Analyzing and Improving Performance of a Class of Anomaly-based Intrusion Detectors
Paper and Code
Oct 26, 2004
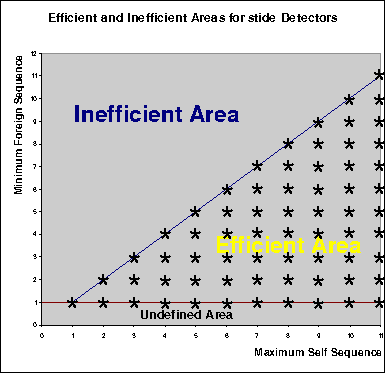
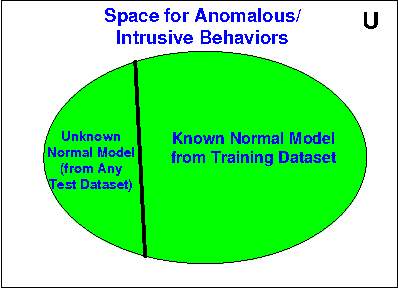
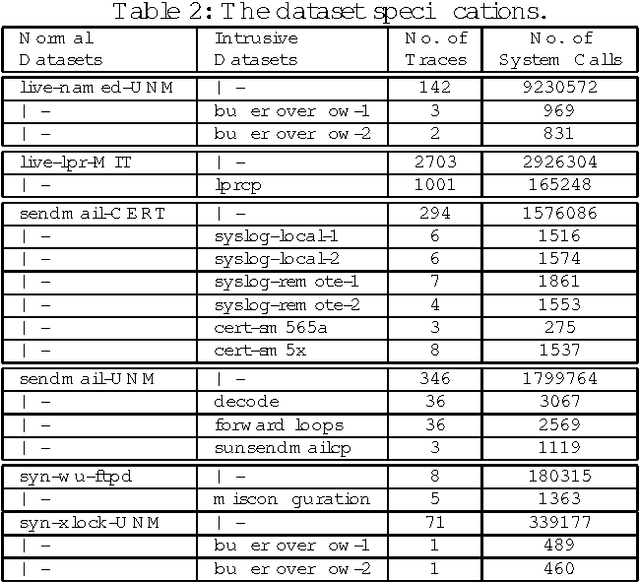
Anomaly-based intrusion detection (AID) techniques are useful for detecting novel intrusions into computing resources. One of the most successful AID detectors proposed to date is stide, which is based on analysis of system call sequences. In this paper, we present a detailed formal framework to analyze, understand and improve the performance of stide and similar AID techniques. Several important properties of stide-like detectors are established through formal proofs, and validated by carefully conducted experiments using test datasets. Finally, the framework is utilized to design two applications to improve the cost and performance of stide-like detectors which are based on sequence analysis. The first application reduces the cost of developing AID detectors by identifying the critical sections in the training dataset, and the second application identifies the intrusion context in the intrusive dataset, that helps to fine-tune the detectors. Such fine-tuning in turn helps to improve detection rate and reduce false alarm rate, thereby increasing the effectiveness and efficiency of the intrusion detectors.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge