Karim Ouazzane
A Novel Reinforcement Learning Model for Post-Incident Malware Investigations
Oct 19, 2024



Abstract:This Research proposes a Novel Reinforcement Learning (RL) model to optimise malware forensics investigation during cyber incident response. It aims to improve forensic investigation efficiency by reducing false negatives and adapting current practices to evolving malware signatures. The proposed RL framework leverages techniques such as Q-learning and the Markov Decision Process (MDP) to train the system to identify malware patterns in live memory dumps, thereby automating forensic tasks. The RL model is based on a detailed malware workflow diagram that guides the analysis of malware artefacts using static and behavioural techniques as well as machine learning algorithms. Furthermore, it seeks to address challenges in the UK justice system by ensuring the accuracy of forensic evidence. We conduct testing and evaluation in controlled environments, using datasets created with Windows operating systems to simulate malware infections. The experimental results demonstrate that RL improves malware detection rates compared to conventional methods, with the RL model's performance varying depending on the complexity and learning rate of the environment. The study concludes that while RL offers promising potential for automating malware forensics, its efficacy across diverse malware types requires ongoing refinement of reward systems and feature extraction methods.
* 8 pages. arXiv admin note: substantial text overlap with arXiv:2408.01999
Reinforcement Learning for an Efficient and Effective Malware Investigation during Cyber Incident Response
Aug 04, 2024Abstract:This research focused on enhancing post-incident malware forensic investigation using reinforcement learning RL. We proposed an advanced MDP post incident malware forensics investigation model and framework to expedite post incident forensics. We then implement our RL Malware Investigation Model based on structured MDP within the proposed framework. To identify malware artefacts, the RL agent acquires and examines forensics evidence files, iteratively improving its capabilities using Q Table and temporal difference learning. The Q learning algorithm significantly improved the agent ability to identify malware. An epsilon greedy exploration strategy and Q learning updates enabled efficient learning and decision making. Our experimental testing revealed that optimal learning rates depend on the MDP environment complexity, with simpler environments benefiting from higher rates for quicker convergence and complex ones requiring lower rates for stability. Our model performance in identifying and classifying malware reduced malware analysis time compared to human experts, demonstrating robustness and adaptability. The study highlighted the significance of hyper parameter tuning and suggested adaptive strategies for complex environments. Our RL based approach produced promising results and is validated as an alternative to traditional methods notably by offering continuous learning and adaptation to new and evolving malware threats which ultimately enhance the post incident forensics investigations.
A Comprehensive Analysis of the Role of Artificial Intelligence and Machine Learning in Modern Digital Forensics and Incident Response
Sep 13, 2023Abstract:In the dynamic landscape of digital forensics, the integration of Artificial Intelligence (AI) and Machine Learning (ML) stands as a transformative technology, poised to amplify the efficiency and precision of digital forensics investigations. However, the use of ML and AI in digital forensics is still in its nascent stages. As a result, this paper gives a thorough and in-depth analysis that goes beyond a simple survey and review. The goal is to look closely at how AI and ML techniques are used in digital forensics and incident response. This research explores cutting-edge research initiatives that cross domains such as data collection and recovery, the intricate reconstruction of cybercrime timelines, robust big data analysis, pattern recognition, safeguarding the chain of custody, and orchestrating responsive strategies to hacking incidents. This endeavour digs far beneath the surface to unearth the intricate ways AI-driven methodologies are shaping these crucial facets of digital forensics practice. While the promise of AI in digital forensics is evident, the challenges arising from increasing database sizes and evolving criminal tactics necessitate ongoing collaborative research and refinement within the digital forensics profession. This study examines the contributions, limitations, and gaps in the existing research, shedding light on the potential and limitations of AI and ML techniques. By exploring these different research areas, we highlight the critical need for strategic planning, continual research, and development to unlock AI's full potential in digital forensics and incident response. Ultimately, this paper underscores the significance of AI and ML integration in digital forensics, offering insights into their benefits, drawbacks, and broader implications for tackling modern cyber threats.
D2WFP: A Novel Protocol for Forensically Identifying, Extracting, and Analysing Deep and Dark Web Browsing Activities
Sep 11, 2023Abstract:The use of the un-indexed web, commonly known as the deep web and dark web, to commit or facilitate criminal activity has drastically increased over the past decade. The dark web is an in-famously dangerous place where all kinds of criminal activities take place [1-2], despite advances in web forensics techniques, tools, and methodologies, few studies have formally tackled the dark and deep web forensics and the technical differences in terms of investigative techniques and artefacts identification and extraction. This research proposes a novel and comprehensive protocol to guide and assist digital forensics professionals in investigating crimes committed on or via the deep and dark web, The protocol named D2WFP establishes a new sequential approach for performing investigative activities by observing the order of volatility and implementing a systemic approach covering all browsing related hives and artefacts which ultimately resulted into improv-ing the accuracy and effectiveness. Rigorous quantitative and qualitative research has been conducted by assessing D2WFP following a scientifically-sound and comprehensive process in different scenarios and the obtained results show an apparent increase in the number of artefacts re-covered when adopting D2WFP which outperform any current industry or opensource browsing forensics tools. The second contribution of D2WFP is the robust formulation of artefact correlation and cross-validation within D2WFP which enables digital forensics professionals to better document and structure their analysis of host-based deep and dark web browsing artefacts.
Multidimensional Cybersecurity Framework for Strategic Foresight
Feb 05, 2022
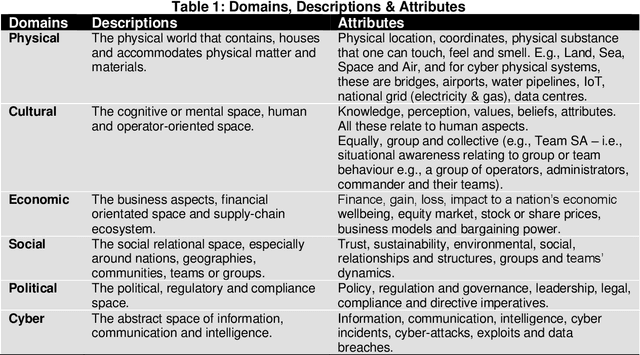


Abstract:Cybersecurity is now at the forefront of most organisational digital transformative agendas and National economic, social and political programmes. Hence its impact to society can no longer be seen to be one dimensional. The rise in National cybersecurity laws and regulations is a good indicator of its perceived importance to nations. And the recent awakening for social and ethical transparency in society and coupled with sustainability issues demonstrate the need for a paradigm shift in how cybersecurity discourses can now happen. In response to this shift, a multidimensional cybersecurity framework for strategic foresight underpinned on situational awareness is proposed. The conceptual cybersecurity framework comprising six domains such as Physical, Cultural, Economic, Social, Political and Cyber, is discussed. The guiding principles underpinning the framework are outlined, followed by in-depth reflection on the Business, Operational, Technological and Human (BOTH) factors and their implications for strategic foresight for cybersecurity.
* 31 pages, 7 figures
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge