Daniel Reti
Evaluation of Reinforcement Learning for Autonomous Penetration Testing using A3C, Q-learning and DQN
Jul 22, 2024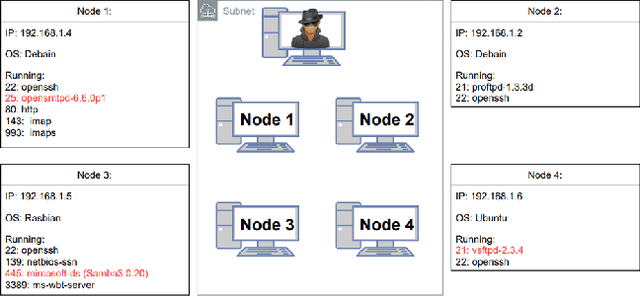
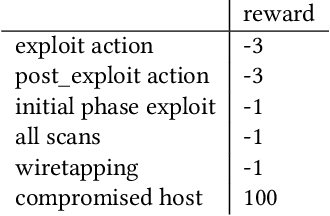
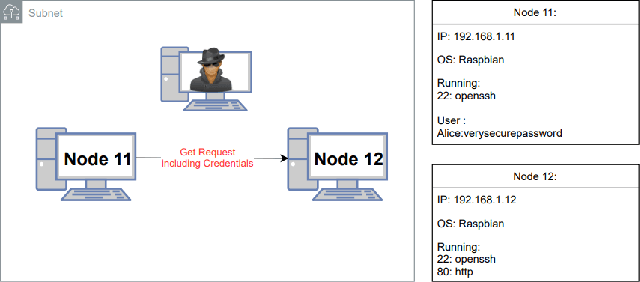
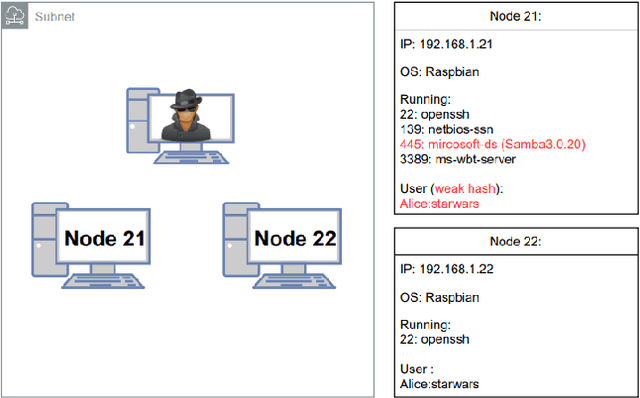
Abstract:Penetration testing is the process of searching for security weaknesses by simulating an attack. It is usually performed by experienced professionals, where scanning and attack tools are applied. By automating the execution of such tools, the need for human interaction and decision-making could be reduced. In this work, a Network Attack Simulator (NASim) was used as an environment to train reinforcement learning agents to solve three predefined security scenarios. These scenarios cover techniques of exploitation, post-exploitation and wiretapping. A large hyperparameter grid search was performed to find the best hyperparameter combinations. The algorithms Q-learning, DQN and A3C were used, whereby A3C was able to solve all scenarios and achieve generalization. In addition, A3C could solve these scenarios with fewer actions than the baseline automated penetration testing. Although the training was performed on rather small scenarios and with small state and action spaces for the agents, the results show that a penetration test can successfully be performed by the RL agent.
GNN-based Anomaly Detection for Encoded Network Traffic
May 22, 2024Abstract:The early research report explores the possibility of using Graph Neural Networks (GNNs) for anomaly detection in internet traffic data enriched with information. While recent studies have made significant progress in using GNNs for anomaly detection in finance, multivariate time-series, and biochemistry domains, there is limited research in the context of network flow data. In this report, we explore the idea that leverages information-enriched features extracted from network flow packet data to improve the performance of GNN in anomaly detection. The idea is to utilize feature encoding (binary, numerical, and string) to capture the relationships between the network components, allowing the GNN to learn latent relationships and better identify anomalies.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge