A. S. M. Badrudduza
Enhancing Physical Layer Security in IoT-Based RF-FSO Integrated Networks: Multi-RIS Structures and their Impact on Secure Communication
Sep 18, 2025Abstract:Due to their ability to dynamically control the propagation environment, reconfigurable intelligent surfaces (RISs) offer a promising solution to address the challenges of $6$G wireless communication, especially in the context of Internet of Things (IoT) networks. This paper investigates a mixed communication model with multi-RIS-aided radio frequency (RF)-free space optics (FSO) to enhance the performance of IoT applications in complex environments. An eavesdropper is assumed to be present, attempting to intercept confidential information transmitted over the RF link. All RF links are modeled using Rician fading, while the FSO link accounts for M\'alaga turbulence with pointing errors, capturing real-world propagation conditions. Closed-form analytical expressions are derived for the secrecy outage probability, average secrecy capacity, and effective secrecy throughput in terms of Meijer's G function. To gain further insight, high signal-to-noise approximations of these metrics are also presented. Numerical results highlight the importance of heterodyne detection in mitigating the adverse effects of pointing errors on the FSO link. Moreover, integrating a multi-RIS structure into the proposed model significantly increases secrecy performance, achieving up to a $47.67\%$ improvement in SOP compared to conventional methods. Finally, the derived analytical results are validated through Monte Carlo simulations.
RIS-Aided Free-Space Optics Communications in A2G Networks over Inverted Gamma-Gamma Turbulent Channels
Aug 12, 2024Abstract:With the advent of sixth-generation networks, reconfigurable intelligent surfaces (RISs) have revolutionized wireless communications through dynamic electromagnetic wave manipulation, thereby facilitating the adaptability and unparalleled control of real-time performance evaluations. This study proposed a framework to analyze the performance of RIS-assisted free-space optics (FSO) communication over doubly inverted Gamma-Gamma (IGGG) distributions with pointing error impairments. Furthermore, a special scenario addressing secure communication in the potential presence of an eavesdropper. Consequently, we derived closed-form expressions for the outage probability, average bit error rate, average channel capacity, average secrecy capacity, and secrecy outage probability by employing an asymptotic analysis to provide deeper insights into the influence of various system parameters. Finally, we verified our analytical results through appropriate numerical simulations.
Secrecy Performance Analysis of Integrated RF-UWOC IoT Networks Enabled by UAV and Underwater-RIS
Jul 26, 2024Abstract:In the sixth-generation (6G) Internet of Things (IoT) networks, the use of UAV-mounted base stations and reconfigurable intelligent surfaces (RIS) has been considered to enhance coverage, flexibility, and security in non-terrestrial networks (NTNs). In addition to aerial networks enabled by NTN technologies, the integration of underwater networks with 6G IoT can be considered one of the most innovative challenges in future IoT. Along with such trends in IoT, this study investigates the secrecy performance of IoT networks that integrate radio frequency (RF) UAV-based NTNs and underwater optical wireless communication (UOWC) links with an RIS. Considering three potential eavesdropping scenarios (RF signal, UOWC signal, and both), we derive closed-form expressions for secrecy performance metrics, including average secrecy capacity, secrecy outage probability, probability of strictly positive secrecy capacity, and effective secrecy throughput. Extensive numerical analyses and Monte Carlo simulations elucidate the impact of system parameters such as fading severity, the number of RIS reflecting elements, underwater turbulence, pointing errors, and detection techniques on system security. The findings offer comprehensive design guidelines for developing such a network aiming to enhance secrecy performance and ensure secure communication in diverse and challenging environments.
RIS-aided Mixed RF-FSO Wireless Networks: Secrecy Performance Analysis with Simultaneous Eavesdropping
Apr 09, 2023



Abstract:The appearance of sixth-generation networks has resulted in the proposal of several solutions to tackle signal loss. One of these solutions is the utilization of reconfigurable intelligent surfaces (RIS), which can reflect or refract signals as required. This integration offers significant potential to improve the coverage area from the sender to the receiver. In this paper, we present a comprehensive framework for analyzing the secrecy performance of a RIS-aided mixed radio frequency (RF)-free space optics (FSO) system, for the first time. Our study assumes that a secure message is transmitted from a RF transmitter to a FSO receiver through an intermediate relay. The RF link experiences Rician fading while the FSO link experiences M\'alaga distributed turbulence with pointing errors. We examine three scenarios: 1) RF-link eavesdropping, 2) FSO-link eavesdropping, and 3) a simultaneous eavesdropping attack on both RF and FSO links. We evaluate the secrecy performance using analytical expressions to compute secrecy metrics such as the average secrecy capacity, secrecy outage probability, strictly positive secrecy capacity, effective secrecy throughput, and intercept probability. Our results are confirmed via Monte-Carlo simulations and demonstrate that fading parameters, atmospheric turbulence conditions, pointing errors, and detection techniques play a crucial role in enhancing secrecy performance.
Secrecy Outage Analysis of Energy Harvesting Relay-based Mixed UOWC-RF Network with Multiple Eavesdroppers
Feb 20, 2023Abstract:This work deals with the physical layer security performance of a dual-hop underwater optical communication (UOWC)-radio frequency (RF) network under the intruding attempts of multiple eavesdroppers via RF links. The intermediate decode and forward relay node between the underwater source and the destination transforms the optical signal into electrical form and re-transmits it to the destination node with the help of harvested energy by the relay from an integrated power beacon within the system. The source-to-relay link (UOWC) follows a mixture exponential generalized Gamma turbulence with pointing error impairments whereas all the remaining links (RF) undergo $\kappa-\mu$ shadowed fading. With regards to the types of intruders, herein two scenarios are considered, i.e., colluding (\textit{Scenario-I}) and non-colluding (\textit{Scenario-II}) eavesdroppers and the analytical expressions of secure outage probability, probability of strictly positive secrecy capacity, and effective secrecy throughput are derived in closed form for each scenario. Furthermore, the impacts of UOWC and RF channel parameters as well as detection techniques on secrecy capacity are demonstrated, and following this a comparison between the two considered scenarios is demonstrated that reveals the collusion between the eavesdroppers imposes the most harmful threat on secrecy throughput but a better secrecy level can be attained adopting diversity at the destination and power beacon nodes along with heterodyne detection rather than intensity modulation and direct detection technique. Finally, all the derived expressions are corroborated via Monte Carlo simulations.
On Effective Secrecy Throughput of Underlay Spectrum Sharing $α$-$μ$/ Málaga Hybrid Model under Interference-and-Transmit Power Constraints
Nov 12, 2021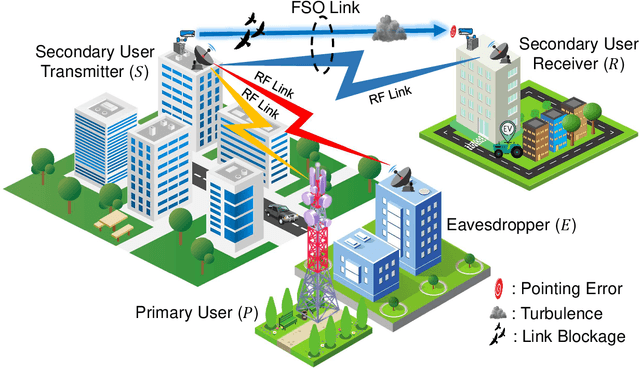
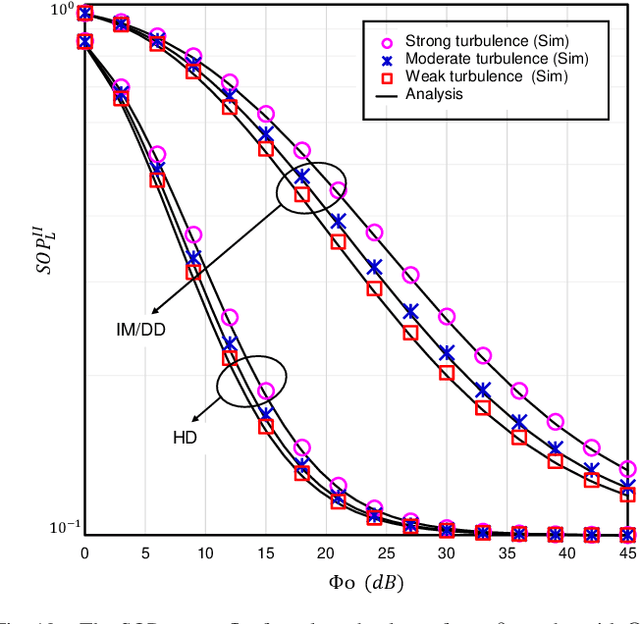
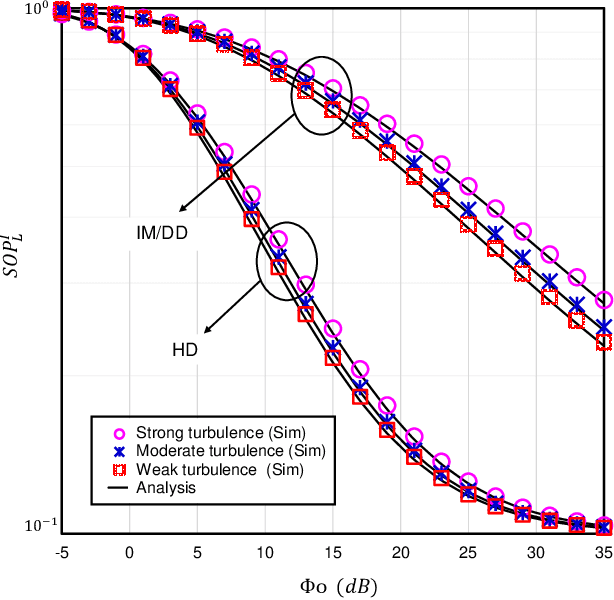
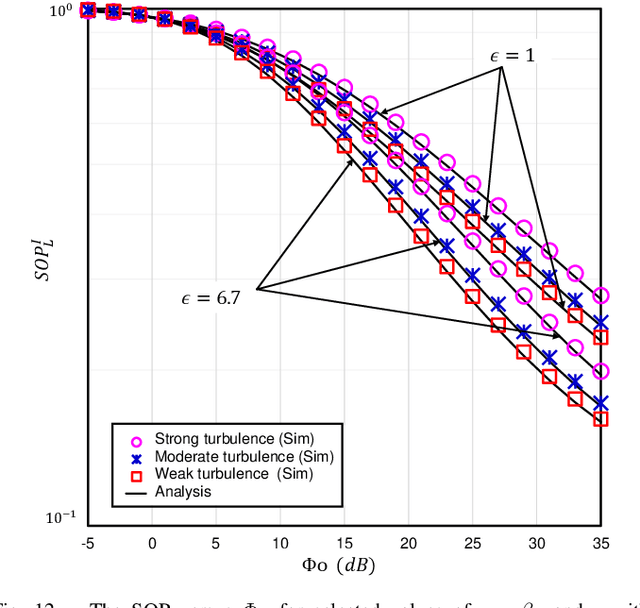
Abstract:The underlay cognitive radio-based hybrid radio frequency / free-space optical (RF / FSO) systems have been emerged as a promising technology due to its ability to eliminate spectrum scarcity and spectrum under-utilization problems. Consequently, this work analyzes the physical layer security aspects of a cognitive RF / FSO hybrid network that includes a primary user, a secondary source, a secondary receiver, and an eavesdropper where the secret communication takes place between two legitimate secondary peers over the RF and FSO links simultaneously, and the eavesdropper can overhear the RF link only. In particular, the maximum transmit power limitation at the secondary user as well as the permissible interference power restriction at the primary user are also taken into consideration. All the RF links are modeled with $\alpha$-$\mu$ fading whereas the FSO link undergoes M\'alaga (M) turbulence with link blockage and pointing error impairments. At the receiver, the selection combining diversity technique is utilized to select the signal with the best electrical signal-to-ratio (SNR). Moreover, the closed-form expressions for the secrecy outage probability, probability of strictly positive secrecy capacity, and effective secrecy throughput are derived to analyze the secrecy performance. Besides, the impacts of fading, primary-secondary interference, detection techniques, link blockage probability, atmospheric turbulence, and pointing error are examined. Finally, Monte-Carlo simulations are performed to corroborate the derived expressions.
On the Intercept Probability and Secure Outage Analysis of Mixed ($α$-$κ$-$μ$)-shadowed and Málaga Turbulent Model
Sep 11, 2021



Abstract:This work deals with the secrecy performance analysis of a dual-hop RF-FSO DF relaying network composed of a source, a relay, a destination, and an eavesdropper. We assume the eavesdropper is located close to the destination and overhears the relay's transmitted optical signal. The RF and FSO links undergo ($\alpha$-$\kappa$-$\mu$)-shadowed fading and unified M\'alaga turbulence with pointing error. The secrecy performance of the mixed system is studied by deriving closed-form analytical expressions of secure outage probability (SOP), strictly positive secrecy capacity (SPSC), and intercept probability (IP). Besides, we also derive the asymptotic SOP, SPSC, and IP upon utilizing the unfolding of Meijer's G function where the electrical SNR of the FSO link tends to infinity. Finally, the Monte-Carlo simulation is performed to corroborate the analytical expressions. Our results illustrate that fading, shadowing, detection techniques (i.e., heterodyne detection (HD) and intensity modulation and direct detection (IM/DD)), atmospheric turbulence, and pointing error significantly affect the secrecy performance. In addition, better performance is obtained exploiting the HD technique at the destination relative to IM/DD technique.
Effects of Eavesdropper on the Performance of Mixed η-μ and DGG Cooperative Relaying System
Jun 13, 2021



Abstract:Free-space optical (FSO) channel offers line-of-sight wireless communication with high data rates and high secrecy utilizing unlicensed optical spectrum and also paves the way to the solution of the last-mile access problem. Since atmospheric turbulence is a hindrance to an enhanced secrecy performance, the mixed radio frequency (RF)-FSO system is gaining enormous research interest in recent days. But conventional FSO models except for the double generalized Gamma (DGG) model can not demonstrate secrecy performance for all ranges of turbulence severity. This reason has led us to propose a dual-hop eta-mu and unified DGG mixed RF-FSO network while considering eavesdropping at both RF and FSO hops. The security of these proposed scenarios is investigated in terms of two metrics, i.e., strictly positive secrecy capacity and secure outage probability. Exploiting these expressions, we further investigate how the secrecy performance is affected by various system parameters, i.e., fading, turbulence, and pointing errors. A demonstration is made between heterodyne detection (HD) and intensity modulation and direct detection (IM/DD) techniques while exhibiting superior secrecy performance for HD technique over IM/DD technique. Finally, all analytical results are corroborated via Monte-Carlo simulations.
On Secrecy Performance of Mixed α-η-μ and Malaga RF-FSO Variable Gain Relaying Channel
May 26, 2021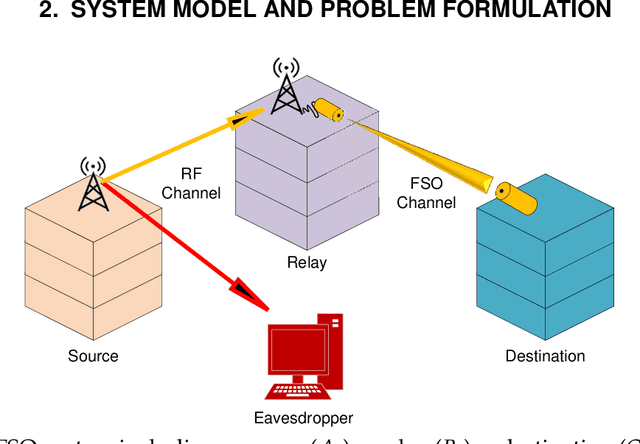
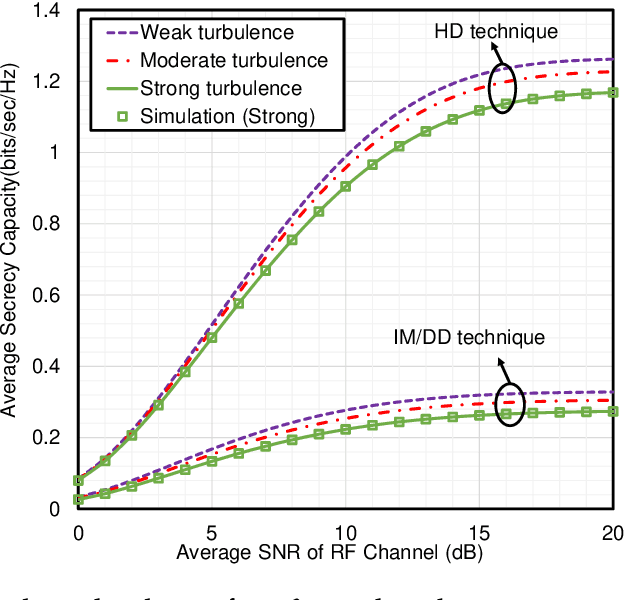
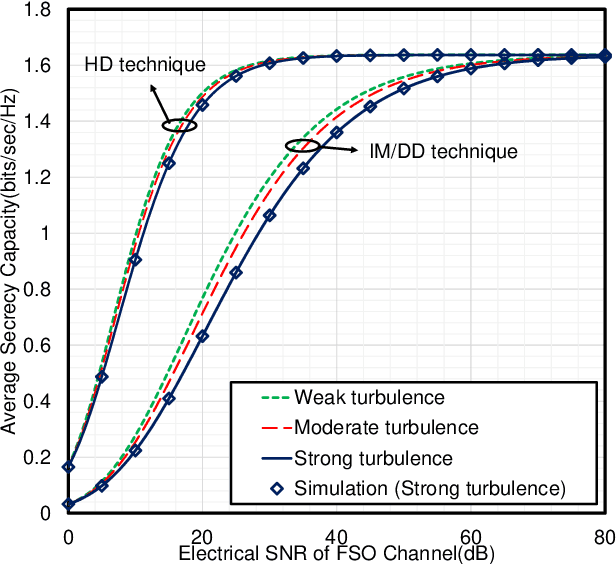
Abstract:With the completion of standardization of fifth-generation (5G) networks, the researchers have begun visioning sixth-generation (6G) networks that are predicted to be human-centric. Hence, similar to 5G networks, besides high data rate, providing secrecy and privacy will be the center of attention by the wireless research community. To support the visions beyond 5G (B5G) and 6G, in this paper we propose a secure radio frequency (RF)-free-space optical (FSO) mixed framework under the attempt of wiretapping by an eavesdropper at the RF hop. We assume the RF links undergo alpha-eta-mu fading whereas the FSO link exhibits a unified Malaga turbulence model with pointing error. The secrecy performance is evaluated by deducing expressions for three secrecy metrics i.e. average secrecy capacity, secure outage probability, and probability of non-zero secrecy capacity in terms of univariate and bivariate Meijer's G and Fox's H functions. We further capitalize on these expressions to demonstrate the impacts of fading, atmospheric turbulence, and pointing errors and show a comparison between two detection techniques (i.e. heterodyne detection (HD) and intensity modulation with direct detection (IM/DD)) that clearly reveals better secrecy can be achieved with HD technique relative to the IM/DD method. The inclusion of generalized fading models at the RF and FSO hops offers unification of several classical scenarios as special cases thereby exhibiting a more generic nature relative to the existing literature. Finally, all the analytical results are corroborated via Monte-Carlo simulations.
Enhancing Security of TAS/MRC Based Mixed RF-UOWC System with Induced Underwater Turbulence Effect
May 19, 2021
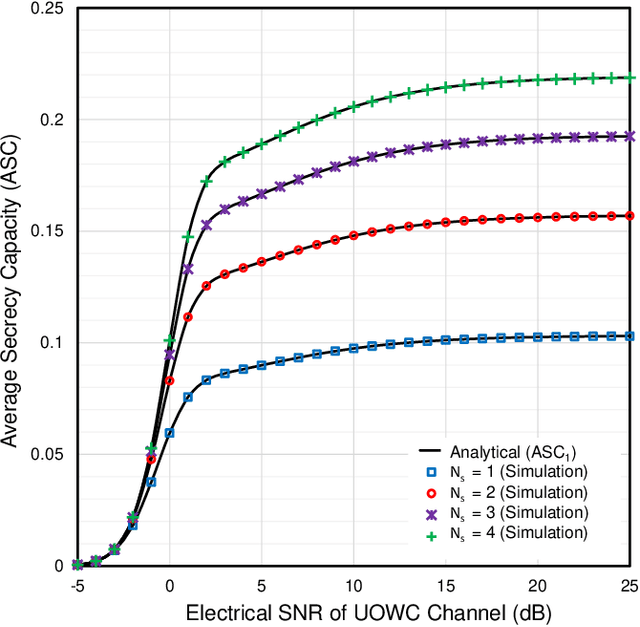
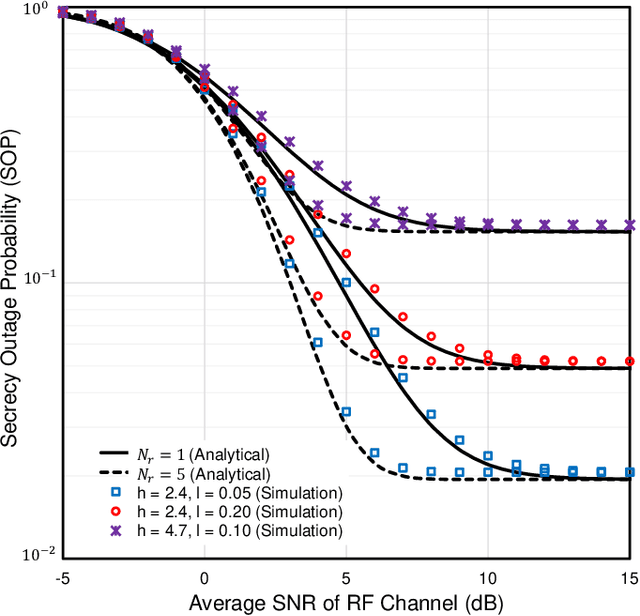
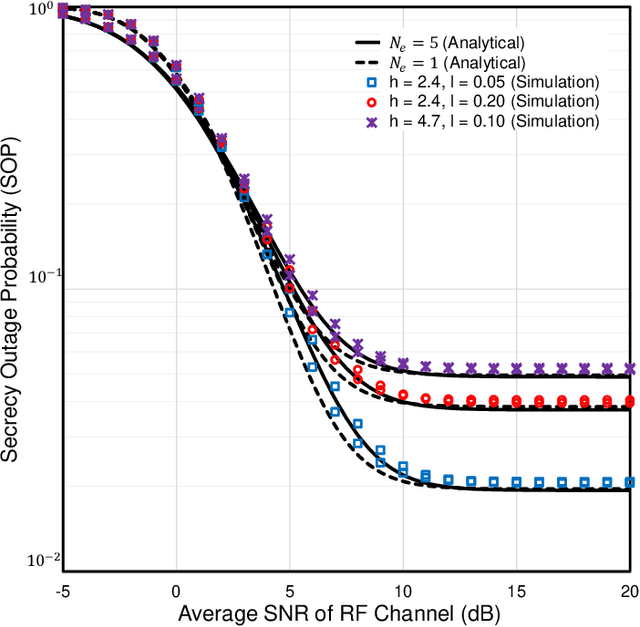
Abstract:Post commercial deployment of fifth-generation (5G) technologies, the consideration of sixth-generation (6G) networks is drawing remarkable attention from research communities. Researchers suggest that similar to 5G, 6G technology must be human-centric where high secrecy together with high data rate will be the key features. These challenges can be easily overcome utilizing PHY security techniques over high-frequency free-space or underwater optical wireless communication (UOWC) technologies. But in long-distance communication, turbulence components drastically affect the optical signals, leading to the invention of the combination of radio-frequency (RF) links with optical links. This work deals with the secrecy performance analysis of a mixed RF-UOWC system where an eavesdropper tries to intercept RF communications. RF and optical links undergo $\eta-\mu$ and mixture exponential generalized Gamma distributions, respectively. To keep pace with the high data rate of optical technologies, we exploit the antenna selection scheme at the source and maximal ratio combining diversity at the relay and eavesdropper, while the eavesdropper is unaware of the antenna selection scheme. We derive closed-form expressions of average secrecy capacity, secrecy outage probability, and strictly positive secrecy capacity to demonstrate the impacts of the system parameters on the secrecy behavior. Finally, the expressions are corroborated via Monte-Carlo simulations.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge