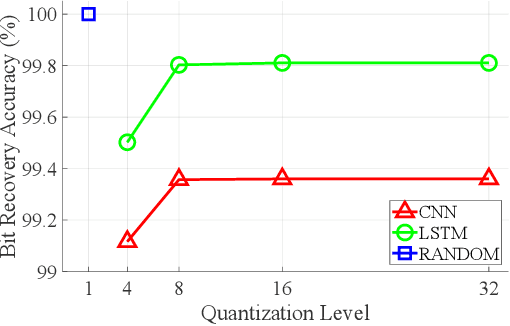
Abstract:Modern cryptography, such as Rivest Shamir Adleman (RSA) and Secure Hash Algorithm (SHA), has been designed by humans based on our understanding of cryptographic methods. Neural Network (NN) based cryptography is being investigated due to its ability to learn and implement random cryptographic schemes that may be harder to decipher than human-designed algorithms. NN based cryptography may create a new cryptographic scheme that is NN specific and that changes every time the NN is (re)trained. This is attractive since it would require an adversary to restart its process(es) to learn or break the cryptographic scheme every time the NN is (re)trained. Current challenges facing NN-based encryption include additional communication overhead due to encoding to correct bit errors, quantizing the continuous-valued output of the NN, and enabling One-Time-Pad encryption. With this in mind, the Random Adversarial Data Obfuscation Model (RANDOM) Adversarial Neural Cryptography (ANC) network is introduced. RANDOM is comprised of three new NN layers: the (i) projection layer, (ii) inverse projection layer, and (iii) dot-product layer. This results in an ANC network that (i) is computationally efficient, (ii) ensures the encrypted message is unique to the encryption key, and (iii) does not induce any communication overhead. RANDOM only requires around 100 KB to store and can provide up to 2.5 megabytes per second of end-to-end encrypted communication.
Assessing Adversarial Replay and Deep Learning-Driven Attacks on Specific Emitter Identification-based Security Approaches
Aug 07, 2023Abstract:Specific Emitter Identification (SEI) detects, characterizes, and identifies emitters by exploiting distinct, inherent, and unintentional features in their transmitted signals. Since its introduction, a significant amount of work has been conducted; however, most assume the emitters are passive and that their identifying signal features are immutable and challenging to mimic. Suggesting the emitters are reluctant and incapable of developing and implementing effective SEI countermeasures; however, Deep Learning (DL) has been shown capable of learning emitter-specific features directly from their raw in-phase and quadrature signal samples, and Software-Defined Radios (SDRs) can manipulate them. Based on these capabilities, it is fair to question the ease at which an emitter can effectively mimic the SEI features of another or manipulate its own to hinder or defeat SEI. This work considers SEI mimicry using three signal features mimicking countermeasures; off-the-self DL; two SDRs of different sizes, weights, power, and cost (SWaP-C); handcrafted and DL-based SEI processes, and a coffee shop deployment. Our results show off-the-shelf DL algorithms, and SDR enables SEI mimicry; however, adversary success is hindered by: the use of decoy emitter preambles, the use of a denoising autoencoder, and SDR SWaP-C constraints.
An Investigation into the Impacts of Deep Learning-based Re-sampling on Specific Emitter Identification Performance
May 05, 2023



Abstract:Increasing Internet of Things (IoT) deployments present a growing surface over which villainous actors can carry out attacks. This disturbing revelation is amplified by the fact that a majority of IoT devices use weak or no encryption at all. Specific Emitter Identification (SEI) is an approach intended to address this IoT security weakness. This work provides the first Deep Learning (DL) driven SEI approach that upsamples the signals after collection to improve performance while simultaneously reducing the hardware requirements of the IoT devices that collect them. DL-driven upsampling results in superior SEI performance versus two traditional upsampling approaches and a convolutional neural network only approach.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge