Matthew C Stamm
Attacking Image Splicing Detection and Localization Algorithms Using Synthetic Traces
Nov 22, 2022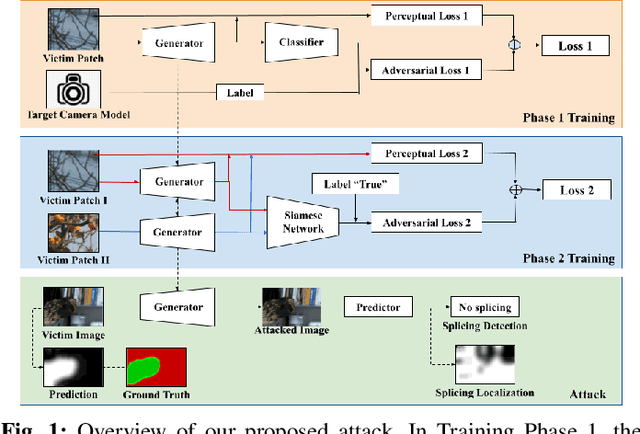
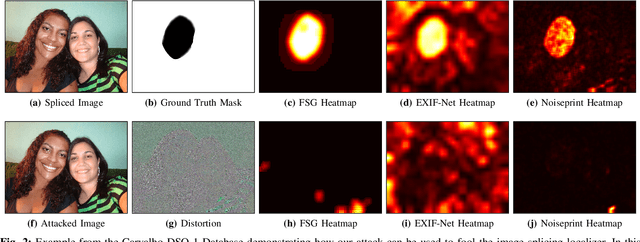

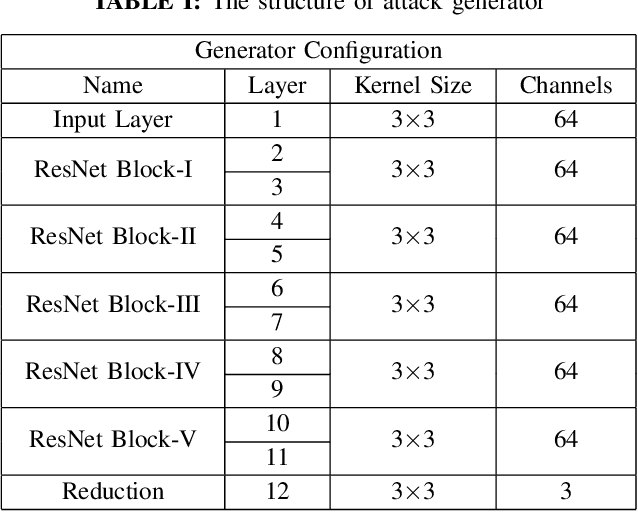
Abstract:Recent advances in deep learning have enabled forensics researchers to develop a new class of image splicing detection and localization algorithms. These algorithms identify spliced content by detecting localized inconsistencies in forensic traces using Siamese neural networks, either explicitly during analysis or implicitly during training. At the same time, deep learning has enabled new forms of anti-forensic attacks, such as adversarial examples and generative adversarial network (GAN) based attacks. Thus far, however, no anti-forensic attack has been demonstrated against image splicing detection and localization algorithms. In this paper, we propose a new GAN-based anti-forensic attack that is able to fool state-of-the-art splicing detection and localization algorithms such as EXIF-Net, Noiseprint, and Forensic Similarity Graphs. This attack operates by adversarially training an anti-forensic generator against a set of Siamese neural networks so that it is able to create synthetic forensic traces. Under analysis, these synthetic traces appear authentic and are self-consistent throughout an image. Through a series of experiments, we demonstrate that our attack is capable of fooling forensic splicing detection and localization algorithms without introducing visually detectable artifacts into an attacked image. Additionally, we demonstrate that our attack outperforms existing alternative attack approaches. %
Primary and Secondary Social Media Source Identification
May 05, 2021
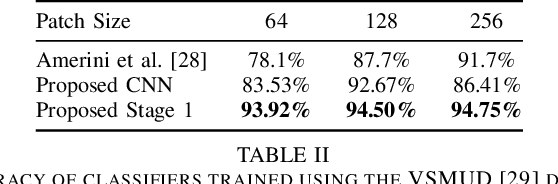
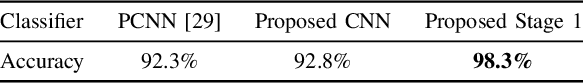
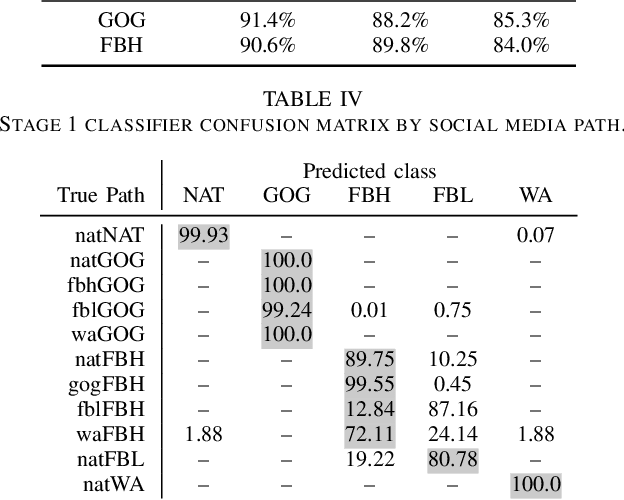
Abstract:Social networks like Facebook and WhatsApp have enabled users to share images with other users around the world. Along with this has come the rapid spread of misinformation. One step towards verifying the authenticity of an image is understanding its origin, including it distribution history through social media. In this paper, we present a method for tracing the posting history of an image across different social networks. To do this, we propose a two-stage deep-learning-based approach, which takes advantage of cascaded fingerprints in images left by social networks during uploading. Our proposed system is not reliant upon metadata or similar easily falsifiable information. Through a series of experiments, we show that we are able to outperform existing social media source identification algorithms. and identify chains of social networks up to length two with over over 84% accuracy.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge