Giuseppe Cascavilla
Breadcrumbs in the Digital Forest: Tracing Criminals through Torrent Metadata with OSINT
Jan 04, 2026Abstract:This work investigates the potential of torrent metadata as a source for open-source intelligence (OSINT), with a focus on user profiling and behavioral analysis. While peer-to-peer (P2P) networks such as BitTorrent are well studied with respect to privacy and performance, their metadata is rarely used for investigative purposes. This work presents a proof of concept demonstrating how tracker responses, torrent index data, and enriched IP metadata can reveal patterns associated with high-risk behavior. The research follows a five-step OSINT process: source identification, data collection, enrichment, behavioral analysis, and presentation of the results. Data were collected from The Pirate Bay and UDP trackers, yielding a dataset of more than 60,000 unique IP addresses across 206 popular torrents. The data were enriched with geolocation, anonymization status, and flags of involvement in child exploitation material (CEM). A case study on sensitive e-books shows how such data can help detect possible interest in illicit content. Network analysis highlights peer clustering, co-download patterns, and the use of privacy tools by suspicious users. The study shows that publicly available torrent metadata can support scalable and automated OSINT profiling. This work adds to digital forensics by proposing a new method to extract useful signals from noisy data, with applications in law enforcement, cybersecurity, and threat analysis.
Illicit Darkweb Classification via Natural-language Processing: Classifying Illicit Content of Webpages based on Textual Information
Dec 08, 2023Abstract:This work aims at expanding previous works done in the context of illegal activities classification, performing three different steps. First, we created a heterogeneous dataset of 113995 onion sites and dark marketplaces. Then, we compared pre-trained transferable models, i.e., ULMFit (Universal Language Model Fine-tuning), Bert (Bidirectional Encoder Representations from Transformers), and RoBERTa (Robustly optimized BERT approach) with a traditional text classification approach like LSTM (Long short-term memory) neural networks. Finally, we developed two illegal activities classification approaches, one for illicit content on the Dark Web and one for identifying the specific types of drugs. Results show that Bert obtained the best approach, classifying the dark web's general content and the types of Drugs with 96.08% and 91.98% of accuracy.
Internet-of-Things Architectures for Secure Cyber-Physical Spaces: the VISOR Experience Report
Apr 01, 2022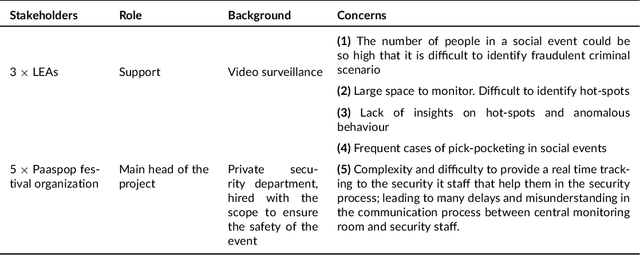
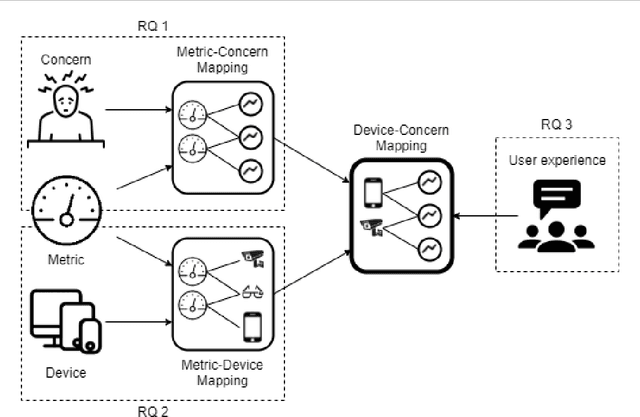


Abstract:Internet of things (IoT) technologies are becoming a more and more widespread part of civilian life in common urban spaces, which are rapidly turning into cyber-physical spaces. Simultaneously, the fear of terrorism and crime in such public spaces is ever-increasing. Due to the resulting increased demand for security, video-based IoT surveillance systems have become an important area for research. Considering the large number of devices involved in the illicit recognition task, we conducted a field study in a Dutch Easter music festival in a national interest project called VISOR to select the most appropriate device configuration in terms of performance and results. We iteratively architected solutions for the security of cyber-physical spaces using IoT devices. We tested the performance of multiple federated devices encompassing drones, closed-circuit television, smart phone cameras, and smart glasses to detect real-case scenarios of potentially malicious activities such as mosh-pits and pick-pocketing. Our results pave the way to select optimal IoT architecture configurations -- i.e., a mix of CCTV, drones, smart glasses, and camera phones in our case -- to make safer cyber-physical spaces' a reality.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge