Ijaz Ahmad
Advanced Multimodal Learning for Seizure Detection and Prediction: Concept, Challenges, and Future Directions
Jan 08, 2026Abstract:Epilepsy is a chronic neurological disorder characterized by recurrent unprovoked seizures, affects over 50 million people worldwide, and poses significant risks, including sudden unexpected death in epilepsy (SUDEP). Conventional unimodal approaches, primarily reliant on electroencephalography (EEG), face several key challenges, including low SNR, nonstationarity, inter- and intrapatient heterogeneity, portability, and real-time applicability in clinical settings. To address these issues, a comprehensive survey highlights the concept of advanced multimodal learning for epileptic seizure detection and prediction (AMLSDP). The survey presents the evolution of epileptic seizure detection (ESD) and prediction (ESP) technologies across different eras. The survey also explores the core challenges of multimodal and non-EEG-based ESD and ESP. To overcome the key challenges of the multimodal system, the survey introduces the advanced processing strategies for efficient AMLSDP. Furthermore, this survey highlights future directions for researchers and practitioners. We believe this work will advance neurotechnology toward wearable and imaging-based solutions for epilepsy monitoring, serving as a valuable resource for future innovations in this domain.
Deep Learning Frameworks for Cognitive Radio Networks: Review and Open Research Challenges
Oct 31, 2024



Abstract:Deep learning has been proven to be a powerful tool for addressing the most significant issues in cognitive radio networks, such as spectrum sensing, spectrum sharing, resource allocation, and security attacks. The utilization of deep learning techniques in cognitive radio networks can significantly enhance the network's capability to adapt to changing environments and improve the overall system's efficiency and reliability. As the demand for higher data rates and connectivity increases, B5G/6G wireless networks are expected to enable new services and applications significantly. Therefore, the significance of deep learning in addressing cognitive radio network challenges cannot be overstated. This review article provides valuable insights into potential solutions that can serve as a foundation for the development of future B5G/6G services. By leveraging the power of deep learning, cognitive radio networks can pave the way for the next generation of wireless networks capable of meeting the ever-increasing demands for higher data rates, improved reliability, and security.
Channel model for end-to-end learning of communications systems: A survey
Apr 08, 2022
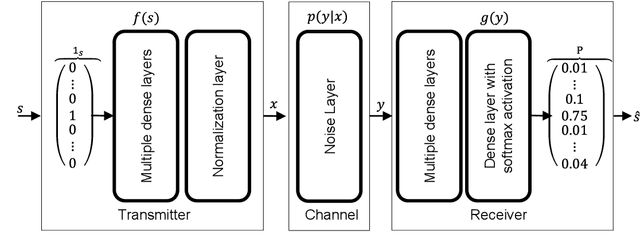
Abstract:The traditional communication model based on chain of multiple independent processing blocks is constraint to efficiency and introduces artificial barriers. Thus, each individually optimized block does not guarantee end-to-end performance of the system. Recently, end-to-end learning of communications systems through machine learning (ML) have been proposed to optimize the system metrics jointly over all components. These methods show performance improvements but has a limitation that it requires a differentiable channel model. In this study, we have summarized the existing approaches that alleviates this problem. We believe that this study will provide better understanding of the topic and an insight into future research in this field.
Just-Noticeable-Difference Based Edge Map Quality Measure
Apr 07, 2022

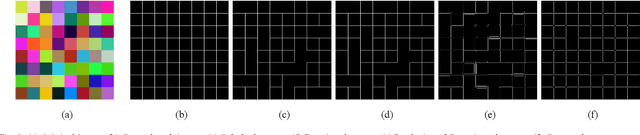
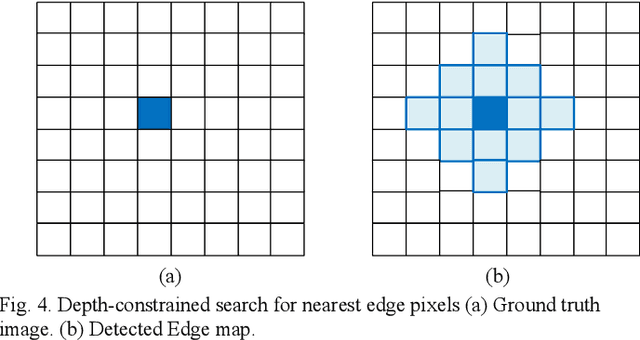
Abstract:The performance of an edge detector can be improved when assisted with an effective edge map quality measure. Several evaluation methods have been proposed resulting in different performance score for the same candidate edge map. However, an effective measure is the one that can be automated and which correlates with human judgement perceived quality of the edge map. Distance-based edge map measures are widely used for assessment of edge map quality. These methods consider distance and statistical properties of edge pixels to estimate a performance score. The existing methods can be automated; however, they lack perceptual features. This paper presents edge map quality measure based on Just-Noticeable-Difference (JND) feature of human visual system, to compensate the shortcomings of distance-based edge measures. For this purpose, we have designed constant stimulus experiment to measure the JND value for two spatial alternative. Experimental results show that JND based distance calculation outperforms existing distance-based measures according to subjective evaluation.
A Pixel-based Encryption Method for Privacy-Preserving Deep Learning Models
Mar 31, 2022
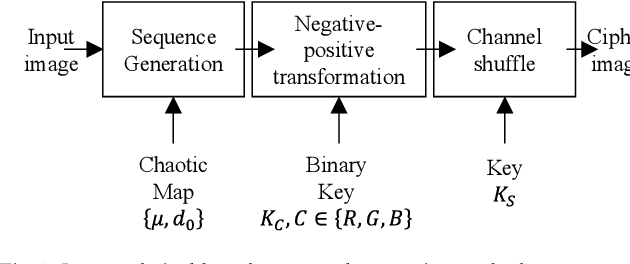
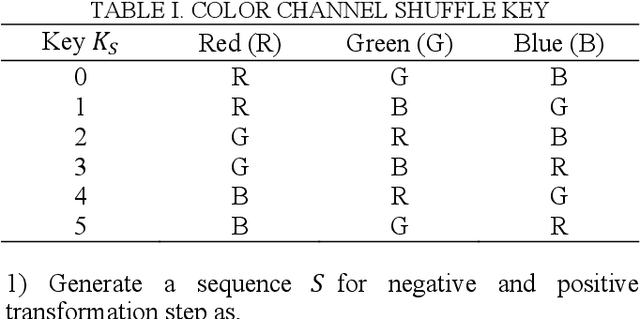
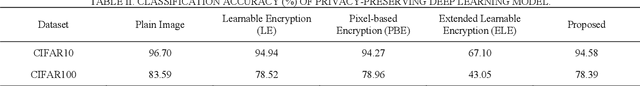
Abstract:In the recent years, pixel-based perceptual algorithms have been successfully applied for privacy-preserving deep learning (DL) based applications. However, their security has been broken in subsequent works by demonstrating a chosen-plaintext attack. In this paper, we propose an efficient pixel-based perceptual encryption method. The method provides a necessary level of security while preserving the intrinsic properties of the original image. Thereby, can enable deep learning (DL) applications in the encryption domain. The method is substitution based where pixel values are XORed with a sequence (as opposed to a single value used in the existing methods) generated by a chaotic map. We have used logistic maps for their low computational requirements. In addition, to compensate for any inefficiency because of the logistic maps, we use a second key to shuffle the sequence. We have compared the proposed method in terms of encryption efficiency and classification accuracy of the DL models on them. We have validated the proposed method with CIFAR datasets. The analysis shows that when classification is performed on the cipher images, the model preserves accuracy of the existing methods while provides better security.
Challenges of AI in Wireless Networks for IoT
Jul 09, 2020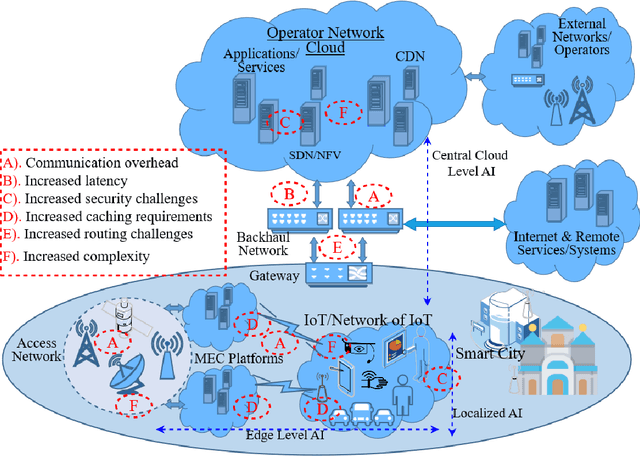
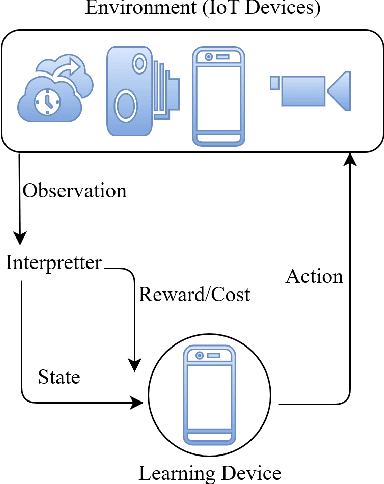
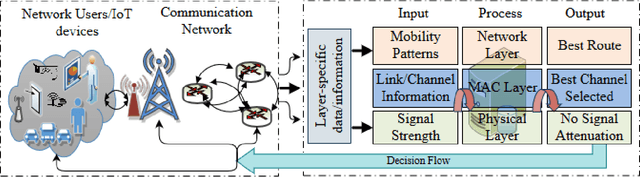
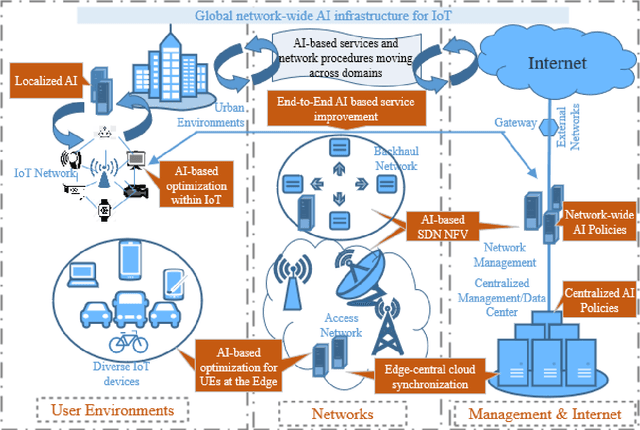
Abstract:The Internet of Things (IoT), hailed as the enabler of the next industrial revolution, will require ubiquitous connectivity, context-aware and dynamic service mobility, and extreme security through the wireless network infrastructure. Artificial Intelligence (AI), thus, will play a major role in the underlying network infrastructure. However, a number of challenges will surface while using the concepts, tools and algorithms of AI in wireless networks used by IoT. In this article, the main challenges in using AI in the wireless network infrastructure that facilitate end-to-end IoT communication are highlighted with potential generalized solution and future research directions.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge