Mike Borowczak
SAGA: Synthesis Augmentation with Genetic Algorithms for In-Memory Sequence Optimization
Jun 14, 2024



Abstract:The von-Neumann architecture has a bottleneck which limits the speed at which data can be made available for computation. To combat this problem, novel paradigms for computing are being developed. One such paradigm, known as in-memory computing, interleaves computation with the storage of data within the same circuits. MAGIC, or Memristor Aided Logic, is an approach which uses memory circuits which physically perform computation through write operations to memory. Sequencing these operations is a computationally difficult problem which is directly correlated with the cost of solutions using MAGIC based in-memory computation. SAGA models the execution sequences as a topological sorting problem which makes the optimization well-suited for genetic algorithms. We then detail the formation and implementation of these genetic algorithms and evaluate them over a number of open circuit implementations. The memory-footprint needed for evaluating each of these circuits is decreased by up to 52% from existing, greedy-algorithm-based optimization solutions. Over the 10 benchmark circuits evaluated, these modifications lead to an overall improvement in the efficiency of in-memory circuit evaluation of 128% in the best case and 27.5% on average.
Dynamic Anonymized Evaluation for Behavioral Continuous Authentication
Mar 07, 2019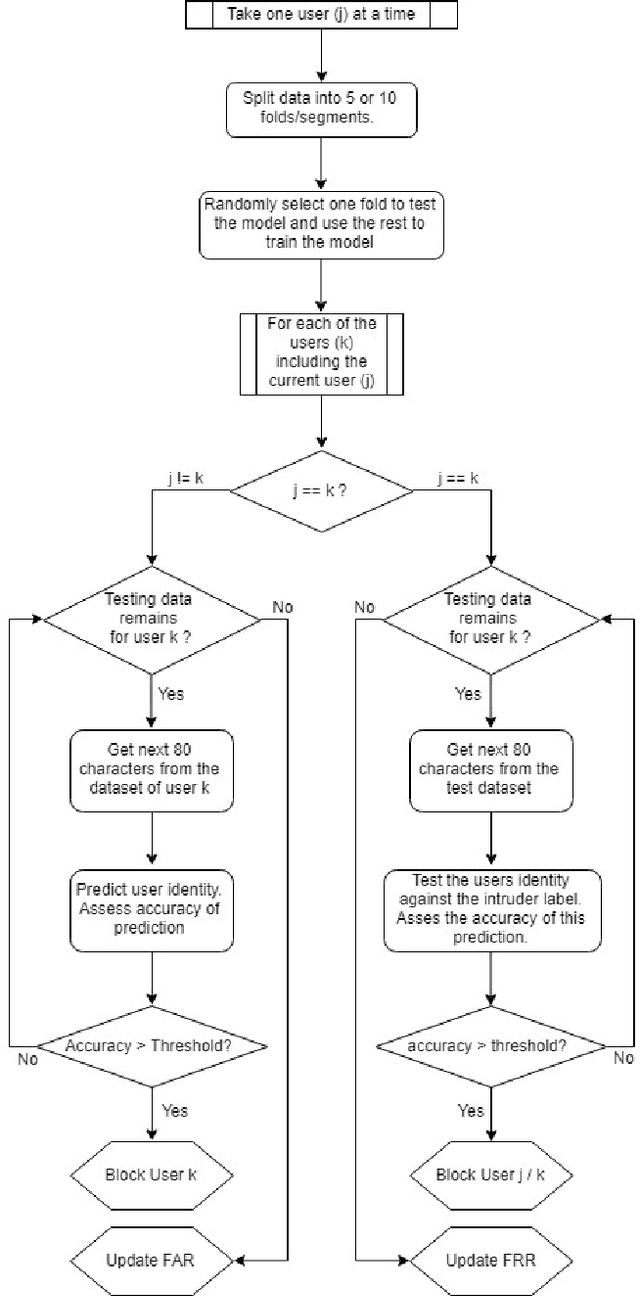
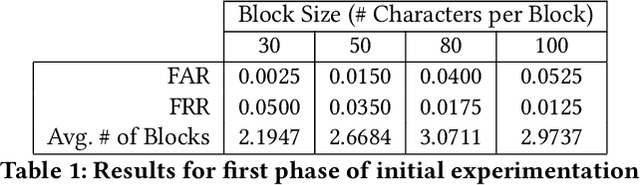
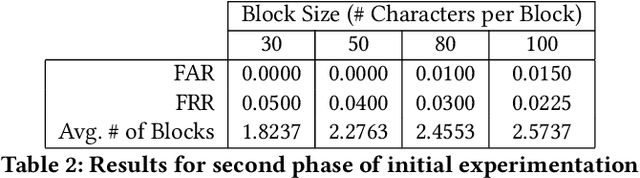
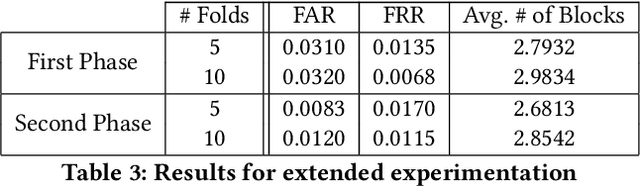
Abstract:Emerging technology demands reliable authentication mechanisms, particularly in interconnected systems. Current systems rely on a single moment of authentication, however continuous authentication systems assess a users identity utilizing a constant biometric analysis. Spy Hunter, a continuous authentication mechanism uses keystroke dynamics to validate users over blocks of data. This easily-incorporated periodic biometric authentication system validates genuine users and detects intruders quickly. Because it verifies users in the background, Spy Hunter is not constrained to a password box. Instead, it is flexible and can be layered with other mechanisms to provide high-level security. Where other continuous authentication techniques rely on scripted typing, Spy Hunter validates over free text in authentic environments. This is accomplished in two phases, one where the user is provided a prompt and another where the user is allowed free access to their computer. Additionally, Spy Hunter focuses on the timing of different keystrokes rather than the specific key being pressed. This allows for anonymous data to authenticate users and avoids holding personal data. Utilizing a couple K-fold cross-validation techniques, Spy Hunter is assessed based on how often the system falsely accepts an intruder, how often the system falsely rejects a genuine user, and the time it takes to validate a users identity. Spy Hunter maintains error rates below 6% and identifies users in minimal numbers of keystrokes. Continuous authentication provides higher level security than one-time verification processes and Spy Hunter expands on the possibilities for behavioral analysis based on keystroke dynamics.
Predictive Liability Models and Visualizations of High Dimensional Retail Employee Data
Mar 29, 2018
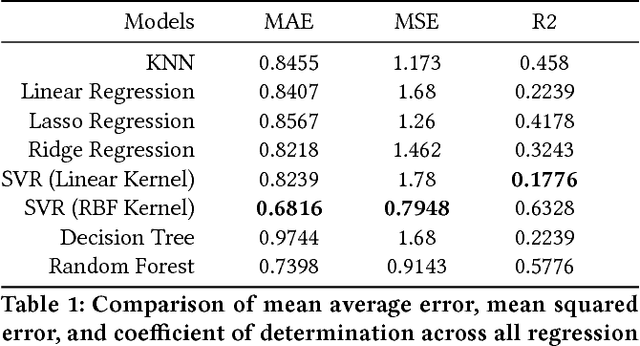
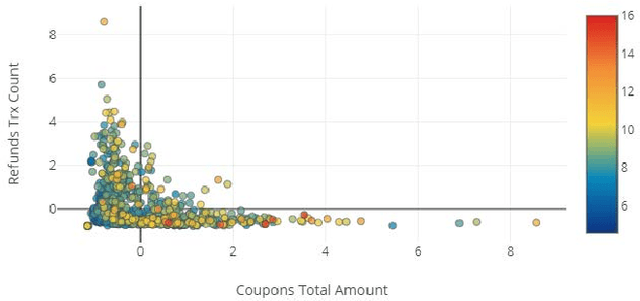
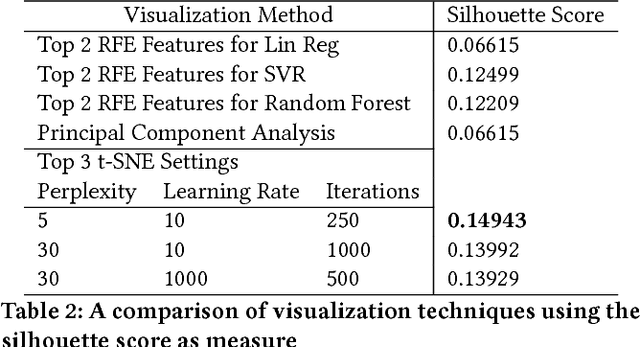
Abstract:Employee theft and dishonesty is a major contributor to loss in the retail industry. Retailers have reported the need for more automated analytic tools to assess the liability of their employees. In this work, we train and optimize several machine learning models for regression prediction and analysis on this data, which will help retailers identify and manage risky employees. Since the data we use is very high dimensional, we use feature selection techniques to identify the most contributing factors to an employee's assessed risk. We also use dimension reduction and data embedding techniques to present this dataset in a easy to interpret format.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge