Chunmei Liu
AdapShare: An RL-Based Dynamic Spectrum Sharing Solution for O-RAN
Aug 29, 2024Abstract:The Open Radio Access Network (O-RAN) initiative, characterized by open interfaces and AI/ML-capable RAN Intelligent Controller (RIC), facilitates effective spectrum sharing among RANs. In this context, we introduce AdapShare, an ORAN-compatible solution leveraging Reinforcement Learning (RL) for intent-based spectrum management, with the primary goal of minimizing resource surpluses or deficits in RANs. By employing RL agents, AdapShare intelligently learns network demand patterns and uses them to allocate resources. We demonstrate the efficacy of AdapShare in the spectrum sharing scenario between LTE and NR networks, incorporating real-world LTE resource usage data and synthetic NR usage data to demonstrate its practical use. We use the average surplus or deficit and fairness index to measure the system's performance in various scenarios. AdapShare outperforms a quasi-static resource allocation scheme based on long-term network demand statistics, particularly when available resources are scarce or exceed the aggregate demand from the networks. Lastly, we present a high-level O-RAN compatible architecture using RL agents, which demonstrates the seamless integration of AdapShare into real-world deployment scenarios.
ProSAS: An O-RAN Approach to Spectrum Sharing between NR and LTE
Apr 14, 2024



Abstract:The Open Radio Access Network (O-RAN), an industry-driven initiative, utilizes intelligent Radio Access Network (RAN) controllers and open interfaces to facilitate efficient spectrum sharing between LTE and NR RANs. In this paper, we introduce the Proactive Spectrum Adaptation Scheme (ProSAS), a data-driven, O-RAN-compatible spectrum sharing solution. ProSAS is an intelligent radio resource demand prediction and management scheme for intent-driven spectrum management that minimizes surplus or deficit experienced by both RANs. We illustrate the effectiveness of this solution using real-world LTE resource usage data and synthetically generated NR data. Lastly, we discuss a high-level O-RAN-compatible architecture of the proposed solution.
5G NR-LTE Coexistence: Opportunities, Challenges, and Solutions
Oct 11, 2022



Abstract:5G New Radio (NR) promises to support diverse services such as enhanced mobile broadband (eMBB), ultra-reliable low-latency communication (URLLC), and massive machine-type communication (mMTC). This requires spectrum, most of which is occupied by 4G Long Term Evolution (LTE). Hence, network operators are expected to deploy 5G using the existing LTE infrastructure while migrating to NR. In addition, operators must support legacy LTE devices during the migration, so LTE and NR systems will coexist for the foreseeable future. In this article, we address LTE-NR coexistence starting with a review of both radio access technologies. We then describe the contributions by the 3rd Generation Partnership Project (3GPP) to solving the coexistence issue and catalog the major coexistence scenarios. Lastly, we introduce a novel spectrum sharing scheme that can be applied to the coexistence scenarios under study.
Resilient Machine Learning for Networked Cyber Physical Systems: A Survey for Machine Learning Security to Securing Machine Learning for CPS
Feb 14, 2021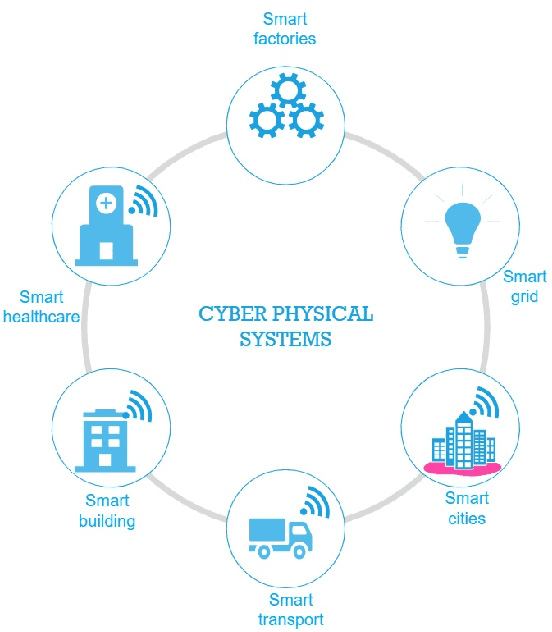
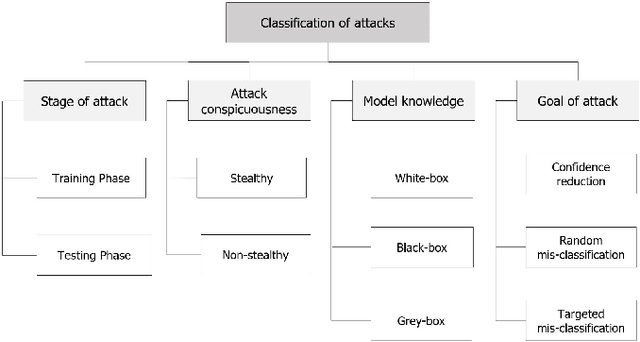
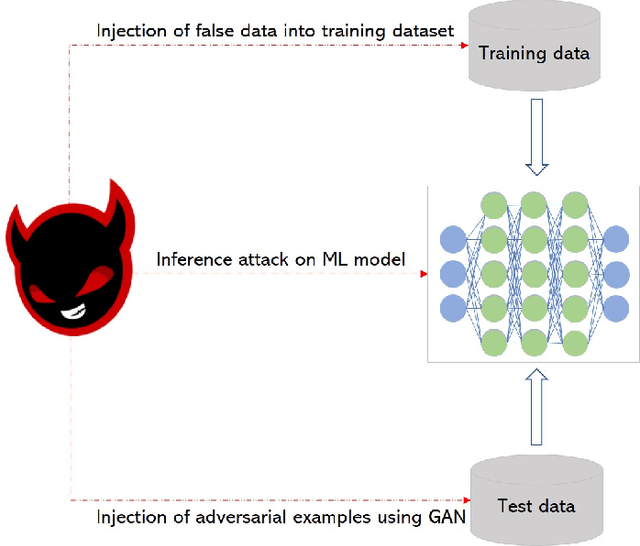
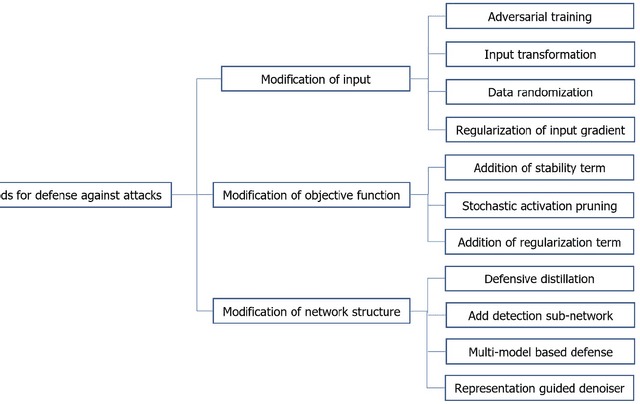
Abstract:Cyber Physical Systems (CPS) are characterized by their ability to integrate the physical and information or cyber worlds. Their deployment in critical infrastructure have demonstrated a potential to transform the world. However, harnessing this potential is limited by their critical nature and the far reaching effects of cyber attacks on human, infrastructure and the environment. An attraction for cyber concerns in CPS rises from the process of sending information from sensors to actuators over the wireless communication medium, thereby widening the attack surface. Traditionally, CPS security has been investigated from the perspective of preventing intruders from gaining access to the system using cryptography and other access control techniques. Most research work have therefore focused on the detection of attacks in CPS. However, in a world of increasing adversaries, it is becoming more difficult to totally prevent CPS from adversarial attacks, hence the need to focus on making CPS resilient. Resilient CPS are designed to withstand disruptions and remain functional despite the operation of adversaries. One of the dominant methodologies explored for building resilient CPS is dependent on machine learning (ML) algorithms. However, rising from recent research in adversarial ML, we posit that ML algorithms for securing CPS must themselves be resilient. This paper is therefore aimed at comprehensively surveying the interactions between resilient CPS using ML and resilient ML when applied in CPS. The paper concludes with a number of research trends and promising future research directions. Furthermore, with this paper, readers can have a thorough understanding of recent advances on ML-based security and securing ML for CPS and countermeasures, as well as research trends in this active research area.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge