Vittorio Orbinato
Automatic Mapping of Unstructured Cyber Threat Intelligence: An Experimental Study
Aug 25, 2022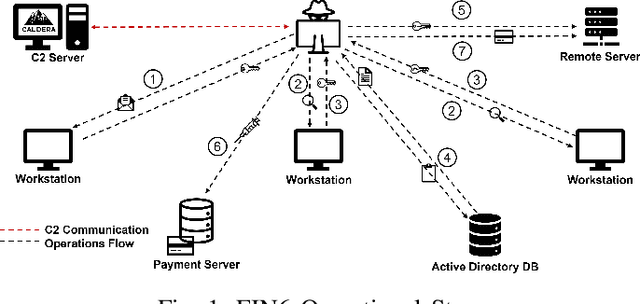
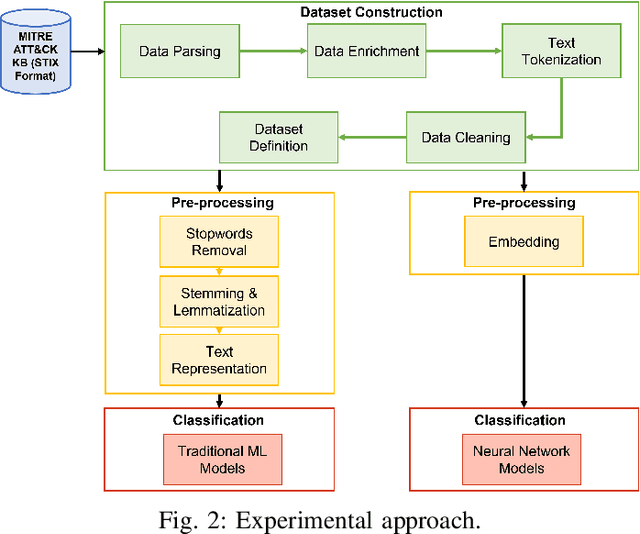
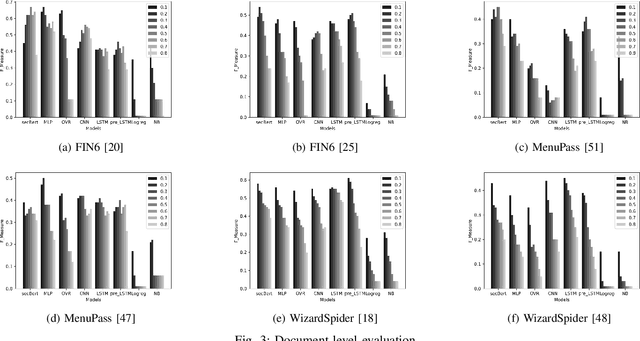

Abstract:Proactive approaches to security, such as adversary emulation, leverage information about threat actors and their techniques (Cyber Threat Intelligence, CTI). However, most CTI still comes in unstructured forms (i.e., natural language), such as incident reports and leaked documents. To support proactive security efforts, we present an experimental study on the automatic classification of unstructured CTI into attack techniques using machine learning (ML). We contribute with two new datasets for CTI analysis, and we evaluate several ML models, including both traditional and deep learning-based ones. We present several lessons learned about how ML can perform at this task, which classifiers perform best and under which conditions, which are the main causes of classification errors, and the challenges ahead for CTI analysis.
A next-generation platform for Cyber Range-as-a-Service
Dec 21, 2021
Abstract:In the last years, Cyber Ranges have become a widespread solution to train professionals for responding to cyber threats and attacks. Cloud computing plays a key role in this context since it enables the creation of virtual infrastructures on which Cyber Ranges are based. However, the setup and management of Cyber Ranges are expensive and time-consuming activities. In this paper, we highlight the novel features for the next-generation Cyber Range platforms. In particular, these features include the creation of a virtual clone for an actual corporate infrastructure, relieving the security managers from the setup of the training scenarios and sessions, the automatic monitoring of the participants' activities, and the emulation of their behavior.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge