Majid Ghaderi
Adaptive Anomaly Detection in Evolving Network Environments
Aug 20, 2025Abstract:Distribution shift, a change in the statistical properties of data over time, poses a critical challenge for deep learning anomaly detection systems. Existing anomaly detection systems often struggle to adapt to these shifts. Specifically, systems based on supervised learning require costly manual labeling, while those based on unsupervised learning rely on clean data, which is difficult to obtain, for shift adaptation. Both of these requirements are challenging to meet in practice. In this paper, we introduce NetSight, a framework for supervised anomaly detection in network data that continually detects and adapts to distribution shifts in an online manner. NetSight eliminates manual intervention through a novel pseudo-labeling technique and uses a knowledge distillation-based adaptation strategy to prevent catastrophic forgetting. Evaluated on three long-term network datasets, NetSight demonstrates superior adaptation performance compared to state-of-the-art methods that rely on manual labeling, achieving F1-score improvements of up to 11.72%. This proves its robustness and effectiveness in dynamic networks that experience distribution shifts over time.
Optimal Routing and Link Configuration for Covert Heterogeneous Wireless Networks
Dec 09, 2024



Abstract:Nodes in contemporary radio networks often have multiple interfaces available for communication: WiFi, cellular, LoRa, Zigbee, etc. This motivates understanding both link and network configuration when multiple communication modalities with vastly different capabilities are available to each node. In conjunction, covertness or the hiding of radio communications is often a significant concern in both commercial and military wireless networks. We consider the optimal routing problem in wireless networks when nodes have multiple interfaces available and intend to hide the presence of the transmission from attentive and capable adversaries. We first consider the maximization of the route capacity given an end-to-end covertness constraint against a single adversary and we find a polynomial-time algorithm for optimal route selection and link configuration. We further provide optimal polynomial-time algorithms for two important extensions: (i) statistical uncertainty during optimization about the channel state information for channels from system nodes to the adversary; and, (ii) maintaining covertness against multiple adversaries. Numerical results are included to demonstrate the gains of employing heterogeneous radio resources and to compare the performance of the proposed approach versus alternatives.
DeepFlow: Abnormal Traffic Flow Detection Using Siamese Networks
Aug 26, 2021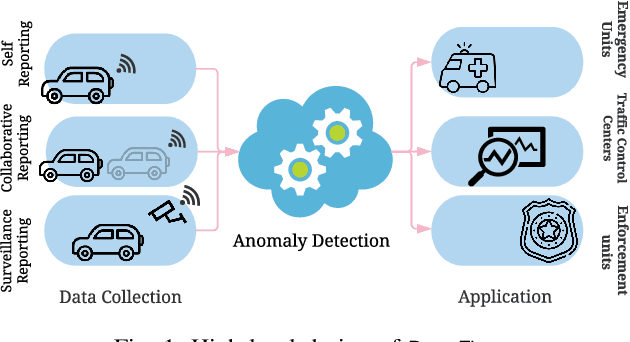
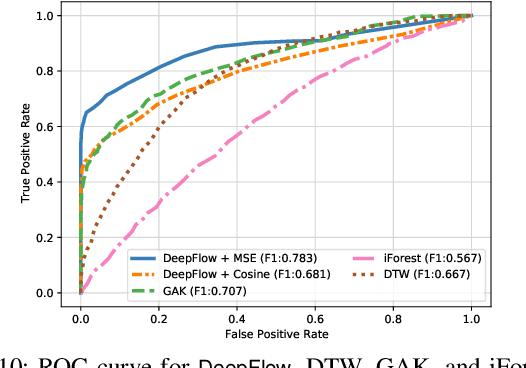
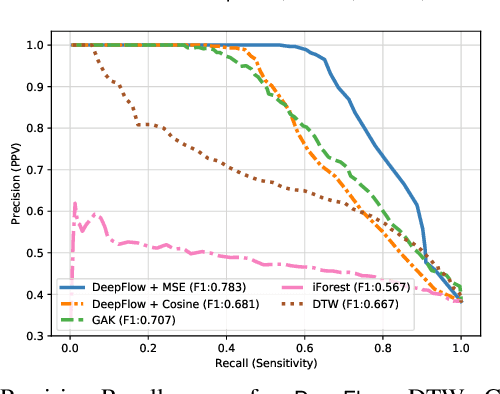
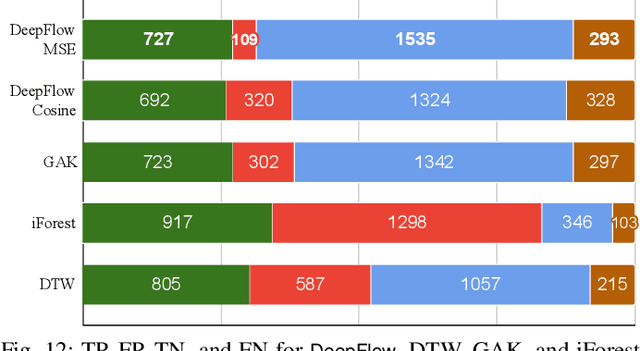
Abstract:Nowadays, many cities are equipped with surveillance systems and traffic control centers to monitor vehicular traffic for road safety and efficiency. The monitoring process is mostly done manually which is inefficient and expensive. In recent years, several data-driven solutions have been proposed in the literature to automatically analyze traffic flow data using machine learning techniques. However, existing solutions require large and comprehensive datasets for training which are not readily available, thus limiting their application. In this paper, we develop a traffic anomaly detection system, referred to as DeepFlow, based on Siamese neural networks, which are suitable in scenarios where only small datasets are available for training. Our model can detect abnormal traffic flows by analyzing the trajectory data collected from the vehicles in a fleet. To evaluate DeepFlow, we use realistic vehicular traffic simulations in SUMO. Our results show that DeepFlow detects abnormal traffic patterns with an F1 score of 78%, while outperforming other existing approaches including: Dynamic Time Warping (DTW), Global Alignment Kernels (GAK), and iForest.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge