Junhwan Lee
Rejection of Smooth GPS Time Synchronization Attacks via Sparse Techniques
Feb 28, 2021


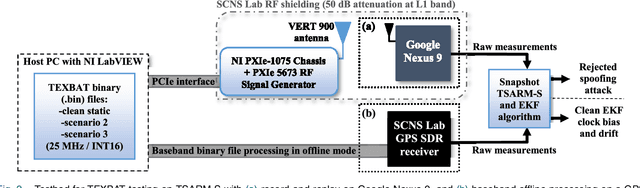
Abstract:This paper presents a novel time synchronization attack (TSA) model for the Global Positioning System (GPS) based on clock data behavior changes in a higher-order derivative domain. Further, the time synchronization attack rejection and mitigation based on sparse domain (TSARM-S) is presented. TSAs affect stationary GPS receivers in applications where precise timing is required, such as cellular communications, financial transactions, and monitoring of the electric power grid. In the present work, the clock bias and clock drift are monitored at higher-order clock data derivatives where the TSA is seen as a sparse spike-like event. The smoothness of the attack relates to the derivative order where the sparsity is observed. The proposed method jointly estimates a dynamic solution for GPS timing and rejects behavior changes based on such sparse events. An evaluation procedure is presented for two testbeds, namely a commercial receiver and a software-defined radio. Further, the proposed method is evaluated against distinct real-dataset Texas Spoofing Test Battery (TEXBAT) scenarios. Combined synthetic and real-data results show an average RMS clock bias error of 12.08 m for the SDR platform, and 45.74 m for the commercial device. Further, the technique is evaluated against state-of-the-art mitigation techniques and in a spoofing-plus-multipath scenario for robustness. Finally, TSARM-S can be potentially optimized and implemented in commercial devices via a firmware upgrade.
* IEEE Sensors Journal ( Volume: 21, Issue: 1, Jan.1, 1 2021)
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge