M. Abdullah Canbaz
LegalGuardian: A Privacy-Preserving Framework for Secure Integration of Large Language Models in Legal Practice
Jan 19, 2025



Abstract:Large Language Models (LLMs) hold promise for advancing legal practice by automating complex tasks and improving access to justice. However, their adoption is limited by concerns over client confidentiality, especially when lawyers include sensitive Personally Identifiable Information (PII) in prompts, risking unauthorized data exposure. To mitigate this, we introduce LegalGuardian, a lightweight, privacy-preserving framework tailored for lawyers using LLM-based tools. LegalGuardian employs Named Entity Recognition (NER) techniques and local LLMs to mask and unmask confidential PII within prompts, safeguarding sensitive data before any external interaction. We detail its development and assess its effectiveness using a synthetic prompt library in immigration law scenarios. Comparing traditional NER models with one-shot prompted local LLM, we find that LegalGuardian achieves a F1-score of 93% with GLiNER and 97% with Qwen2.5-14B in PII detection. Semantic similarity analysis confirms that the framework maintains high fidelity in outputs, ensuring robust utility of LLM-based tools. Our findings indicate that legal professionals can harness advanced AI technologies without compromising client confidentiality or the quality of legal documents.
Federated Learning in Adversarial Environments: Testbed Design and Poisoning Resilience in Cybersecurity
Sep 15, 2024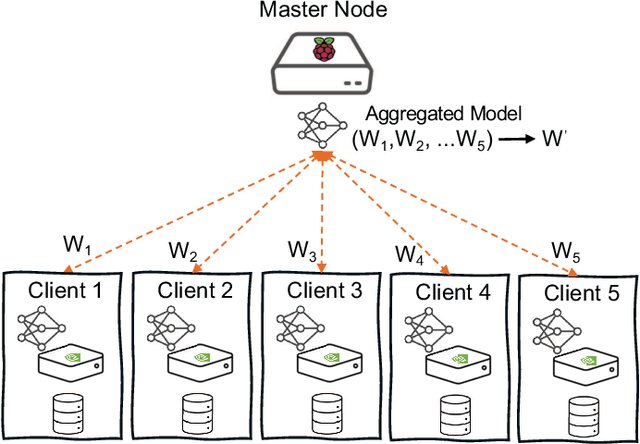
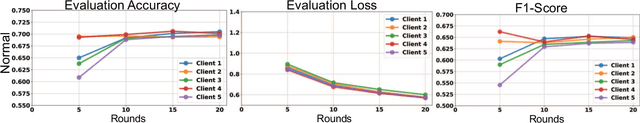
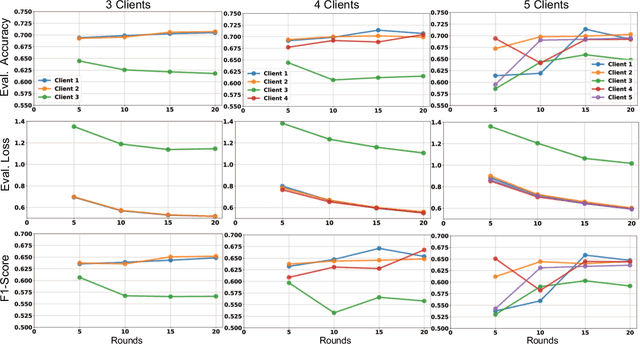
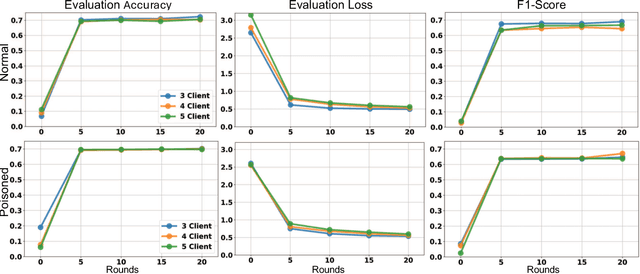
Abstract:This paper presents the design and implementation of a Federated Learning (FL) testbed, focusing on its application in cybersecurity and evaluating its resilience against poisoning attacks. Federated Learning allows multiple clients to collaboratively train a global model while keeping their data decentralized, addressing critical needs for data privacy and security, particularly in sensitive fields like cybersecurity. Our testbed, built using the Flower framework, facilitates experimentation with various FL frameworks, assessing their performance, scalability, and ease of integration. Through a case study on federated intrusion detection systems, we demonstrate the testbed's capabilities in detecting anomalies and securing critical infrastructure without exposing sensitive network data. Comprehensive poisoning tests, targeting both model and data integrity, evaluate the system's robustness under adversarial conditions. Our results show that while federated learning enhances data privacy and distributed learning, it remains vulnerable to poisoning attacks, which must be mitigated to ensure its reliability in real-world applications.
LLM Honeypot: Leveraging Large Language Models as Advanced Interactive Honeypot Systems
Sep 12, 2024



Abstract:The rapid evolution of cyber threats necessitates innovative solutions for detecting and analyzing malicious activity. Honeypots, which are decoy systems designed to lure and interact with attackers, have emerged as a critical component in cybersecurity. In this paper, we present a novel approach to creating realistic and interactive honeypot systems using Large Language Models (LLMs). By fine-tuning a pre-trained open-source language model on a diverse dataset of attacker-generated commands and responses, we developed a honeypot capable of sophisticated engagement with attackers. Our methodology involved several key steps: data collection and processing, prompt engineering, model selection, and supervised fine-tuning to optimize the model's performance. Evaluation through similarity metrics and live deployment demonstrated that our approach effectively generates accurate and informative responses. The results highlight the potential of LLMs to revolutionize honeypot technology, providing cybersecurity professionals with a powerful tool to detect and analyze malicious activity, thereby enhancing overall security infrastructure.
Harnessing Deep Learning and Satellite Imagery for Post-Buyout Land Cover Mapping
Jan 15, 2024



Abstract:Environmental disasters such as floods, hurricanes, and wildfires have increasingly threatened communities worldwide, prompting various mitigation strategies. Among these, property buyouts have emerged as a prominent approach to reducing vulnerability to future disasters. This strategy involves governments purchasing at-risk properties from willing sellers and converting the land into open space, ostensibly reducing future disaster risk and impact. However, the aftermath of these buyouts, particularly concerning land-use patterns and community impacts, remains under-explored. This research aims to fill this gap by employing innovative techniques like satellite imagery analysis and deep learning to study these patterns. To achieve this goal, we employed FEMA's Hazard Mitigation Grant Program (HMGP) buyout dataset, encompassing over 41,004 addresses of these buyout properties from 1989 to 2017. Leveraging Google's Maps Static API, we gathered 40,053 satellite images corresponding to these buyout lands. Subsequently, we implemented five cutting-edge machine learning models to evaluate their performance in classifying land cover types. Notably, this task involved multi-class classification, and our model achieved an outstanding ROC-AUC score of 98.86%
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge