G. Sahoo
A New Clustering Approach for Anomaly Intrusion Detection
Apr 10, 2014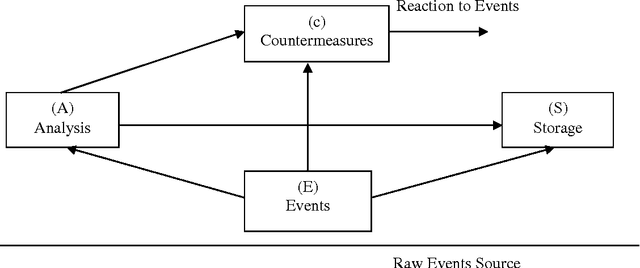
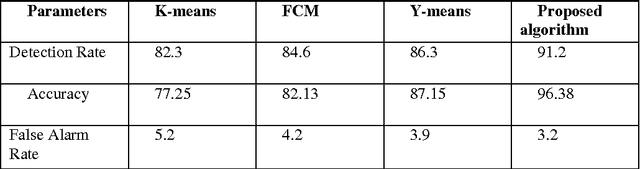
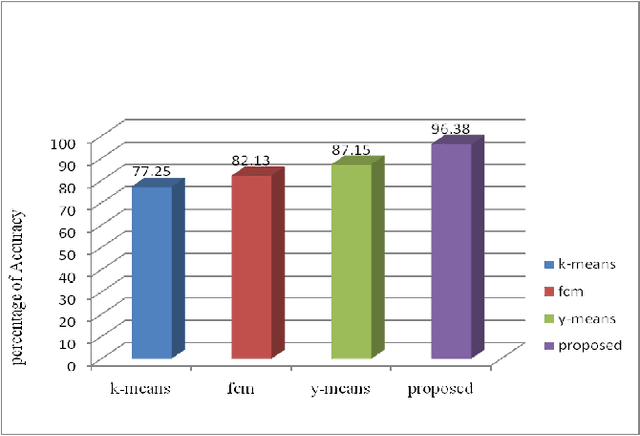
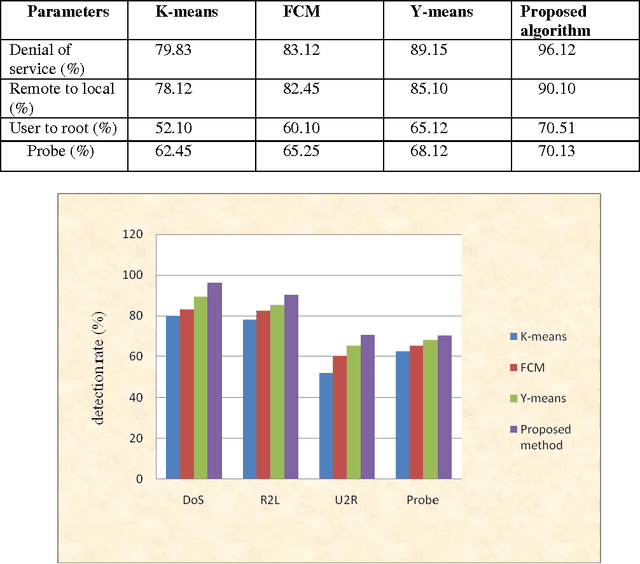
Abstract:Recent advances in technology have made our work easier compare to earlier times. Computer network is growing day by day but while discussing about the security of computers and networks it has always been a major concerns for organizations varying from smaller to larger enterprises. It is true that organizations are aware of the possible threats and attacks so they always prepare for the safer side but due to some loopholes attackers are able to make attacks. Intrusion detection is one of the major fields of research and researchers are trying to find new algorithms for detecting intrusions. Clustering techniques of data mining is an interested area of research for detecting possible intrusions and attacks. This paper presents a new clustering approach for anomaly intrusion detection by using the approach of K-medoids method of clustering and its certain modifications. The proposed algorithm is able to achieve high detection rate and overcomes the disadvantages of K-means algorithm.
* 10 pages with 3 figures,2 Tables This paper explains about clustering methodology used in Data Mining field for Intrusion Detection in the area of Network Security
An Unmanned Aerial Vehicle as Human-Assistant Robotics System
Apr 19, 2011



Abstract:According to the American Heritage Dictionary [1],Robotics is the science or study of the technology associated with the design, fabrication, theory, and application of Robots. The term Hoverbot is also often used to refer to sophisticated mechanical devices that are remotely controlled by human beings even though these devices are not autonomous. This paper describes a remotely controlled hoverbot by installing a transmitter and receiver on both sides that is the control computer (PC) and the hoverbot respectively. Data is transmitted as signal or instruction via a infrastructure network which is converted into a command for the hoverbot that operates at a remote site.
An Artificial Immune System Model for Multi-Agents Resource Sharing in Distributed Environments
Feb 24, 2011



Abstract:Natural Immune system plays a vital role in the survival of the all living being. It provides a mechanism to defend itself from external predates making it consistent systems, capable of adapting itself for survival incase of changes. The human immune system has motivated scientists and engineers for finding powerful information processing algorithms that has solved complex engineering tasks. This paper explores one of the various possibilities for solving problem in a Multiagent scenario wherein multiple robots are deployed to achieve a goal collectively. The final goal is dependent on the performance of individual robot and its survival without having to lose its energy beyond a predetermined threshold value by deploying an evolutionary computational technique otherwise called the artificial immune system that imitates the biological immune system.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge